Djvu virus – the most dangerous crypto-extortionist that keeps releasing new versions

Djvu, also known as .djvu files virus, is a crypto-malware variant that belongs to one of the most prominent ransomware families – STOP. The infections started spreading around in December 2018, and the success of the strain encouraged its developers to expand their operation and release sub-variants regularly.
While, initially, it was not much known about Djvu ransomware distribution, researchers spotted that victims let the virus into their systems after downloading and executing the so-called software cracks or keygens. These tools allow users to use the paid software for free, although they are often laden with malware. These cracks and cheats are typically available on torrent sites and remain the main vector for Djvu distribution, especially for last versions .kvag, .karl, .nesa.
The more recent activities and ransomware samples dating to .gero version revealed changes in the virus encryption process and ended with disabling previously known decryption tool STOPDecrypter. However, some versions can be decrypted as noted on this post. In infected, note that numerous expert teams are working really hard on closing the virus, so you can store encrypted files and other data related to the cryptovirus on your computer and wait for the decryption tool.
As soon as Djvu ransomware infects the host machine, it applies a proper AES[1] or another asymmetric encryption algorithm to lock up pictures, videos, music, document, and other files. Users can immediately spot the infection as all their files are appended with .djvus, .djvuu, .uudjvu, .tfunde, and other extensions. To achieve a prompt result, Djvu ransomware modifies various system files and deletes Shadow Volume Copies to prevent recovery.
| Name | Djvu |
|---|---|
| Category | Ransomware |
| Appendixes | .djvu, .djvus, .djvuu, .udjvu, .uudjvu, .djvuq, .djvur, .pdff, .tro, .tfude, .tfudeq, .tfudet, .adobe, .adobee, .blower, .promorad, .promock, .bufas, .dotmap, .sarut, .verasto, .seto, .peta, .karl, .kvag, .nesa and many others |
| Ransom message | _openme.txt, _readme.txt files appear on the desktop after the file encryption process. These ransom notes contain message about the encryption and further details |
| Contact email examples | |
| About the ransom | Crooks offer a 50% discount for the price if the victims contact them in 72 hours. However, this is created to fake trust between criminals and victims |
| System modification | The virus also deletes shadow volume copies, modifies windows registry, starts/stops various processes, creates scheduled tasks, etc. |
| Distribution techniques | Rogue email attachments, cracks, and keygens, adware bundles. In most cases, this ransomware family distributes its versions via torrent sites and services using infected files placed in software crack packages (cracked software, Video games, and so on) |
| Decryptable? |
Some versions are decryptable. Download this tool (direct download link) to check it if your versions is older than .gero. You can find another solution here. The tool described in that post helps when files get encrypted using offline keys. Another alternative decryption option is the service that Dr.Web offers – a tool named Rescue Pack |
| Removal process | Use Reimage Reimage Cleaner or another security tool to get rid of the virus infection. Anti-malware program is required to fight malicious files and fix virus damage completely |
As soon as the encryption process is complete, users are introduced with a ransom note which is usually named _readme.txt or _openme.txt. The message from hackers behind Djvu virus claim that victims have to pay up for the file recovery tool that they would allegedly provide as soon as the payment (as a general rule, $980/$490 in BTC is asked) is processed.
Some of the first Djvu ransomware variants are entirely decryptable with the STOPDecrypter – a decryption tool created by Michael Gillespie. Later variants, however, might not be as easy to crack. Nevertheless, later versions can sometimes be decoded if the encryption process was performed when the malware was unable to contact its C&C server or the host machine was disconnected from the internet. Regardless which Djvu virus version you are affected by, paying the ransom is never recommended, as a possibility of being scammed prevails.
After spreading on the Internet for several weeks, the ransomware came back with the Djvus virus version. It is the same file-encrypting virus which uses unique encryption[2] algorithms to lock up important documents that are found on the infected PC. In this case, the hackers are using the RSA encryption algorithm.
Even though the decryption might be hard to perform even for the highly-experienced users (you cannot guess this key or find it on the Internet), there is no need of rushing to pay the criminals. Note that, these people often try to scam their victims by providing them false promises. We suggest taking a look at some data recovery methods that we have provided below this article.
