Calum ransomware – a Phobos family member that appends the .Calum extension to each locked component and demands a BTC ransom
Calum virus – ransomware that encrypts files and demands money in exchange for the decryption software
Calum ransomware is one of the newest versions belonging to Phobos ransomware. The purpose of this malware is to target English speakers, infiltrate their Windows machines, and scan the system for encryptable documents/files. Once the malicious program detects all files that can be locked, it executes a symmetric[1] or asymmetric algorithm that blocks the data and appends the .Calum extension to each affected component. Furthermore, Calum virus drops the info.hta and info.txt ransom notes that bring ransom demands which have to be met, otherwise, the victims will not be able to recover their data. The criminals try to scare people by claiming that no other tool will help and encourage victims to write them via [email protected] or [email protected] email addresses and also obtain Bitcoin cryptocurrency for the ransom payment.
| Name | Calum ransomware |
|---|---|
| Type | Ransomware infection/file-encrypting malware/ransom-demanding virus |
| Appendix | Once the malware places itself on the Windows computer system and uses symmetric or asymmetric encryption to lock up data, the affected components end up with the .Calum extension added |
| Ransom note(s) | The ransomware virus places info.hta and info.txt ransom demanded messages on the desktop and also a copy in each folder that includes locked documents and files |
| Demanded price | Even though there is no current ransom price number given, hackers are likely to demand an amount between $100 and $2000 that needs to be transferred in BTC or another type of cryptocurrency |
| Email addresses | The criminals provide [email protected] or [email protected] email addresses as a way to make communication with them |
| Distribution | Ransomware infections, including Calum virus, are most commonly distributed via email spam, software cracks, vulnerable RDP, infectious ads/links, and other similar locations |
| Family | Phobos ransomware |
| Removal | You need to get rid of the infection ASAP. Perform the process only automatically to avoid possible mistakes and damage |
| System repair | If the malware has touched some system components on your Windows computer machine, try repairing them with the help of Reimage Reimage Cleaner software |
Calum ransomware brings more than just file encryption and inadequate ransom demands. This malicious string might modify some Windows Registry entries and inject hazardous processes in your Task Manager section once entering your Windows machine. This way the cyber threat will be assured that it will reboot and reload itself each time when the user turns on his/her computer system.
Continuously, such alterings might allow Calum ransomware to run a system scanning process once in a while and go in search of newly-encryptable documents and files. Also, the malware might try to avoid antivirus detection by running specific commands, destroy Shadow Copies[2] of locked data, or damage the hosts file in order to prevent users from accessing cybersecurity-related web pages where they might find reliable information towards Calum ransomware removal.
Our recommendation would be not to fall for the tricks that Calum ransomware might try to put on you as there might be some better solutions than paying the criminals. Besides, you always risk losing your money for nothing while paying hackers as these people might appear to be only scammers. Even though the ransom note claims that the decryption tool will be provided after the ransom payment, this type of data might be completely false:
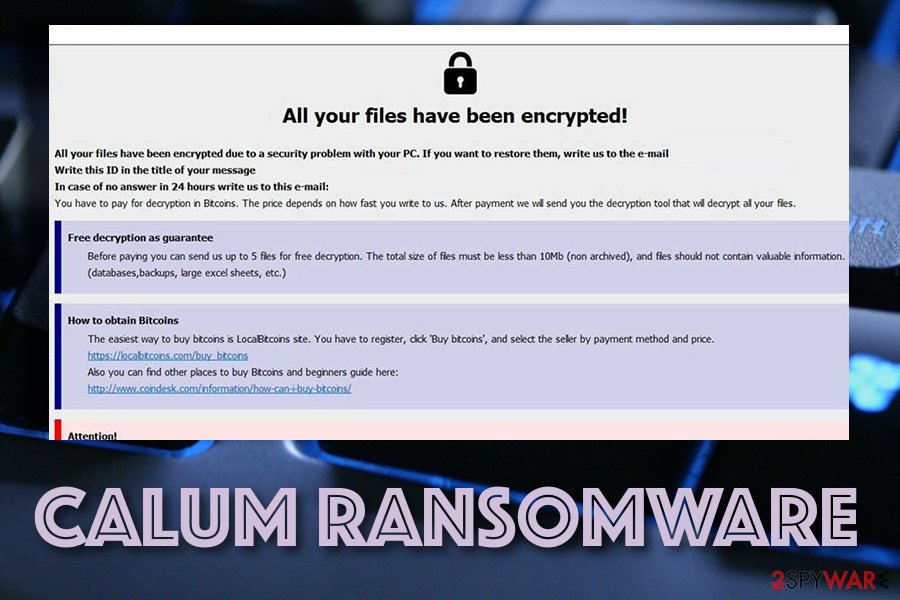
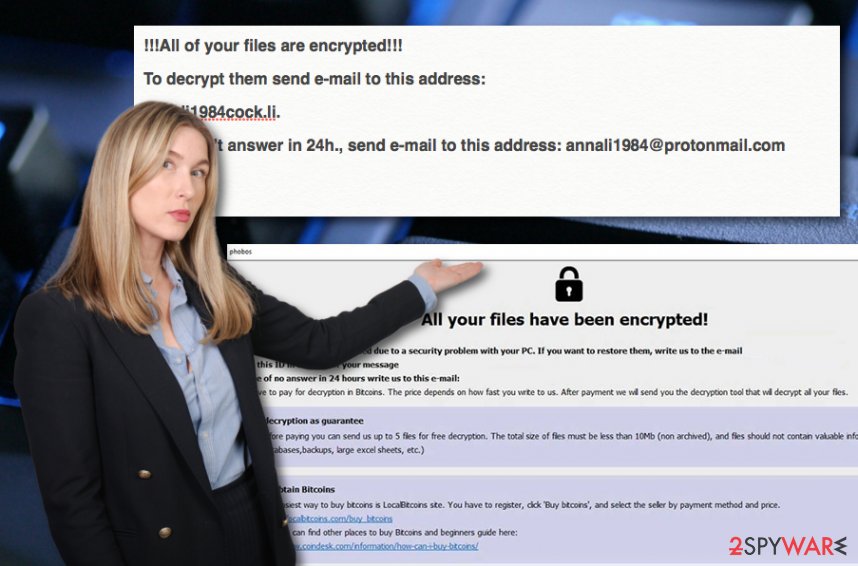
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID in the title of your message –
In case of no answer in 24 hours write us to this e-mail:[email protected]
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 4Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
