Cloudnet virus is a threat that runs questionable processes in the background and causes high CPU and GPU usage


Cloudnet virus is a miner malware that creates cryptocurrency by running on infected devices’ resources. This behavior causes lots of frustration for the user because this process slowdowns the machine and keeps the victim from using the PC normally.[1] The virus runs Cloudnet.exe process in the background, which is located in a subfolder of the user’s profile folder, allowing it to perform its malicious activities. Additionally, because the virus is usually transferred with the help of other malicious applications, the possibility of the system being infected with such hazards as ransomware, backdoors, keyloggers, and similar threats is quite high.
Cloudnet is a type of malware that belongs to the Trojan[2] category. Created by Epic Net Inc., it was bugging users since early 2017, and multiple anti-virus engines are still reporting infections all over the world. The threat is usually injected via the dropper malware already present on the system or is downloaded by users from malicious websites. Once installed, the malicious Cloudnet virus compromises system security by performing a variety of changes to it. It connects to a remote server controlled by hackers who can remotely send and receive information, which puts sensitive data at risk.
| Name | Cloudnet virus |
| Type | Trojan, backdoor, cryptocurrency-miner |
| Rekated process | Cloudnet.exe |
| Alternative names |
|
| Activities | Connects to various IPs and URLs, collects and sends out data, compromises system security |
| Main dangers | Personal data theft, additional malware infection |
| Infiltration | Downloaded from malicious websites, installed by other malware |
| Elimination | Use reputable security software to scan your device in Safe Mode and remove Cloudnet virus |
| Recovery | Use Reimage Reimage Cleaner Intego to restore normal system functions and repair damage done |
Because the malware can compromise system security, experts[3] advise not to delay Cloudnet virus removal. However, the process might be a little complicated, as Trojans are sometimes difficult to detect and remove due to persistence techniques used. Therefore, it is highly recommended entering the safe environment in Windows (Safe Mode) and performing a full scan with anti-virus software.
Once the malicious payload is executed, Cloudnet.exe backdoor performs the following tasks:
- Creates a new path %Application Data%\EpicNet Inc\CloudNet\;
- Creates an executable %Application Data%\EpicNet Inc\CloudNet\cloudnet.exe;
- Creates mutex to ensure one copy of executable is running;
- Adds and modifies Windows Registry to ensure persistence;
- Creates a proxy connection;
- Downloads and executes arbitrary files.
Once system modifications are complete, Cloudnet virus can start its malicious activities. First of all, it sends out a variety of information (OS version, processor name, memory information, malware version, etc.) to a C2[4] server starts redirecting users to dangerous websites and also include users’ emails in advertisement campaigns, which can spam the inbox rather quickly.

Cloudnet virus is a trojan horse that arrives on the system with the help of other malware present on the system or is downloaded from a malicious site