No matter which virus version you are dealing with, the ransom warning stays the same. As you can see from the message body, no particular details about the money are given in the ransom note. However, victims have reported that they were asked to pay from $350 to $500 for the decryption of encrypted data:
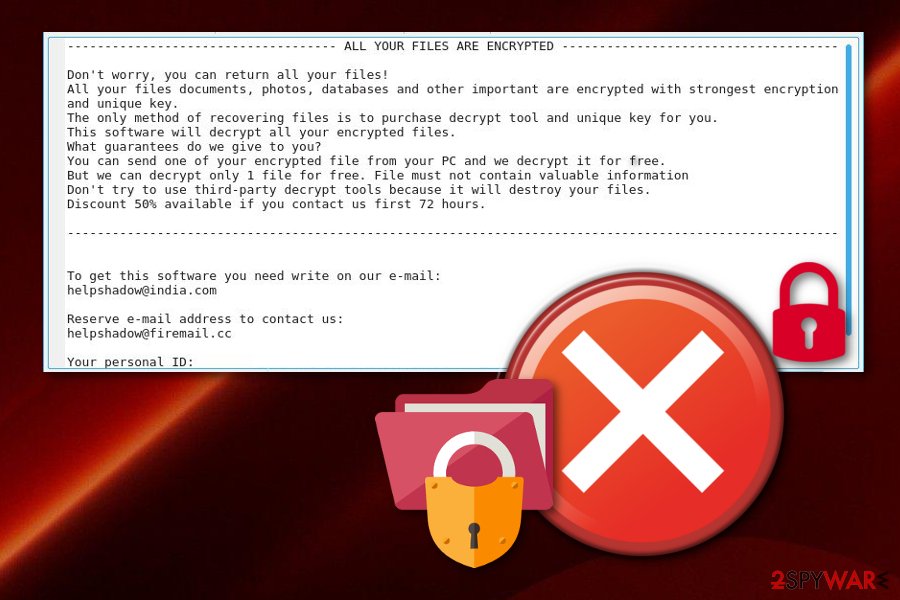
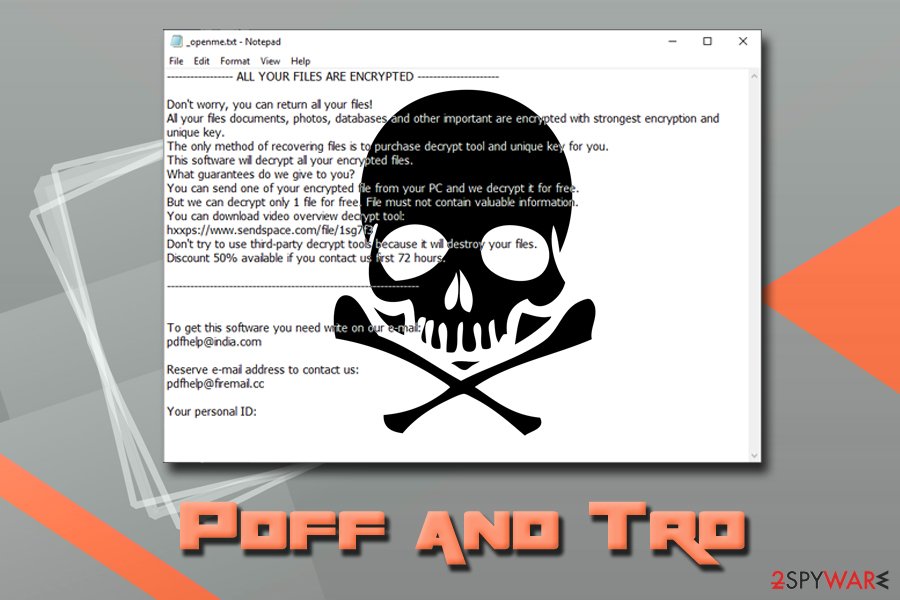
———————— ALL YOUR FILES ARE ENCRYPTED ————————
Don’t worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees do we give to you?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information
Don’t try to use third-party decrypt tools because it will destroy your files.
Discount 50% available if you contact us first 72 hours.——————————————————————————————————-
To get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]Your personal ID:
Crooks who spread viruses such as Djvu ransomware are most likely to urge for cryptocurrencies only. The most popular demanded currency is Bitcoin[3] as it is commonly used worldwide. Hackers urge for this type of ransom because cryptocurrency transfers do not require any specific personal details, and because of that, the process remains completely untrackable. This lets the crooks to scam victims easily without the risk of getting caught.
