Dridex malware – a well-developed banking trojan that can avoid detection by AV engines and anti-malware tools
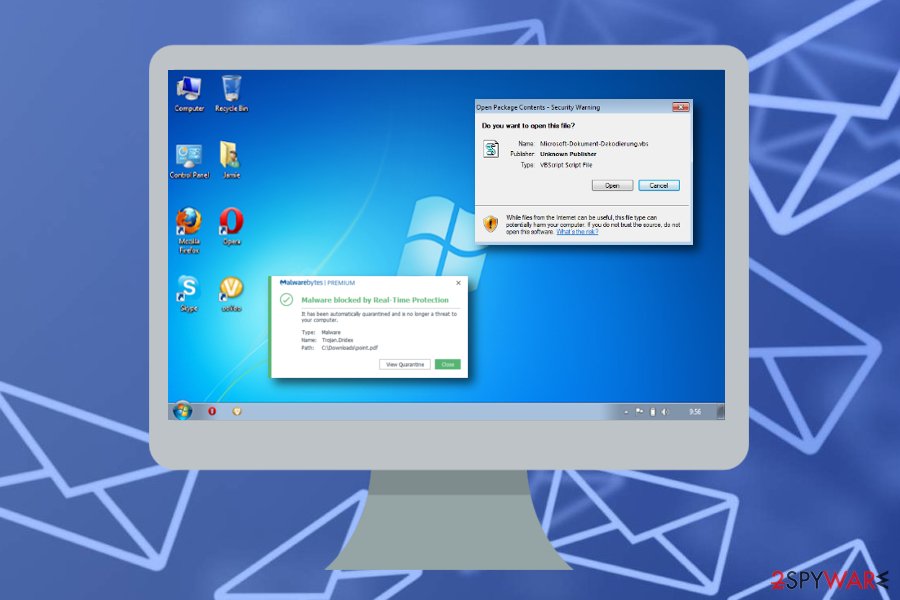
Dridex – malware that can avoid detection of antivirus engines

Dridex – malware that can avoid detection of antivirus engines
Dridex virus is malware used to steal data, access sensitive information, or perform secondary attacks on the already infected machines. Developers of the Trojan use spam campaigns to spread the infection and disguise it as UPS delivery company or other services, so people open those emails without thinking twice. As soon as the attachment is opened, malware begins its infection routine, which impacts various system files and settings.
During the active years of this Trojan, criminals use many names of different companies to mimic their billing emails and other notifications, so malware scripts are launched without direct installs. The last activity of Dridex was noticed in April 2020 when FedEx-themed malspam campaigns were surfacing.
Dridex, also recognized as Bugat or Cridex,[1] is a notorious piece of software that aims to steal banking details and track keystrokes of Windows users. Up to now, no campaigns targeting macOS were detected, but it might be possible in the future. Date stolen by Dridex Trojan might be used or transferring money from victims’ accounts, which results in huge monetary losses.
Also, the malicious payload gets dropped using compromised FTP websites and hyperlinks added on those emails directly or included on Microsoft documents as rerouting links. Unfortunately, it is extremely easy to trigger the install of this virus because a few clicks on the screen launches the macro malware drop.
| Name | Dridex |
|---|---|
| Type | Malware |
| Modules | Trojan, worm, keylogger, botnet |
| Other names | Bugat, Cridex |
| Target | Windows users |
| Distribution | Infectious Microsoft Windows or Excel documents, infected websites |
| Aim | To steal banking data and perform illegitimate money transfers, inject scripts, and obtain sensitive information like passwords and logins. The malware poses as UPS, FedEx, or another service to fake the legitimacy of malware-laden emails |
| Detected as | Win32:Trojan-gen, Trojan.GenericKD.41400500, Trojan.GenericKD.41400500 (B), Trojan.TR/AD.Dridex.nbtoz, Trojan.Packed2.41796 |
| Active since | 2014 |
| Elimination | Dridex malware removal process can be easier if you choose the proper AV tools and run the full system scan, so all the intruder get deleted |
| Repair | You can download and install software such as Reimage Reimage Cleaner Intego to find all traces of the virus and affected files or corrupted programs. These PC optimization applications can help and fix damaged data on the system |
Dridex malware aims to operate in more than just one way on the infected computer system. Security experts have discovered that this notorious virus is capable of recording the victim’s keystrokes and has gained the name of keylogger.[2] Tracking users key presses can relate to different types of illegitimate and dangerous activities.