hxxps://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Calum ransomware might tend to carry additional malware into the system. There are a lot of ransomware strains that come attached with a Trojan horse as this way the developers can double their benefits. If you postpone the elimination process of the ransomware virus, you might not even notice that additional malware has been added to your computer system before it is too late.
If you are looking for a way to remove Calum ransomware, we recommend employing only reliable antimalware software as manual elimination is not a good possibility in this case. After the cyber threat leaves your computer, you can try repairing damaged files with Reimage Reimage Cleaner . Also, go down to the end of this article and read through all of the data recovery methods some of which might let you bring your data back to primary state.
The content of Calum ransomware has also been included in the database of VirusTotal website.[3] We have found that 53 out of 69 AV engines are able to detect the malware-laden files. Some of the detection names include Win32:Malware-gen, TR/Crypt.XPACK.Gen, Trojan.Ransom.Phobos.F, Trojan.Ransom.Phobos.F (B), Ransom.Phobos, Ransom:Win32/Phoenix.BW, etc.
Calum ransomware – a dangerous malware that can be distributed via software cracks, email spam, vulnerable RDP, and other techniques
Ransomware appearance is a common thing in the cybersecurity field
Regarding the latest news reports by security researchers, ransomware infections are commonly distributed on random user computers and also have been targetting reputable healthcare firms, banking organizations, and so on. These notorious viruses might result in the loss of important information or money if the victim agrees to pay and inadequate price in order to receive the decryption tool.
Calum ransomware is just a small fish in the ocean regarding the thousands of other ransomware viruses released. However, every infection is dangerous, should be avoided and removed if injected into someone’s computer system. Besides from Phobos releasing new versions fastly, Djvu ransomware also does not fall behind. The developers have already let out around 200 versions that belong to this malware category.
Multiple techniques are used for ransomware distribution daily
Security specialists from ZonderVirus.nl[4] state that hackers think of numerous ways how to distribute their products for a wider range of people. Ransomware viruses are one of the most dangerous infections that lean on spreading techniques such as email spam, software cracks, malicious updates, infected files/ads/links, exploit kits, vulnerable RDP, etc.
One of the most popular spreading ways is through email spam campaigns where cybercriminals pretend to be from reliable shipping companies such as FedEx or DHL and tend to deliver “shipment information” or “order confirmation” via a hyperlink or attachment that truly is the infectious payload.
Furthermore, ransomware is also commonly distributed via software cracks that can be found on unsecured downloading sources and p2p networks such as The Pirate Bay. Get all of your products and services only from reputable developers and originals websites, otherwise, you might easily end up with malware on your computer system.
Continuously, vulnerable RDP protection such as including a weak password or none security code at all might also allow crooks to hack the RDP remotely, brute force the password into the system, or just connect remotely without putting any big effort into the process. Make sure that you always use strong and reliable passwords that include not only letters or just numbers but both of them combined together and even some symbols added.
The termination process of Calum ransomware (Phobos variant)
Phobos seems to be including various versions of ransomware into its family line and Calum ransomware is one of them. If you ever encounter this malicious infection on your Windows computer system, you should not let it stay there for long as many damaging actions might be performed during then.