Djvu virus – ransomware which can enter the computer system via spam email messages and their rogue attachments.

Djvu virus – ransomware which can enter the computer system via spam email messages and their rogue attachments.
If you are seeking to recover your encrypted data, remove Djvu ransomware virus first before that. If you do not proceed with these actions in the right order, your files might be encrypted again after the next computer boot as the cyber threat will still remain in the computer system. For next time, make sure you take care of your data’s safety properly. A piece of advice would be to store it on a remote server or device which is accessible only for you. This way no other person will be able to reach that data.
Performing the Djvu ransomware removal requires a lot of attention. That is why you need to leave the process for reliable anti-malware computer software. However, we suggest using a program such as Reimage Reimage Cleaner or SpyHunter 5Combo Cleaner to detect all malware-laden content that might be some type of malicious files hiding in the PC system. If all hazardous components are successfully removed, the ransomware virus should not return to your computer after the process.
One more thing you need to know about Djvu files virus: this file locker can inject malicious components anywhere in the system, furthermore, it can clean paths for other malware to distribute easily, delete Shadow Volume Copies of encrypted documents, and add unwanted content to the Windows Registry.[4] Once you spot this threat, make sure you get rid of it ASAP.
To recover files encrypted by Djvu ransomware, try the STOPDecrypter from DemonSlay335. According to the researcher, the program is not ready to recover all encrypted files. At the moment, it works only for this personal ID: 6se9RaIxXF9m70zWmx7nL3bVRp691w4SNY8UCir0 which is generated while your computer is off. Take into account that if you try to add invented numbers can result in a complete loss of your encrypted data.
Djvu ransomware infection stages
Djvu ransomware infection progression is multi-stage, and there are several steps that it performs as soon as it is able to get into the machine’s system. The primary executable installs into the LocalAppData[5] and then downloads several additional files: 1.exe, 2.exe, 3.exe, and pdatewin.exe. All of these executables serve different functions:
- 1.exe is used to disable various features and functionalities within Windows Defender. Additionally, the file launches a PowerShell script called Script.ps1 which disables Defender’s real-time protection feature;
- 2.exe modifies Windows’ HOSTS file by adding multiple security site URLs, preventing users from navigating there and seeking for help;
- 3.exe’s functionality is not yet identified.
After these processes are complete, Djvu ransomware will contact C2 server, providing hackers with the unique ID that is based on victims’ MAC address.[6] The remote server then responds with the encryption key that is used to encode all personal files. During data encryption, Djvu virus launches a fake Windows Update window (spawned by pdatewin.exe) so that the victim would not suspect anything.
Finally, Djvu ransomware will append the appropriate file extension, depending on the virus version. For example, a file called picture.jpg will be turned into picture.jpg.djvu and will become inaccessible for users. Additionally, an _openme.txt ransom note is inserted into each of the affected folders.
Once the encryption process is complete, malware will create a scheduled task called Time Trigger Task that will periodically encrypt newly-added files.