For example, criminals who distribute Dridex banking trojan can use its key-logging feature for spying on sensitive login details, various account passwords, personal information, and the same credentials that we have talked about before. Collection of such data might relate not only in monetary losses but also to serious identity theft.
The antivirus avoidance feature is also the one belonging to Dridex trojan. Reports say that this malware might be hard to detect as it is good at hiding. However, some well-known anti-malware programs are still capable of spotting strings of this cyber threat and it can be found in these types of names:[3]
- Win32:Trojan-gen.
- Trojan.GenericKD.41400500.
- Trojan.GenericKD.41400500 (B).
- Trojan.TR/AD.Dridex.nbtoz.
- Trojan.Packed2.41796.
Note that instant Dridex malware removal is a necessity once your anti-malware detects such threat names. Also, you can try using a program such as Reimage Reimage Cleaner Intego for searching for malware strings. It is very important to react fast as this trojan can inject other dangerous infections remotely and cause severe damage to your computer. This tactic is known as “injection attack”.
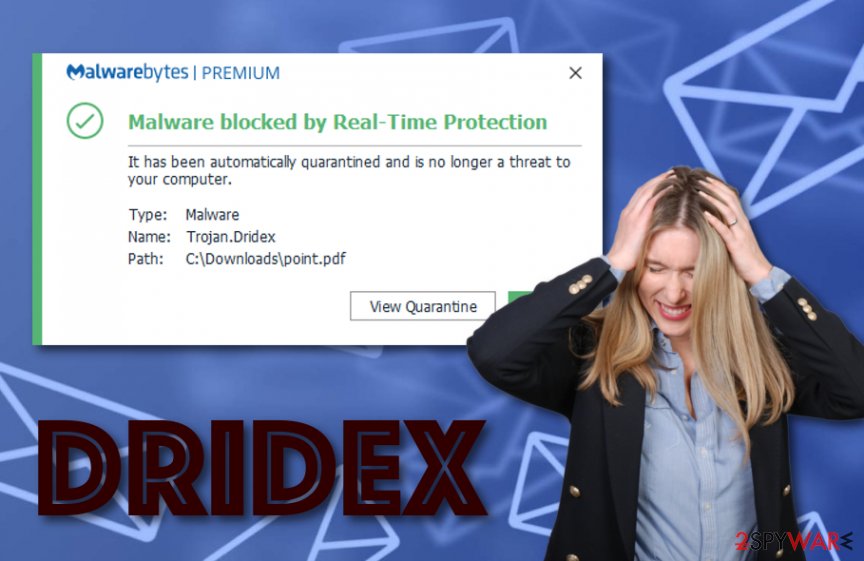
Dridex is a dangerous malware that has been active since 2014

Dridex is a dangerous malware that has been active since 2014
Nevertheless, Dridex is capable of disabling Windows Script Host objects by using the Application Whitelisting tool and its WMIC vulnerability. Additionally, this dangerous form of computer virus brings infectious VBS content to the system which is carried through XLS-based scripts. As you can see, it is very important to take quick actions after spotting the first signs of malware. Performing Dridex removal should be your first priority now.
There are many more activities that the virus might be capable of but they might not be identified yet. For example, Trojan viruses often overuse CPU and GPU power which causes regular system crashes. They also might end up placing infectious processes and files all over the system. So, remove Dridex and avoid possible computer and software corruption.
