Cerberus virus is the memory-resident Android trojan that can fully control the device and steal financial data
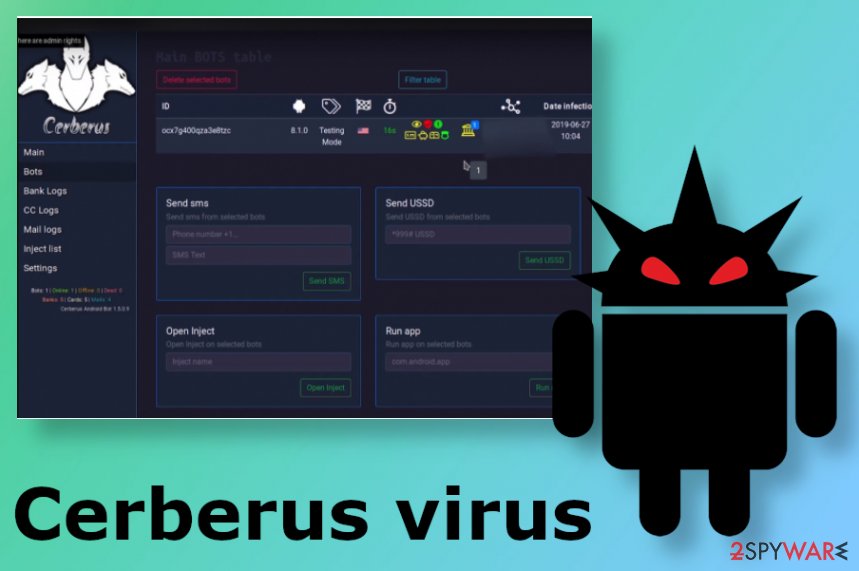

Cerberus virus – a threat that criminals use for accessing mobile phones and taking actions remotely without any indication for the user. This banking trojan[1] relies on the accelerometer sensor to delay the launch on the system, so security researchers’ analysis can be evaded. This malware recently started to act as a malware-as-a-service business. According to creators, it is used privately for the past few years since they created the malware from scratch. This trojan can be rented or bought on hacker forums as a tool for stealing credentials and sensitive information. The threat can easily be used to send commands to the victims’ devices and perform needed actions.
This sneaky Cerberus malware can be disguised as common applications, installs of FlashPlayer, or some service. Such methods are used to deceive users into providing privileges through the Accessibility Service because once these privileges are granted, the malware can connect to a botnet and receive commands from the C&C server.
Once that is done Cerberus becomes a tool for controlling the phone calls, SMS messages, processes, and accessing other valuable information. It is known that trojan can bypass the Google Authenticator and use advanced mechanisms to enter devices, so it can steal banking credentials and passwords or payment information on any Android device. It acts as a Remote Acess Trojan, so there are many commands that criminals who use it can launch on targeted devices, so it may lead to serious hacker attacks and even crucial damage or data loss.
| Name | Cerberus virus |
|---|---|
| Type | Android malware/ banking trojan |
| Danger | The threat can access valuable information, steal it, and use that data in later scams, targeted attacks, or even sell details to other criminals. Once the RAT is on the device it can control various processes and trigger actions[2] |
| Symptoms | A trojan is not causing many issues on its own, but the system gets slow and can crash due to background processes. Applications and functions cannot run normally when malware controls the behavior and modifies various parts of the device without permission |
| Possible actions | Controlling messages and calls, stealing information, making screenshots, changing functions and program behavior can all be features of the malware, depending on the aims of the particular criminals who use the tool |
| Distribution | Malware like this can spread via malicious or hacked sites, email attachments with direct malicious script injected or scam websites, deceptive pop-ups and applications |
| Elimination | To remove Cerberus virus, you should run the proper anti-malware tool, so all the issues are no longer bothering you when the malware is terminated alongside all the associated files and programs. You can find AV tools designed for various operating systems, so the virus can be removed easily from any device |
| Repair | Trojans can affect many functions of the device to get their goals achieved, so there are many issues with the device left, even when the virus is cleared. You should run the PC repair or optimization tool like Reimage Reimage Cleaner Intego to find affected or even damaged files and system functions |
Cerberus virus can unlock the phone remotely and get into the camera, microphone, and track your behavior for a long time until anything suspicious can be noticed. Trojan uses the mechanism that determines if the device is moving or not. It is achieved by reading the information from the accelerometer sensor that is on all Android devices and measures the force on all the physical axes.