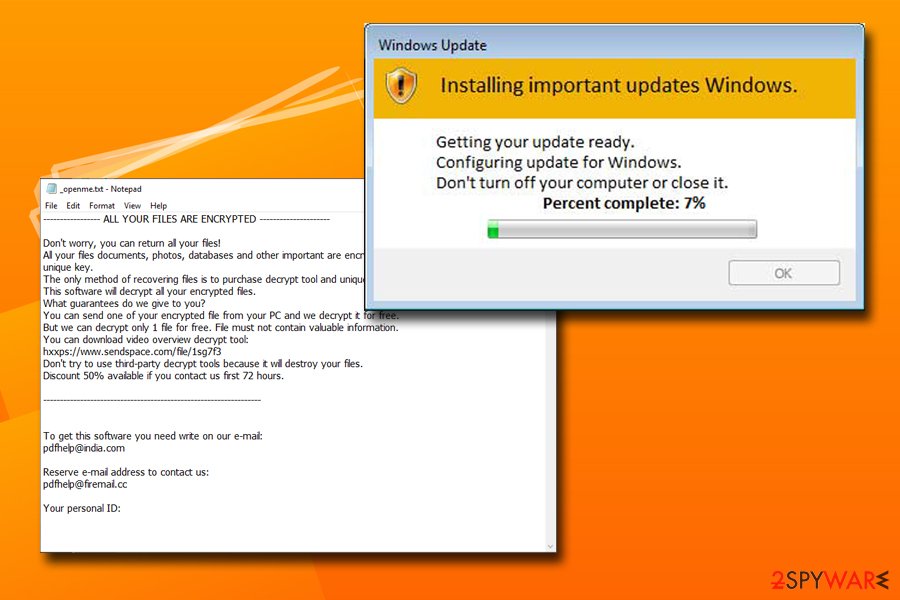
During file encryption process, Djvu ransomware runs fake Windows Update window

During file encryption process, Djvu ransomware runs fake Windows Update window
Djvu virus versions explained
Djvu virus was spotted on the internet in the late end of 2018. Malware researchers have identified it as one of STOP ransomware versions. However, together with the new year, the ransomware virus started using new file markers to help users find encrypted files among the untouched ones. The ransom note file is still named as _openme.txt and is placed in every folder with the encrypted data. Below you can find more information about each version:
Djvus virus
Djvus file ransomware came out right before the New Year. While virus developers haven’t changed the virus much, we can see that the email address is [email protected]. In addition, the virus is still offering 50% discount for those who contact its developers within 72 hours. Unfortunately, people have reported about numerous cases when they found this virus on their computer system, cloud services and even hard drives which were connected to the compromised system without much thinking. While some versions of STOP ransomware can be decrypted, unfortunately, this is not applied to the Djvus virus.
Djvuu virus
Djvuu ransomware was discovered back in December 2018. As the name suggests, it is appending the previously mentioned extension to affect users’ personal data. The ransom note displayed in a text file is still named _openme.txt and displays the message encouraging victims to contact these criminals via email and contact addresses: [email protected] and [email protected]. Djvuu virus is not decryptable, so you should use your files’ backups to recover encrypted data. The virus is using RSA encryption method to make files useless. The private keys are stored on hackers’ servers.
Uudjvu ransomware
Uudjvu ransomware is a slightly different version of the same Djvu virus that appears on the targeted system by using the common PirateBay setup window and this way attempts to steal user’s credentials from various accounts to use them in later scams. Developers created this variant without a ransom demand but files on the computer still get encrypted by using AES and RSA mix. The affected part of files is marked with .uudjvu file appendix. We don’t recommend contacting hackers for their ransomware demands as you can be left with more damage on your computer. Remove the virus at first and then continue with the recovery of your files. Use backups or third-party software in this stage.
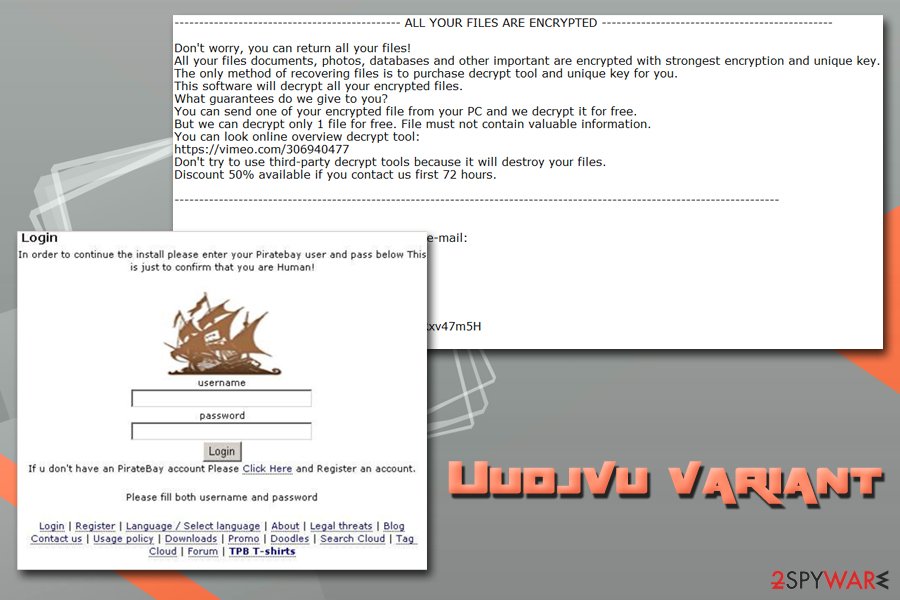
Uudjvu ransomware was almost identical to the original – Djvu – version of the virus

Uudjvu ransomware was almost identical to the original – Djvu – version of the virus
Djvuq ransomware
Djvuq ransomware is one of the versions that are more similar to the initial Djvu virus. It also encrypts files using the algorithm and marks encoded photos, documents or even archives with .djvuq at the end. Ransom note, in this case, also gets placed in the _openme.txt file with the discount deal on the ransom and previously used contact emails [email protected] and [email protected].
