Alka ransomware is the cryptovirus that encrypts files and corrupts the system settings in several attack stages
 Alka ransomware – malware that extorts a particular fee for the alleged decryption tool that should help to unlock encoded files marked using .alka extension. It is a version of the DJVU virus that is releasing a new version after version and not stopping for three years now. Previously, some of the versions were decryptable, and people got their files back with the help of STOPDecrypter.exe file and the tool that researchers developed based on offline keys. After August 2019, malicious actors who develop this virus started to use proper encryption methods and rely on online keys. This fact made it worse for all the victims all over the world because when each victim gets the unique ID, decryption is only possible with that particular key. In some cases, when IDs end in t1, they can be used to restore at least some of the files because, with offline keys, encryption codes are easier to break.
Alka ransomware – malware that extorts a particular fee for the alleged decryption tool that should help to unlock encoded files marked using .alka extension. It is a version of the DJVU virus that is releasing a new version after version and not stopping for three years now. Previously, some of the versions were decryptable, and people got their files back with the help of STOPDecrypter.exe file and the tool that researchers developed based on offline keys. After August 2019, malicious actors who develop this virus started to use proper encryption methods and rely on online keys. This fact made it worse for all the victims all over the world because when each victim gets the unique ID, decryption is only possible with that particular key. In some cases, when IDs end in t1, they can be used to restore at least some of the files because, with offline keys, encryption codes are easier to break.
Since Alka ransomware virus mainly uses online IDs, as other versions released in the past six months, f.e Repp dropped around the same time, there are fewer options left for victims. Tools, that researchers have, only work with offline IDs that can be used for many victims at the time. The other option is paying the ransom, but experts[1] rarely state that it is safe, especially when it comes to such large cryptovirus families. Since decryption is not easy, it is better to focus on terminating the malware and recovering the machine using other options – thrid party data restoring applications and anti-malware tools.
| Name | Alka ransomware |
|---|---|
| Family | This is a threat belonging to the STOP virus family. The 204th version of the Djvu ransomware |
| File marker | .alka is the appendix that indicates all the data affected during the encryption. This marker gets added at the end of the original name after the file type extension |
| Ransom note | _readme.txt – the file that gets placed in folders where encrypted data is and on the desktop where people can find the message as soon as possible |
| Amount of ransom demanded | It starts at $980, but actors try to fake the trust and offer a discount of 50% for people who contact criminals in the first 72 hours, which makes the ransom $490 in the form of Bitcoin. |
| Contact emails | [email protected], [email protected] |
| Distinct features | The malware injects AZORult trojan on the system as a secondary payload that can steal various information; it alters hosts files so the victim cannot access security software providers, sites like this one; malware shows a fake Windows OS update window during the encryption, so the victim is not paying attention to the slowness and disturbance of the performance |
| Distribution | It is known that one of the more unique ways of how this family injects products on the machines involves pirated software and torrent sites because software cracks,[2] licensed keys, game cheats and other files like that include malicious script which triggers ransomware infection |
| Elimination | Alka ransomware removal is a process that requires additional help and advanced knowledge since it involves a few types of malware, possibly, and system alterations. So the best way os to get the anti-malware program and scan the computer for thorough cleaning |
| Decryption options | Files affected by the Alka version cannot get easily decrypted unless the victims’ ID ends in t1 what indicates the offline key used for encryption. If so, Emsisoft has a tool that may help. Otherwise, the official decryption tool is not available, so you may need third-party options for recovery |
| Repair | You still need to clean the machine and fix the damage that virus leaves on the system, so get PC repair program or an optimizer like Reimage Reimage Cleaner and find affected parts of your device and possibly fix them without causing additional issues |
Alka ransomware is not targeting particular countries, so anyone and anywhere can get affected by this threat and suffer the loss of data or even money if they decide to pay the creators. The encryption that ransomware is based on changes original code of data like images, documents, audio, video files. This process also affects databases and archives, but system files and folders get interfered too, just not during the encryption.