Cloudnet virus is a trojan horse that arrives on the system with the help of other malware present on the system or is downloaded from a malicious site
This malicious trojan runs the Cloudnet.exe CPU miner that creates digital currency without users’ permission. The behavior starts once the malicious program is installed on the device. Unfortunately, the victim at first can only notice slowness or additional application installations and suspicious background processes.
Cloudnet removal requires a thorough system cleaning with the professional anti-malware tool because only a full scan on the device can detect all malware and indicate other issues with the machine that may be caused by the backdoor trojan or additional programs running on your device.
The main purpose of Cloudnet virus is cryptocurrency mining. This type of malware comes second after the ransomware as one of the most dangerous cyber threats for a reason.[5] Trojans gets on the system without the users’ knowledge and runs the needed process for a long time until the victim notices anything.
Cryptocurrency gets generated for the creator or sponsor without any interaction with the victim, so this virus is more harmful to the device it runs on than the user in comparison with ransomware. Using such files like executables or dlls, malware creators can mask their activities on the device and drop additional payloads or malicious programs to devices.
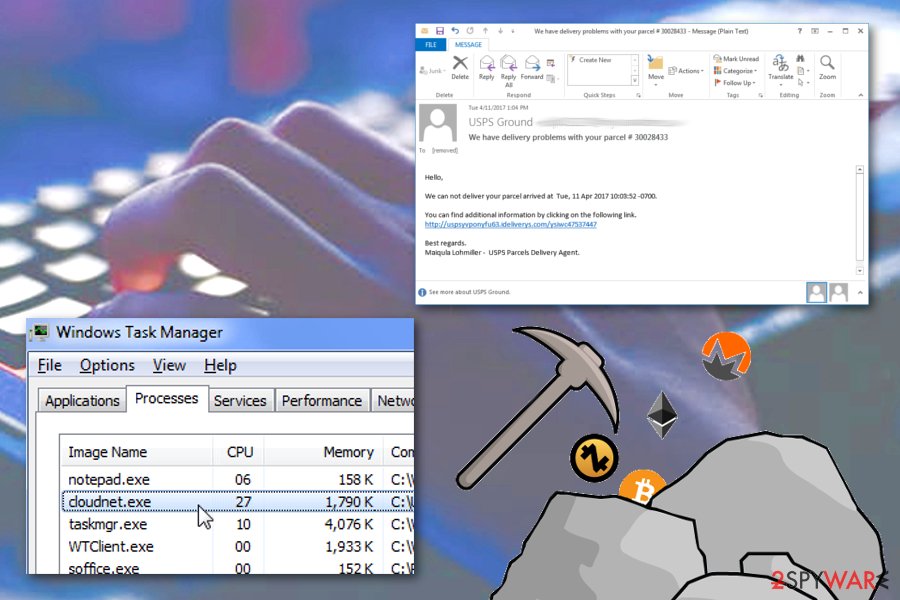
Cloudnet virus is the malware responsible for Cloudnet.exe process that runs in the background and uses CPU and GPU of the users’ machine.

Cloudnet virus is the malware responsible for Cloudnet.exe process that runs in the background and uses CPU and GPU of the users’ machine.
Nevertheless, the uninstallation process of Cloudnet virus is not easier than any other malware removal. There is no particular application that can be removed from the machine manually, so the best option is anti-malware tools and system scans using those programs.
Because malware can modify proxy settings, some users might have troubles when trying to remove Cloudnet.exe virus. Nevertheless, powerful security software should be able to perform the task in the Safe Mode. Please refer to the bottom section of the blog.
Once Cloudnet virus elimination is complete, you should scan your devices with Reimage Reimage Cleaner Intego – it can repair Windows Registry automatically and recover from system damage in just a few minutes. This way you can fox virus damage.
Be careful when surfing the internet – malicious scripts can install malware on your system
Malicious software developers have always been looking for new ways to infect as many users as possible. While the most primitive methods range from hosting malicious links on websites, some sophisticated techniques rely on exploit kits that abuse software vulnerabilities.
While no method would keep you out of trouble 100%, there are several methods that you could decrease the chance of trojan infection by a lot. Some most basic security measures (which most users still fail to implement) include running anti-malware software and timely system updates. However, probably the most important thing is to be attentive while browsing the internet.
Security software cannot and will not protect you from ALL viruses, as new threats are being developed every day, and databases of AV engines and not immediately updated. Therefore, do not browse questionable sites (like a torrent, porn, gambling), do not download pirated software, and use ad-block for your own safety.
Remove Cloudnet virus and prevent further system compromise
If Cloudnet backdoor entered your machine with the help of other malware, your device might be infected with multiple threats. Different malware serves different purposes, however, they do not bring anything beneficial for the victim and can even result in loss of funds, personal files or even identity theft.
Therefore, computer security should not be treated lightly. Talking about this particular threat, you can open Task manager and check if Cloudnet.exe is running. For complete Cloudnet virus removal use Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner, or Malwarebytes and ensure that machine is virus-free. Such tools can also eliminate possible virus damage and corrupted files.
Remove Cloudnet virus with the help of security software. Beware that not all anti-virus applications may recognize the threat, so you might have to use a different program to eliminate malware completely. Besides, if your machine is affected by other malicious threats, AV software should be able getting rid of it all in one scan.
This entry was posted on 2020-06-04 at 11:12 and is filed under Malware, Trojans, Viruses.