Udjvuq ransomware
Udjvuq file ransomware also appeared in December 2018 following previous identical versions. Cybercriminals behind the threat still focus on the encryption and file marking process with extortion purpose. However, ransom note states about the only way to recover the files – pay up. According to developers, other decryption tools cannot give you the needed results, so they give you a half-off for the ransom if you contact them in the first 72h. These details alongside the same email addresses are delivered in the file _openme.txt.
Tfude ransomware
Tfude ransomware is one of the numerous versions of Djvu virus. Being split into several versions as well (.tfude, .tfudeq, .tfudet), the virus is actively trying to overcome computers’ protection and install its malicious executable. Once active, malware encrypts files and drops _openme.txt ransom note. Unfortunately, even if your computer is offline, the virus can still continue the encryption of your files.
Additionally, cybercriminals are asking to use [email protected] or [email protected] email addresses to reach them for files’ decryption. However, making any contact with these criminals can result in money loss. If your personal ID consists of these numbers, you should be capable of using the decryptor given at the end of this post: 6se9RaIxXF9m70zWmx7nL3bVRp691w4SNY8UCir0
Pdff ransomware
Pdff ransomware also uses AES encryption algorithm to encrypt files and was first spotted in January 2019 attacking computer users from the Middle-East. Nevertheless, the ransom note _openme.txt remains to be written in English language and contain almost identical text that is typical for Djvu file virus infection.
However, this time crooks ask users to contact them with the help of [email protected] and [email protected] email addresses. Another difference from the previous variants seems to be the file extension that is added – .pdff. While this version is not decryptable yet, we suggest you remove Pdff ransomware and use alternative file recovery methods.
Tro ransomware
Tro ransomware was observed on the web just a day after Pdff ransomware came out. It was spotted being distributed with the help of cracks, keygens or bundled software that includes adware applications.
As soon as the virus enters the machine, it encrypts all the available data (skipping system files) with the help of a secure encryption algorithm and adds .tro file extension. This time it seems that the extension is the only difference compared to its previous versions, as the ransom note is called _openme.txt and the contact emails are [email protected] and [email protected].
The two latest variants of Djvu ransomware are .tro and .pdff, which share same contact address.

The two latest variants of Djvu ransomware are .tro and .pdff, which share same contact address.
Adobe ransomware
.adobe file extension has first been introduced by an infamous Dharma ransomware. However, Djvu ransomware has also started using this extension after encrypting victim’s files and making them useless. After some time, it was changed to .adobee. The virus is still using [email protected] as the default email address which should be used by victims to contact hackers for the ransom.
Unfortunately, no matter some of the previous versions can be recovered by using STOPDecrypter, .adobe hasn’t been added to this tool’s database yet. If infected, keep checking this post and hope that security researchers will soon find a cure for this malware.
Adobee ransomware
As we can see, Djvu ransomware has A LOT of other versions, the cybercriminals have released another variant lately. This one is familiar with the Adobe ransomware, however, with two e’s (Adobee). It has the same operating principle. Once installed, the ransomware virus injects malicious content in the system and performs the encryption. After that, files appear with the .adobee appendix and are blocked from any access.
Additionally, Adobee ransomware, just like other Djvu versions, provides a ransom message named _openme.txt. The note shows up in the Notepad. Crooks urge for some money in order to receive the decryption tool. They provide [email protected] and pdfhelp@ firemail.cc email addresses as a way to make contact.
Blower ransomware
Blower ransomware can enter the PC secretly just like others of its kind, for example, through infected hyperlinks, harmful attachments, etc. Once it is installed, rogue and harmful content is injected into the system and malicious activities such as data encryption are performed.