Alka ransomware and Djvu versions, in general, are known for displaying the fake Windows update program window that states about a running process, so people believe that slowness of the system is caused by this, not anything else. During this time, encryption and all the other changes takes place. When files get the .alka marker, they already are unreadable and cannot be used, so the ransom is demanded in _readme.txt file.
However, the attack is not ending here. To ensure that victims cannot easily recover after the infection and that there are fewer options for Alka ransomware removal, virus developers focus on disabling particular security tools and functions. Since your AV software is possibly blocked, you need to enter the Safe Mode with Networking or use another method that allows performing the system check.
Unfortunately, it becomes difficult to remove Alka ransomware and to restore files after these registry and system file alterations. When startup preferences get changed, ransomware is launched newly over and over, and all the processes of disabling and blocking programs continue. The virus can install files, applications, and other malware, so the machine gets even more damaged over time.
You should clean the system as soon as possible to avoid permanent and unrepairable Alka ransomware virus damage. However, you may fix such issues with system tools like Reimage Reimage Cleaner since such a program can find affected system files and repair them without damaging other processes. 
Alka ransomware is the cryptovirus that demands money from victims when their commonly used files get encrypted. Don’t fall for the discount offers and test decryption opportunities.
Alka ransomware file encryption and recovery
Alka ransomware starts with encryption as soon as the payload file lands on the machine. Malware uses a powerful algorithm that allows finding the most commonly used and valuable files. Then the virus can change those personal files and demand payment for the recovery.
It happens first because actors focus on locking data and demanding payments from victims. The ransom demanding file _readme.txt also gets placed on the system as soon as possible. The ransom note delivers the same message that has been distributed since 2016:
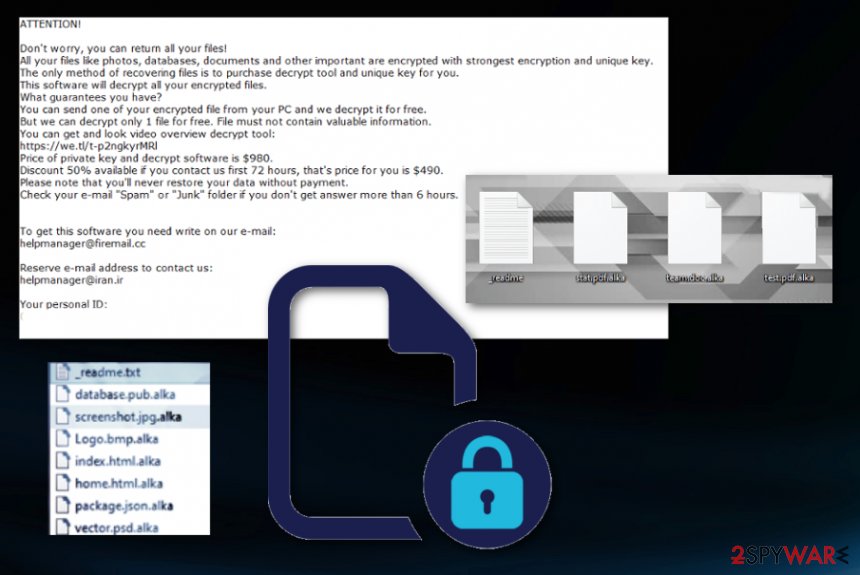
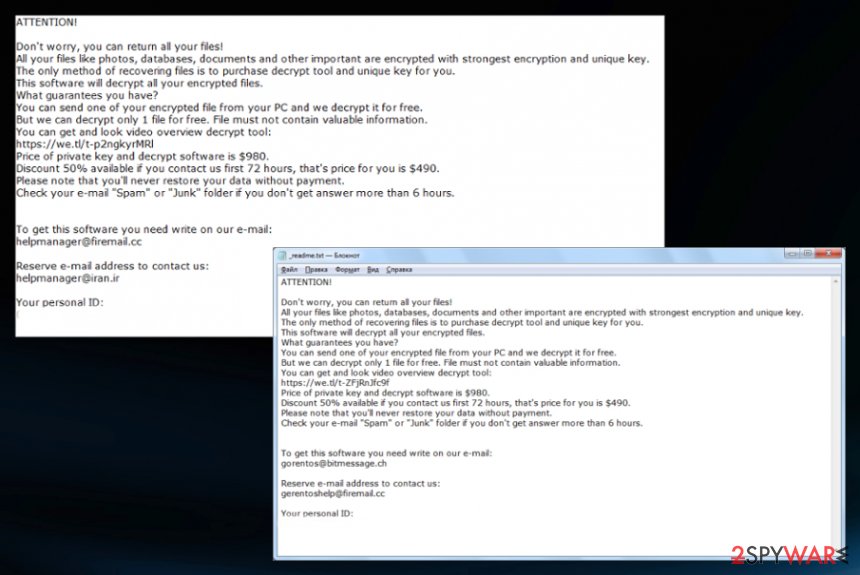
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-7YSRbcuaMa
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]Your personal ID:
Additional changes that Alka ransomware makes, happens after the encryption and cannot be easily noticed because of that. The blackmailing message distracts victims from any other activities, and malware can run uninterrupted while people decide to pay or not. This is not the solution for such malware, and researchers note that people shouldn’t even contact criminals in such instances.
This is probably the reason why developers keep releasing version after version and blocking such sites like security software providers, malware researchers’ blogs, and so on. Victims cannot get too much information about the infection and decides to pay. When it comes to recovery after Alka ransomware infection, it is important to note that some facts can determine how easy it is to get your files back:
