New iPhone exploit discovered: Chinese hackers spy on Uyghur Muslims in the autonomous region of Xinjiang
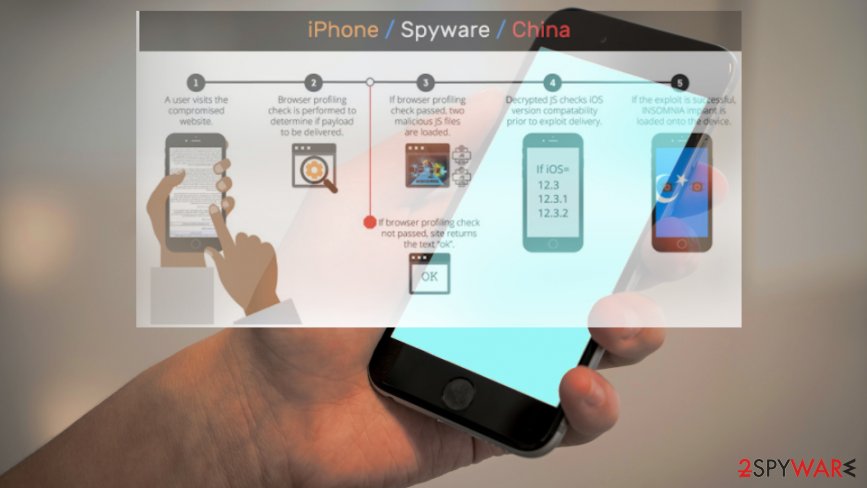

The digital forensic team reveals that new iOS exploit named Insomnia uses a flaw in WebKit browser engine to spy on China’s Uyghur minority.[1] The exploit works on iOS versions 12.3, 12.3.1, and 12.3.2 and leverages on the previously known flaw that was patched last year with iOS 12.4 version.[2] Insomnia was used between January and March 2020 when the exploit was loaded on the devices of users that visited Uyghur-themed websites.
The exploit was launched when the victim accessed the site, and attackers gained root access to the device immediately. Once that was done, hackers managed to steal plaintext messages from various instant messaging applications, emails, photos, contacts, and even track GPS location details. Insomnia works with various browsers that are based on WebKit and anyone that visited websites with Insomnia scripts were vulnerable to getting hacked, as Volexity reports:
Note that exploit can be triggered through any browser on the phone, as they all use WebKit. Volexity was able to confirm successful explotiation of a phone running 12.3.1 via the Apple Safari, Google Chrome, and Microsoft Edge mobile browsers.
Insomnia used by Evil Eye hacker group
Researchers reported that the exploit was used by a group that they are tracking with the name of Evil Eye. These hackers supposedly are a state-sponsored group operating from Beijing and particularly spying on the Uyghur Muslim minority in China’s autonomous region of Xinjiang.
According to previous reports, this group targets the Uyghur minority since 2016, and at least 14 exploits with similar techniques were already deployed.[3] Once the Google report on these iOS exploits got published, Evil Eye shut down their network and stopped using those older exploit tools.
Back then, actors removed malicious code from compromised pages and took down the command-and-control servers. January 2020 was the time when the hacker group came back by releasing this Insomnia exploit targeting the same Muslim minority with new watering hole attacks.[4] Researchers noticed activities on previously affected Uyghur websites and decided to dig further to reveal the exploit campaign.
Spyware targets open-source browsers and ProtonMail, Signal applications
The Safari and Google Chrome are the browsers based on open-source browser engine WebKit. The vulnerability that was exploited allowed hackers to compromise six different websites. The one that was visited the most is akademiye.org that is the website of Uyghur Academy.
Previous exploits targeted details like GPS coordinates, photos from the iOS Photos app and address book, contacts application.[5] After the Volexity report, the Insomnia exploit also expanded the target to emails from the ProtonMail app and images sent via Signal messaging application.
The inclusion of Signal and ProtonMail may suggest that the Uyghurs are aware of potential monitoring of their communications and are attempting to use applications with strong security features to avoid this.
Fortunately, Insomnia as previous exploit kits doesn’t have the boot persistence feature, so rebooting the phone removes the exploit kit entirely from the device. However, Evil Eye hackers are advanced enough to put the persistence up if they want to. The better protection solution is to update devices to the iOS 12.4 version that includes the recent patch for the WebKit flaw.