Blower is appending the .blower file extension to each encrypted file. This ransomware virus is capable of locking all kinds of data such as images, audio files, video, text documents, databases, excel sheets, powerpoint, and others. Once the encryption is performed, crooks notify their users through a text message named _readme.txt. Two emails are provided in this message: [email protected], [email protected]. We suggest you avoid any contact with these cruel people.
Norvas ransomware
Norvas virus is a crypto-malware that is using the same _readme.txt ransom note to swindle the money from users worldwide. It is an easy task because before that the virus changes the code of target files and then appends the special extension called .norvas to every piece of data that was affected. In this case, files become useless and cannot be used as previously.
The developers of Norvas ransomware can be reached via [email protected] and [email protected] email addresses. They also offer to provide the 50% discount for the ransom if they are contacted within 24 hours. However, do NOT believe these people as they are notorious scammers stealing users’ money.
Grovat ransomware
Grovat is using AES-256 encryption code to make users’ data useless. Additionally, the victim is required to make a special payment to a secret bitcoin wallet in exchange for the decryption code. Email addresses users are typically pointed to are called either [email protected] or [email protected]. These addresses should be used to contact cybercriminals and get the bitcoin address for the payment. However, we do NOT recommend making any contact with these people.
To generate a unique identifier along with the decryption code assigned for each user, malware contacts its C&C server. The ransom note is called like any other used by other Djvu versions – _readme.txt. You should remove all files that belong to this malware instead of contacting cybercriminals. To recover your files, you can try using STOPDecrypter.
As soon as Grovat ransomware encrypts files, they impossible to open

As soon as Grovat ransomware encrypts files, they impossible to open
Verasto ransomware
Verasto was first spotted at the end of April 2019 and, since its release, it has been infecting hundreds of users all over the world, remains one of the most prevalent Djvu virus variants to date.
Just as its predecessors, Verasto ransomware uses various propagation techniques, including:
- Spam emails;
- Exploits;
- Software cracks or keygens;
- Fake updates;
- Backdoor,[7] etc.
After its infiltration, the malware scans the device looking for a variety of most popular file types, such as .jpg, .mpeg, .xlsx, .html, .zip, .php, and others, and appends .verasto markings. Nevertheless, the virus avoids encrypting the most crucial system files (although it does modify certain OS files and settings), along with executables as they are not considered to be valuable.
Unfortunately, data locked in such a way requires a unique key that is secured on a remote server controlled by hackers. They offer a decryption tool for a $980/$490 payment in Bitcoins. Experts recommend avoiding paying criminals, however, as the chance of getting scammed remains quite high. Instead, remove Verasto ransomware and use alternative data recovery methods as per instructions below.
Hrosas ransomware
One of many versions in the family that came out in April 2019, Hrosas ransomware still includes the same emails as previous versions. [email protected], [email protected] remains the primary method to contact people behind this virus, and criminals provide another method – Telegram account.
Also, as typical for this family, ransom note comes in the text file _readme.txt and politely asks to pay up with the discount offer. Besides this version, on the same day, researchers discovered a file-locker virus that marks data using .kiratos extension, but not much samples got revealed and it may not be that widely spread as other ones.
Todarius ransomware
As known for a while, STOP decryption tool worked for many versions, including the previous to this Todarius ransomware variant. However, many user reports and sample analysis revealed that there is a patch in the version, so decryption is not possible, unfortunately.
It seems that once STOP decrypter is run, the extension changes to .kiratos and 0 files are decrypted. it happens with a few updated versions of this tool, so it is allowed to say that .todarius file extension marked files are not decryptable. This and new email added to the mix – [email protected], are the only unique features for the variant.
Hofos ransomware
Hofos ransomware came soon after the Todarius version, at the same time like .dutan and .roldat versions that remained not that active. However, Hofos files virus was yet again slightly unique than other ones, as user samples showed. marking the 74th version of the Djvu ransomware it comes with the same already known ransom note file _readme.txt and recently renewed email addresses – [email protected], [email protected].
The distribution of the malware includes packs of software spread around in public torrent sites. Multiple users reported that particular subtitle packs and Sony Vegas 16 plugin delivered an executable with a malicious payload. This version is probably the one that started a tendency for Djvu creators because since .hofos main vector remained cracks and other pirated data.