- we already mentioned that offline vs. online keys get used by these malware creators and since Alka ransomware is one of the newer versions it mostly relies on online victim IDs, making the decryption merely impossible;
- if you know that offline key got used in the particular attack on your machine, you can rely on decryption tool and researchers;
- additional options could be Data Recovery Pro and Windows Previous Versions that can be found at the bottom of this guide.
Alka ransomware is called like that because it focuses on ransom-demanding messages and getting money for alleged decryption keys. In most cases, people don’t receive their decryption tools, so DO NOT pay.
Deceptive techniques enable hackers to spread malicious code on a large scale
It is common to get an infection like ransomware or trojan from spam email attachments, hacked sites, malicious pages, and insecure software installations involved in pirating services. Many opportunities allow hackers to spread quickly and even deliver other threats on the infected machine.[3]
In most cases, this threat comes unnoticed because the victim opens the email attachment without paying close attention or installs a package from sharing services where pirated or even malicious files get included. Spam email can have links on the notification that directly reroutes users to malware-dropping service, so you only need to click on a dangerous content once to get infected. This is a very dangerous threat that starts working immediately. Remember:
- pirating software, getting game cheats and other cracks of applications are not only illegal but highly dangerous activities;
- spam emails that are sent from questionable sources, unknown companies, services, and commercial providers should be taken into consideration before opening;
- don’t download random MS documents and other files on the machine from emails or websites you are not sure of.
Make the system clean from Alka files virus traces
Even though Alka ransomware virus is focusing on encryption and ransom demands, that doesn’t mean other parts of the device are affected. The infected system is vulnerable to infections, and especially when threats besides the cryptovirus get installed, the cleaning process is crucial.
Alka ransomware removal is significantly affected by all the alterations in the system folders, Windows registry, and other parts that control functions and programs running on the computer. Although anti-malware tools are the ones that should help the best, you may need to reboot the machine in Safe Mode additionally.
To remove Alka ransomware, get SpyHunter 5Combo Cleaner or Malwarebytes and run it on the system. Follow all the steps that the program suggests and remember to double-check before proceeding with file repair options. If you add your data backups on the system that still has virus traces, you may lose all your files. Fix system damage using Reimage Reimage Cleaner and then go through recovery option suggestions below.
