EGMWV ransomware is a malicious program that is designed to encrypt personal files on the infected computer
EGMWV ransomware is a file locking virus that stems from Snatch virus family

EGMWV ransomware is a file locking virus that stems from Snatch virus family
EGMWV ransomware, or otherwise known as doctor666 ransomware, is a type of malicious software that focuses on money extortion after encrypting pictures, documents, databases, and other files on the host machine and holding them hostage. Only a unique key that EGMWV ransomware developers have access to can unlock the data.
As soon the malicious payload of the EGMWV virus is executed, it begins to look for personal files to encrypt and, once found, locks it with the help of the AES encryption algorithm, also marking files with .egmwv extension. To recover access to locked data, users are asked to pay up a ransom in Bitcoins. For communication purposes, crooks leave a notification – DECRYPT_EGMWV_FILES.txt – which explains that users need to contact [email protected] or [email protected] if they want to have a chance at recovering personal files. Paying criminals is not recommended, as they might never send the required f EGMWV ransomware decryptor, resulting in monetary loss to victims.
| Name | EGMWV ransomware |
| Type | File locking virus, crypto-malware |
| Family | Snatch ransomware |
| Associated files | Update_Collector.exe, DECRYPT_EGMWV_FILES.txt |
| Service and registry | Malware creates a “SuperBackupMan” service that runs in Safe Mode due to a set registry key HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\SuperBackupMan:Default:Service |
| Capabilities | Encrypting all personal data on the host machine, rebooting into Safe Mode during the encryption process to avoid AV detection and removal, implementation of the data-stealing module, running |
| Main targets | Snatch ransomware mainly targets corporations and businesses, although it does not mean that regular users cannot be infected |
| File extension | All personal files are appended with .egmwv extension (virus skips system and most executables) |
| Contact | Malicious actors ask users to contact them via [email protected] or [email protected] emails |
| Data recovery | If no data backups were prepared before the ransomware attack, recovering it without paying criminals is difficult. Nevertheless, you might have a chance of restoring at least some of your files with the help of third-party recovery software |
| Ransom size | Depending on the affected party, crooks asked for ransoms between $2,000 and $35,000 in Bitcoin |
| Malware removal | Perform a full system scan with anti-malware software like SpyHunter 5Combo Cleaner or Malwarebytes |
| System fix | In case your machine is crashing, lagging or suffering from Blue Screen of Death errors after malware elimination, you can scan it with Reimage Reimage Cleaner – it can fix virus damage and restore Windows registry |
Discovered in early February 2020, EGMWV ransomware belongs to Snatch virus family which is known for its advanced capabilities, such as stealing personal victim information and accessing Safe Mode for encryption process. Due to previous practices of this malware strain, it is highly likely that EGMWV ransomware mainly targets corporate organisations and businesses, encrypting all data on networks and performing secretive surveillance processes for weeks. Interesting fact: the malware name (Snatch) comes from a highly popular British crime comedy movie from 2000 under the same.
While usually ransomware developers use several propagation methods, EGMWV file virus authors usually go for targeted attacks, which are executed with the help of unprotected Remote Desktop connections. Once inside, the attackers log to domain controller as administrator and penetrate a full computer network. EGMWV ransomware capability to perform encryption process in Safe Mode grants it evasion, as most of security applications are non-functional in this computer setting.
EGMWV ransomware is cryptomalware that reboots the Windows PC into Safe Mode in order to perform file encryption without getting detected by anti-virus software