Sarut ransomware
The first version of the month of May, Sarut ransomware came alongside other variants like .fedasot, .berost, .forasom, .fordan. The few added another email to the mix – [email protected] that got used in latter versions from time to time, but not as the primary contact email.
As given from the name, this version encrypts files with a .sarut file marker and developers still use offline keys for the file locking, so many victims can get their files back with STOP decrypter. Djvu developers seemed to sleep on their money gotten from victims and focusing on these continuous releases without making any crucial changes to the coding.
Ferosas ransomware
At the same time as not so unique versions .codnat, .codnat1, .bufas, .dotmap, .radman and .rectot came out Ferosas ransomware that is yet another version in Djvu family that cannot be easily decrypted with the STOP decryption tool or other programs offered by programmers or researchers.
These versions included a mix of contact emails with more uncommon [email protected], [email protected]. However, the same ransom note, ransom amount and encryption methods, so offline keys still help to decrypt files or at least some of them. The distribution remains focusing around software cracks and torrent files. Particular versions were reportedly included in packs with Sony Vegas application cracks and other software.
Skymap ransomware
Skymap ransomware came out in the summer alongside .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret. A few of them got more active than others ad can be identified from a new contact email [email protected]. However, .skymap was the one that got more attention from researchers due to user samples and reports.
Nevertheless, these all versions can be decrypted because developers use offline keys for encryption mainly. Still, the main vector remains serial numbers, cracks and other illegal files delivered via torrent sites.
Heroset ransomware
July was not the biggest month for Djvu ransomware because Heroset ransomware and .pidon, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke variants that came out this month all were almost identical. [email protected], [email protected] emails, _readme.txt ransom note ant the same discount offer to lower $980 to $490 remained unchanged.
Although the versions seem to be more persistent and making all the changes in the system folders, STOP Decrypter with needed updates works perfectly for files locked using offline keys. However, during this time it was revealed that besides encryption processes, Djvu delivers AZORult malware as a secondary payload.
Litar ransomware
Summer of 2019 was big for Djvu virus, that is uncommon in ransomware world because developers mainly rest during the season. However, Litar ransomware and .dalle, .lotep, .nusar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau all got released in a span of three weeks.
Although some of them got more popular than others, all can be decrypted with a proper version of the decryption tool. Developers still trying to calm people by stating “don’t worry” but scaring them with a claim that there are no other options besides paying the ransom. At this point, decryption is possible for files locked using offline keys and there is no need to panic or pay the demanded amount.
Madek ransomware
Starting with Madek ransomware, creators released a new version a day up until the very end of August. Not developing anything new, criminals wanted to infect as many systems as possible due to positive results with the decryption tool developed by Michael Gillespie. Not many things get to be changed, as usual. [email protected], [email protected] still remain default contact emails for these versions of file markers:
- .tocue
- .darus
- .lapoi
- .todar
- .dodoc
- .bopador
- .novasof
- .ntuseg
- .ndarod
- .access
- .format
- .nelasod
- .mogranos
- .cosakos
- .nvetud
- .lotej
- .kovasoh
- .prandel
- .zatrov
- .masok
- .brusaf
- .londec
- .krusop
- .mtogas
- .nasoh
- .coharos
- .nacro
- .pedro
- .nuksus
- .vesrato
- .cetori
- .masodas
- .stare
- .carote
- .shariz
Gero ransomware
Although those last few weeks were extremely active for developers, versions were decryptable yet again. However, Gero ransomware release changed everything. Encryption method and coding were changed, and developers started to use the proper asymmetric file-locking algorithm. This fact made STOP virus decrypter useless, in most cases because offline keys cannot be used. During this time, [email protected], [email protected] started to be used as main, and the only contact emails, ransom note unchanged and the file remains _readme.txt.
Kvag ransomware
Kvag ransomware came out after all those changes and become extremely active, based on user reports on our site. However, previous versions .hese, .seto, .peta, .moka, and .meds also encrypted peoples’ computer at the same time. Thanks to all those samples and reports, we and other researchers could investigate the newest changes made by Djvu creators.