We always recommend using automatical software for succeeding in processes such as Calum ransomware removal as manual elimination might bring more damage to the infected system if completed wrong. First, scan the system with antivirus software such as SpyHunter 5Combo Cleaner or Malwarebytes.
After you remove Calum ransomware, you can try employing Reimage Reimage Cleaner which might help you to repair the corrupted files that have been touched by the malware. Also, below you will find some data recovery methods that might be helpful if you are looking forward to recovering some locked files.
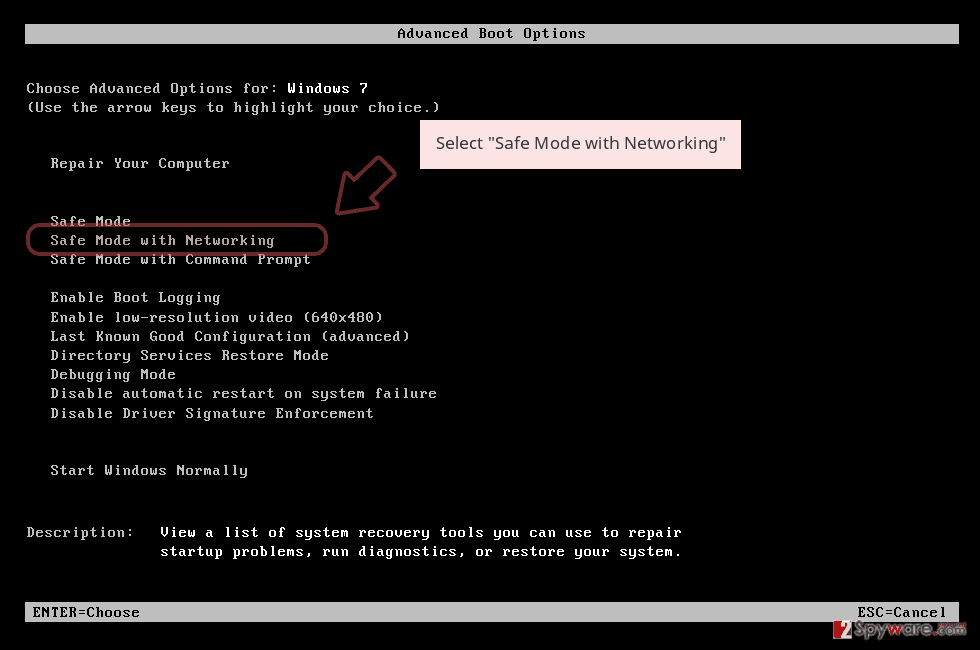
Remove Calum using Safe Mode with Networking
If the ransomware virus has initiated some malicious processes on your Windows computer system, you can try to disable the operations by booting your machine in Safe Mode with Networking:
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
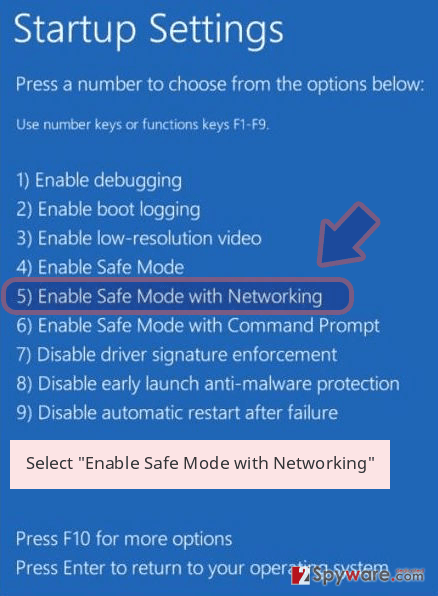
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Calum removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove Calum using System Restore
If you have been looking for ways to stop malicious tasks from running on your computer, you can try booting up via System Restore. To do that, follow these guidelines:
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Calum from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by Calum, you can use several methods to restore them:
Employ Data Recovery Pro for file restoring purposes.
Use this piece of software if you have been looking for a tool to unlock your data with. Even though there is no 100% guarantee that the program will work, it is definitely better trying this product than paying the big ransom.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Calum ransomware;
- Restore them.
Use Windows Previous Versions feature for data recovery tasks.
Employ this type of feature to reverse some files back to their previous states. However, just ensure that you have activated System Restore in the past, otherwise, this tool might not work properly.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try activating Shadow Explorer and restore some data.
If the ransomware infection did not permanently eliminate or damage the Shadow Volume Copies of your locked files, you can give this piece of software a try.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, cybersecurity experts are still working on the official Calum ransomware decryption tool.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Calum and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2019-11-26 at 10:37 and is filed under Ransomware, Viruses.