Remove Alka using Safe Mode with Networking
Reboot the machine in Safe Mode with Networking and remove the Alka ransomware with AV tools then
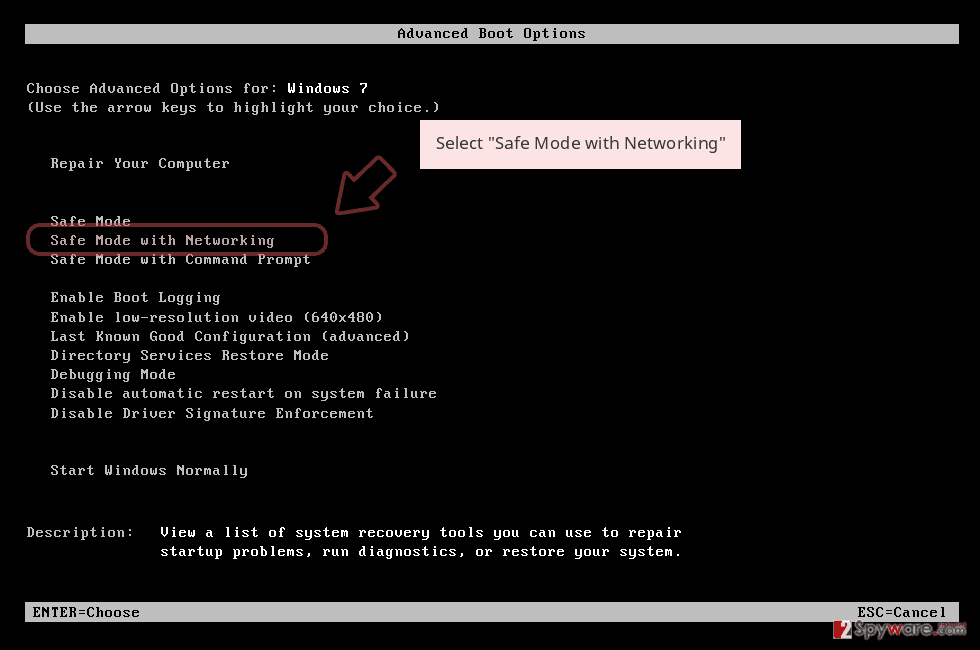
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
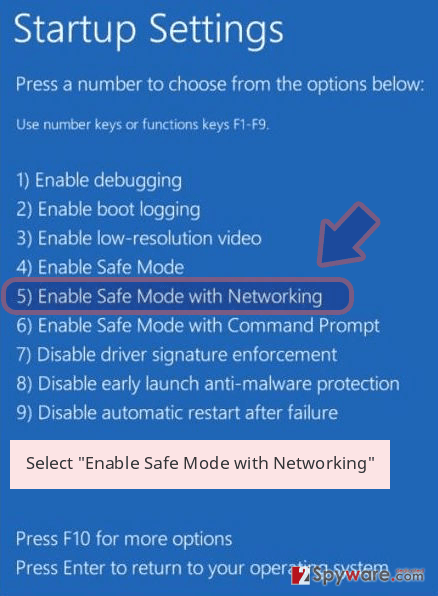
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Alka removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove Alka using System Restore
System Restore is a feature worth trying because it allows the user to recover the machine in a previous state when the virus was not active
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Alka from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by Alka, you can use several methods to restore them:
Data Recovery Pro is the program that can possibly be used for file restoring
When Alka ransomware encrypts your files, but you don’t have a particular data backups, Data Recovery Pro can restore then for you. It also helps for accidentally deleted data
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Alka ransomware;
- Restore them.
Windows Previous Versions feature restores individual files that get affected by the malware
When System Restore gets enabled, Windows Previous Versions can be the solution for affected data
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer method for encrypted files
If Alka ransomware is not affecting Shadow Volume Copies, ShadowExplorer can be used as an alternative method for data repair
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption tool for Alka ransomware is not developed, but there are a few options
When offline IDs get used for locking files, Emsisoft can offer the DJVU decryption tool that can repair encoded data
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Alka and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-02-03 at 07:18 and is filed under Ransomware, Viruses.