Yet again, people are not careful with their files and illegal habits, so ransomware quietly spreads via torrent files. Some of you stated that cracks and Russian file-sharing sites led to the ransom note appears on the screen. Since there is a long period of waiting until the proper decryption tool gets developed, you should store all virus-related files on an external device and wait for the possibility to restore your data.
Karl ransomware
Karl ransomware came with .domn virus version and more options from researchers. The changed method of file-locking left no options but to disable STOP-Decrypter and end service of file recovery. However, other researchers made their analysis and now can offer other services.
In some rare cases when offline keys still get used you can try to use the decryptor, or rely on other services that are offered by researchers:
- For people that have data encrypted using offline keys, there is a decryption option here.
- Dr.Web also offers a tool named Rescue Pack that costs 150 euro per user.
Nesa ransomware
Nesa ransomware is still delivering AZORult malware and making all the changes in the system like dropping modules set to steal stored data and information from web browsers. However, the threat leaves hosts file on the system that keeps you from accessing sites like ours and search other methods to recover from the attack. For that, go to this location and find “hosts” file: C:\Windows\System32\drivers\etc. Delete it completely by using admin permissions.
Upper-mentioned services can work for this variant, and you can additionally search these sites for decryption tool:
Ransomware viruses distribute via spam messages, software cracks, and adware bundles
According to cybersecurity specialists from LosVirus.es,[8] ransomware infections can appear on the computer because of an opened spam letter or its attachment. Some email messages, that are dropped by the crooks, might contain a hazardous link inserted inside the letter itself, or a dubious attachment that comes clipped to the email. Be aware of all questionable emails, do not open and if they look malicious or suspicious in some certain way.
Furthermore, you can detect that something is wrong if the email message contains various grammar mistakes, and if it comes from an unrecognizable sender. However, not all of them look this way. Some crooks pretend to be from worldwide organizations. So, if you were not expecting to receive anything important recently, you better not access any messages. What you should do is contact the company directly if necessary.
Additionally, in some cases, ransomware viruses can distribute thru third-party networks. All pages that come from secondary sources often lack required protection and do not fit the security requirements. This leads to a high risk of getting infected by dangerous malware, e.g. ransomware. We suggest avoiding all non-original pages and suspicious hyperlinks that you might encounter while browsing the web.
With the .tro file extension, ransomware was spotted being distributed with the help of so-called “cracks” and “keygens.” These files are used to crack the original software to make it perform as a licensed version. Such activity is highly illegal, and users could face fines and legal actions if they get caught. Besides, the risk of infecting the PC with ransomware should diminish the urge to crack programs.
Finally, researchers said that the virus is also being spread bundled with adware programs. To stop unwanted apps from entering the machine, never skip the installation steps and read through the installation instructions. Always pick Advanced/Custom installation mode instead of Recommended/Quick one and remove all the optional components that are offered.
Many users recently reported that the ransom note stating about encryption and ransom demand appeared on their screen after cracked software installation. Such programs like Adobe Photoshop, Illustrator or video games like NBA package, serial numbers or license keys of legitimate applications, security tools contain much more in the installation setup.
Public pirated content pages deliver such ransomware payload as installer file and once the executable gets loaded on the machine malicious script is triggered and encryption starts. The file-locking process happens in a matter of minutes, so you cannot do anything about it, even though you noticed that something is off.

Djvu ransomware uses spam emails, among others, to distribute malware’s payload

Djvu ransomware uses spam emails, among others, to distribute malware’s payload
To get rid of Djvus virus, employ recommended software
To remove Djvu virus, use only reputable computer software. Furthermore, you can detect all malware-laden content by scanning the computer system with these tools:
Such software is created to lengthen the removal process for all users. Even though the detection process might take a while, please, be patient as you will find it incredibly useful later on.
Performing the Djvu ransomware removal requires a lot of attention. This is the main reason why you should leave the process for automatical computer tools. Furthermore, after you proceed with the elimination, make sure that you perform some system backups. All ransomware-related components need to be removed permanently for the computer to work normally again.
NOTE! You can find yourself blocked while trying to download anti-virus software or visit a legitimate security site. For that, go to this location and find “hosts” file: C:\Windows\System32\drivers\etc. Delete it completely by using admin permissions.
This entry was posted on 2020-02-18 at 08:24 and is filed under Ransomware, Viruses.