The name of Dridex has been known since 2014
Dridex has become a notorious celebrity already in 2014 when countless corporate users worldwide reported their stolen passwords of bank accounts. As a result, they suffered huge financial losses. Due to the complex and exquisite structure as well as distribution methods, the malware has succeeded in causing the entire chaos in the IT world.
Dridex virus techniques helped it to stand its ground among other aggressive computer threats and remain invincible. While the malware mainly targeted North America and Western Europe, now it moves further east. The Baltic states are the next target of this malware. Ordinary users are likely to become victims as well.

Talking about nowadays, the year of 2019, there were numerous reports coming out that Dridex has been avoiding antivirus detection and infecting computer systems worldwide without big effort. Nevertheless, experts revealed that the malware has expanded its distribution plot from email spam to misleading FTP pages.[4]
Information on other characteristics of the malware
Alternatively known as Worm.Win32.Cridex or Cridex, the threat is able to steal log-in data and passwords by making several significant modifications in the browser. Since it operates both, as a trojan and as a computer worm, it managed to escape detection of a security program in the past. Regarding its characteristics of a worm, it might infect a system via a link encountered in the file-sharing domain.
Once Dridex malware successfully settles on the computer, its trojan features get activated. Likewise, the malware meddles with your browser settings by redirecting you to the fake version of your bank instead of leading to the original site. As a result, it is able to track and record all your passwords and spy on your activity by taking secret screenshots of your computer screen.
Moreover, when Dridex botnet takes control of the device, you might notice occasional system errors and notifications to reboot the system. When the required information is collected, it is transferred to hidden hackers‘ servers. As a result, victims might suffer financial losses overnight or within a couple of hours.
The main goal of the virus is to steal sensitive information related to bank accounts, si fraudulent transactions to criminal-belonging accounts can be made. Stealing money is the most common aim of various malware creators. This Dridex trojan can also operate as a key logger and record keystrokes on sites where logins and passwords. This malware can also perform injection attacks during which remote commands can be executed on code injected into specific programs. 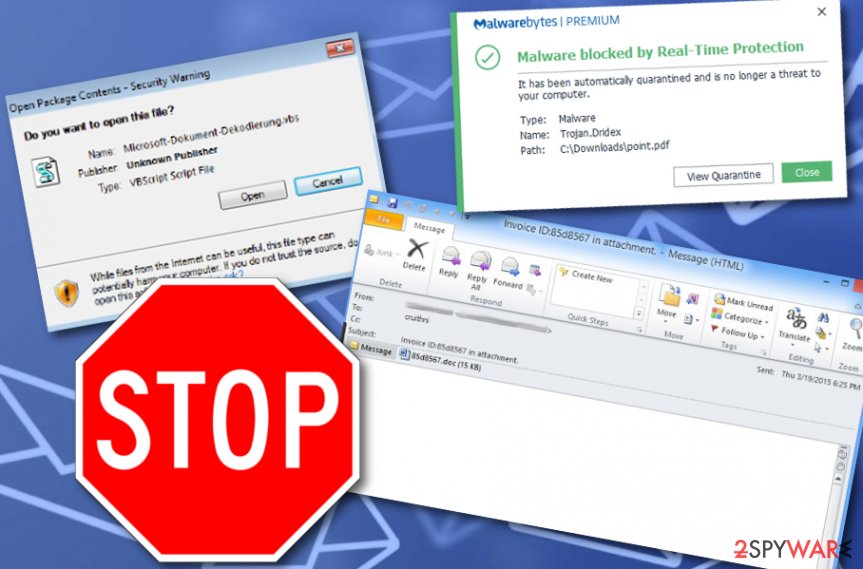
Dridex is a notorious form of malware that travels through infectious MS Word Documents or Excel files

Dridex is a notorious form of malware that travels through infectious MS Word Documents or Excel files
The operation and transmission techniques of Dridex malware
Its distribution and operation ways are worth mentioning as they assisted the malware in to remain active for such a long time. The first signs of Dridex banking trojan were already spotted in 2014. Due to the botnet (the network of machines and devices which manage the distribution of the malware), the malware successfully infiltrated thousands of computers.