By launching the pedometer, Cerberus virus tracks if the victim is moving, and when the person moves around the motion data is generated and triggers the step counter. Once the trojan is active it starts communicating with the C&C server when the particular number of steps is reached. Such a function is designed to avoid running on test devices or in sandbox environments and other machines used for malware analysis.
Cerberus virus is acting mainly as a typical banking trojan, so it gets executed on the system and hides the malware as the icon of a shady application like Flash Player. It asks for increased privileges through the Accessibility Service to avoid getting detected and removed from the machine.
It is not much advanced and all the features are pretty standard, so malware can send messages, open injected programs or run existing applications, send other commands and record calls, audio messages, take screenshots or directly steal data from conversations and the system itself. Since the Cerberus virus is available online it can be used to target anyone and run commands that lead to serious issues and even damage or identity theft, financial losses.
Possible actions that Cerberus virus can take once the authorization is granted:
- total control over messages and phone calls;
- data checks on the device;
- recording of any phone call;
- sending data from the machine to crook’s server;
- password and username gathering;
- taking screenshots;
- stealing audio data;
- locking and unlocking the phone;
- shutting the device off and turning on.
Cerberus trojan functions as a malware that can also reboot the device if needed and access characteristics that the original client can launch. It takes complete control of the device, and the victim may not even notice anything suspicious. Criminals who take this tool in their hands can also choose to add various information on the machine or steal anything from the databases. 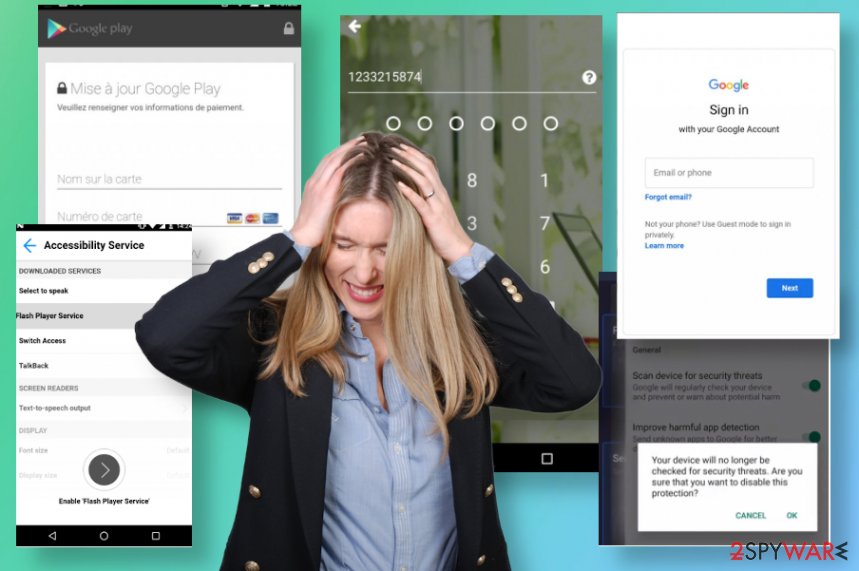
Cerberus virus is the trojan that spreads on Android OS and aims to steal banking information, so payments may be gathered directly from victims.

Cerberus virus is the trojan that spreads on Android OS and aims to steal banking information, so payments may be gathered directly from victims.
Cerberus virus is dangerous firstly because of the information that it can obtain. Confidential data and sensitive credentials, banking information gets stolen when victims enter those details on various sites, and stealer collects all the keystrokes. Overlays and other data grabber methods get used to stealing these credentials and later on attacks can be launched.
There are some reports that the Cerberus virus is aiming to perform overlay attacks using banking applications and other programs launching on Android devices in France, U.S, and Japan. This malware came out with some of the campaigns involving malicious and deceptive websites that focus on the pandemic situation during the spring of 2020.
If you visit coronavirus-information.online or canada-alert-covid19.com, at least once you may need to remove Cerberus virus because some pop-ups and other additional windows trigger the drop of the malicious script that launches the trojan. Other sites with fake alerts about downloads or updates also trigger payload installation instead of browser or software updates.
Various cryptovirus sites and pages that pose as legitimate Bitcoin wallet services can spread and promote Cerberus virus or any other threat that causes serious issues ranging from data-stealing to direct damage. As we mentioned, the drop of the payload may happen significantly earlier than you notice any symptoms or suspicious behavior. Unfortunately, there is a long list of applications that banking trojan targets:
- Bank of America Mobile Banking
- Capital One® Mobile
- Chase Mobile
- Connect for Hotmail
- Gmail
- ING
- Mail (Android)
- Microsoft Outlook
- Snapchat
- Telegram
- U.S. Bank – Inspired by customers
- Uber
- Viber
- Yahoo Mail – Organized Email
This list expands each week, so pretty much anyone that uses Android devices can become a victim of the trojan that uses overlays and gathers information from private conversations and the device in general. You need to react to these risks and run anti-malware tools that can detect[3] the trojan and possibly perform the Cerberus virus removal.