Ordinary users may not be familiar with Dridex as it mainly targeted banks and financial institutions. Its success also lies in spreading the menace via macros embedded in spam messages. In order for victims to activate the threat, the hackers label the emails as invoices or financial report files. If the targeted operating system automatically enables the macros, the malware sets out to perform its misdeed.
After the infiltration, the malware causes real havoc: it creates backdoors to secretly install other malignant files. Moreover, the malware has joined forces with multiple ransomware developers. It has been observed that such a virus as Bart also facilitated the distribution of Dridex and Locky ransomware.[5] That is how this dangerous malware has also earned the name of the ransomware.
malware creates campaigns and delivers emails stating about invoices, billing information, or bookings. Notifications mainly include links or Microsoft documents with information supposedly sent from services like UPS or FedEx. Enabling content buttons launches malicious macros automatically.
Some examples of Dridex malware distributing emails:
Subject: Invoice Due #7300980
Good morning,
Attached is the invoice for the work completed at your property. Payment should be remitted to the invoice below. We appreciate your business.
For security reason the invoice is password protected: 159
Should you have any questions, please do not hesitate to contact us.
Jess Tiffani RSW, CCAC, ICADC, CEC
Director
Pegasus Recovery Solutions
m: 250.514.1083
f: 250.294.6850
a: 270 – 2950 Douglas St, Victoria BC, V8T 4N4
w: www[.]pegasusrecoverysolutions[.]com
e: [email protected]
Subject: FedEx Billing – Invoice Ready for Payment
You have a FedEx invoice ready for payment.
Your invoice is ready for payment
Dear Customer
Your account has a new invoice(s) from FedEx ready for payment.
Invoice number: Invoice amount:
9-053-76763 180.82Thank you for your business,
FedEx
Ensuring proper cybersecurity is a crucial step to take
Security experts from LosVirus.es[6] warn users that taking recommended precautionary measures should be a crucial step for each person that uses a computer, laptop, or similar device. Malicious infections are ready to sneak into the system through different types of ways such as email spam campaigns, infected networks, malicious links, fake software updates, etc.
Talking about spam emails, the malicious payload will supposedly come inserted into a Microsoft Word document or into an EXE file. If you ever find such components clipped to an email, use a reputable anti-malware program to scan the entire content and identify rather it is harmful or safe to open.
Continuously, you should always have trustworthy antivirus protection working along your side while completing browsing work. Try avoiding all rogue-looking networks as they supposedly lack protection. These types of websites usually appear to be based on piracy, gambling, online gaming, or porn-watching.
Dridex malware termination steps
Trojans and computer worms are surely highly destructive and frustrating viruses. In order to remove Dridex virus completely, update your anti-virus, and install an additional security application, such as SpyHunter 5Combo Cleaner or Malwarebytes. The anti-spyware software is specifically created to confront such malware as this banking trojan.
In addition, it will help you block other samples of this category as well as ransomware threats. Manual Dridex removal is not recommended as detecting its executables might be a futile activity. Your cautiousness also plays a great role in increasing cybersecurity. However, what you can do on your own is rebooting your computer to Safe Mode or performing a System Restore.
These two below-provided features allow disabling malicious processes that might be ongoing on your machine and reversing previous changes that were made during the activation period of Dridex malware. However, do not feel too relaxed after the cyber threat vanishes as you need to ALWAYS follow security recommendations if you want to keep your device/machine protected from hazardous infections. Remember to double-check and install Reimage Reimage Cleaner Integofor virus damage repair purposes before running the AV tool or after the proper malware removal.