If you get indicated that Cerberus trojan is on the machine do not wait and clean all the threats that the AV engine shows you on the list after a full system scan. Once you remove the malicious applications, you may additionally download Reimage Reimage Cleaner Intego or a similar repair/ optimization tool so damaged files or corrupted functions gat be fixed automatically. 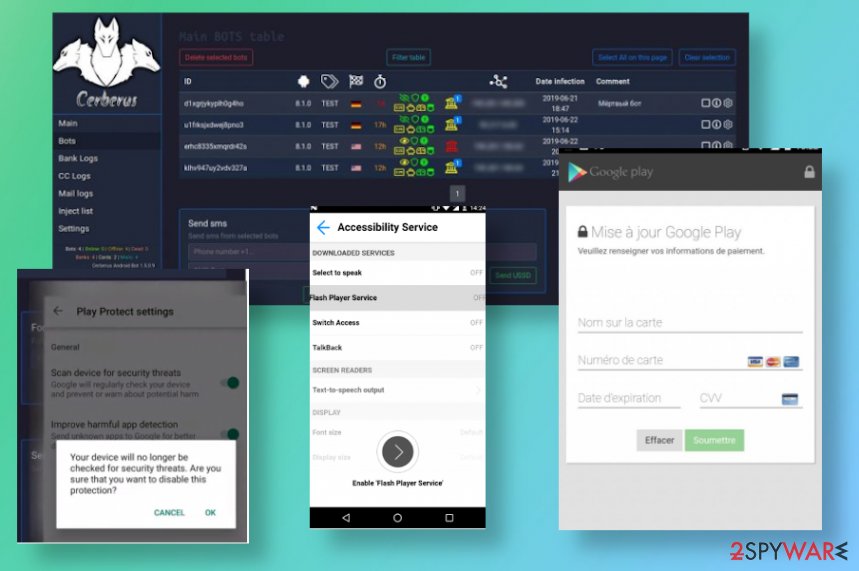
Cerberus virus is the banking malware that controls various processes on the affected device and can steal passwords, logins, data stored on the machine directly.

Cerberus virus is the banking malware that controls various processes on the affected device and can steal passwords, logins, data stored on the machine directly.
Criminals recreate the download and installation of primary applications to infect the machine
Crooks include the malicious scripts in the code of applications and re-uploads the application along with the uploads from third-party sites or malicious pages posing as official versions of download sites and software providers or update pages. These pages can replicate and produce many domains delivering the same harmful apps and redirecting to additional downloads of similar applications.
Social media spam messages can also promote these links and apps. Once the malicious app lands on the device, it may connect to other servers and act as a downloader, so devices get infected with a trojan or different malware. These threats can also get downloaded as malicious documents via spam email campaigns when notifications resemble emails from legitimate companies or services.
Standart Android security policies shouldn’t allow installations of applications from untrusted sites, so users may opt-out of such settings and allow various third-party downloads. This is how malware can enter the system though, so experts[4] do not recommend doing so. Be careful when verifying any requirements and do not give shady apps inadequate permissions.
The guide to clearing machine from Cerberus banking trojan
Cerberus virus is the Android OS-based malware that affects mobile devices, so you should take that into consideration and make sure to take some additional actions before starting actual procedures of malware elimination. Firstly, turn off the device until you know how bad the infection has gotten. You can win some time this way.
You can also start the Cerberus virus removal process with entering the Safe Mode on Android OS:
- Turn the device and hold the power button until you see the menu with choices.
- Tap on Safe Mode and enter the system. You will be on airplane mode, so the virus is no longer connecting to remote control servers and hackers in general.
- If you know which application is triggering the malware, you can possibly remove the program via settings and the control center. More solutions for system resetting, in the article about general Android virus infections.
Of course, there are many other things that you need to delete if you want to remove Cerberus virus completely from the machine. There might be some hidden files and threats loaded on the system, so rely on tools compatible with your operating system or security software like SpyHunter 5Combo Cleaner or Malwarebytes. Running AV detection-based programs can indicate various threats, so you need to clear them all off of the machine.
This entry was posted on 2020-05-05 at 06:06 and is filed under Trojans, Viruses.