EGMWV ransomware is cryptomalware that reboots the Windows PC into Safe Mode in order to perform file encryption without getting detected by anti-virus software
Once threat actors gain access to the compromised Windows computer (malware runs on Windows 7 through 10 machines 32 and 64 bit versions), they can launch the malicious payload of EGMWV ransomware manually, which immediately reboots the PC into Safe Mode. In there, a malicious executable runs in the background – it performs all the necessary system changes to perform data encryption. The whole process is finished just within a few seconds a reboot, so victims do not have time to react and interrupt it.
After file encryption, EGMWV ransomware authors inform users in the ransom note that they only have 48 hours to respond, or they could lose access to data permanently:
Hello! Your all your files are encrypted and only I can decrypt them.
Contact me:[email protected] or [email protected]
Write me if you want to return your files – I can do it very quickly!
The header of the letter must contain the extension of the encryptor.Attention!!!!
Do not rename encrypted files. You may have permanent data loss.To prove that I can recover your files, I am ready to decrypt any three files (less than 1Mb) for free (except databases, Excel and backups)
hurry up!
! ! ! If you do not email me in the next 48 hours then your data may be lost permanently ! ! !
According to security researchers from Sophos Labs, EGMWV ransomware, which is a variant of Snatch, might insert a data-stealer component into the infected machine, which would harvest the sensitive user inputs during malware’s operation (this is another reason to remove EGMWV ransomware as soon as possible):[1]
What we refer to as Snatch malware comprises a collection of tooling, which include a ransomware component and a separate data stealer, both apparently built by the criminals who operate the malware; a Cobalt Strike reverse-shell; and several publicly-available tools that aren’t inherently malicious, but used more conventionally by penetration testers, system administrators, or technicians.
While the encryption process is not likely to be stopped by anti-malware software due to rebooting into Safe Mode, most AV engines recognize the threat as follows:[2]
- Ransom:Win64/Gocoder.A!MSR
- BehavesLike.Win64.Generic.tc
- Trojan.Encoder.29809
- Malware/Win64.RL_Generic.R300784
- Ransom_Gocoder.R002C0DLE19
- HEUR:Trojan.Win32.DelShad.vho
- Mal/Generic-S, etc.
However, before you perform EGMWV ransomware removal, you should make a copy of all the encrypted data (this applies only if you had no backups), as getting rid of malicious software or using third-party recovery tools may result in permanent data corruption.
Unfortunately, there are very few options when it comes to a successful EGMWV ransomware file decryption, as there is no working decryptor currently available. Nevertheless, it may be created in the future, or third-party tools might be able to recover at least some data for you.
You Should use reputable anti-malware to get rid of EGMWV ransomware after you backup the encrypted data. Because ransomware might have affected the Windows registry and corrupted some system files, we also advise using Reimage Reimage Cleaner to fix virus damage after termination.
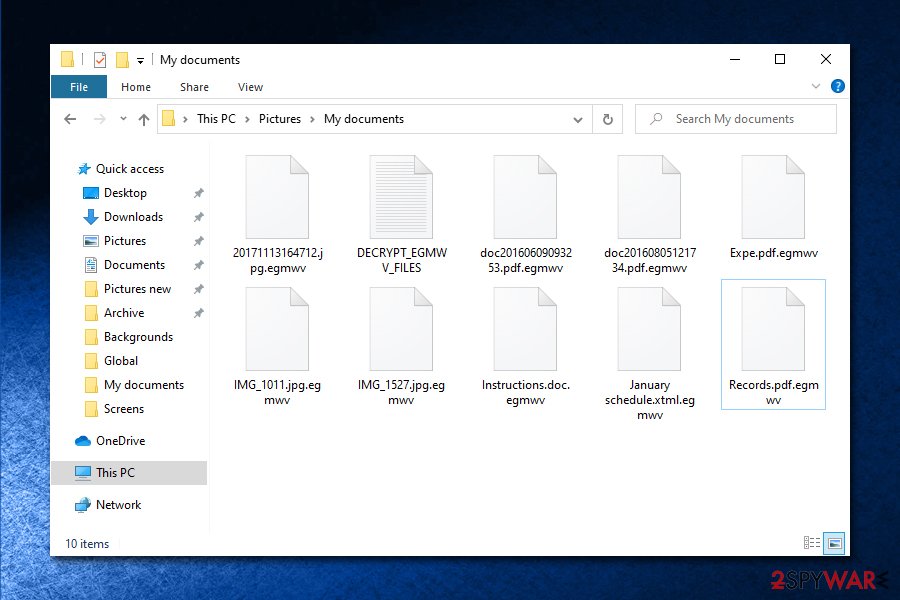
Unfortunately, recovering EGMWV ransomware encrypted files without paying the ransomware is almost impossible

Unfortunately, recovering EGMWV ransomware encrypted files without paying the ransomware is almost impossible
Ways to protect your RDP and prevent ransomware attacks
Cybercriminal groups that specialize in ransomware use usually employ several distribution methods, including spam email attachments/hyperlinks, software vulnerabilities, and exploits,[3] software cracks/pirated software installers, fake updates, etc. Nevertheless, because Snatch virus developers mainly target organizations, they perform targeted attacks with the help of RDP – this method became prevalent in the past few years, as it allows the attackers to act “on the spot” and perform necessary changes during the operation if unexpected circumstances arise.
In most cases, malicious actors use credentials acquired from previous targeted phishing emails or bought the information online on the dark web. After collecting the required credentials, all they have to do is scan the internet for vulnerable RDP connections and perform a break-in. In other cases, hackers can also automate the process with the help of a so-called brute-force attack, which applies a combination of well-known passwords (for example, “qwerty,” “administrator, “123456,” etc.)[4] in order to get in.
Thus, it is crucial to protect Remote Desktop-connected computers with the help of the following measures:
- Do not use the default TCP and UDP ports 3389;
- Use a VPN and disallow access on machines that are not running it;
- Ensure a strong, alphanumeric password is used;
- Only allow access via Remote Desktop to those that actually need it;
- Enable Network Level Authentication (NLA) via System Properties;
- Disconnect from the service as soon as it is not used.
EGMWV ransomware ransomware removal method
EGMWV virus is relatively unique ransomware, as it is programmed to start a Service named SuperBackupMan, which also runs in a Safe Mode thanks to Windows registry modification upon the infiltration. Therefore, booting into Safe Mode will not stop malware’s operation. Nevertheless, it should still be possible to remove EGMWV ransomware by using the most up-to-date security software, which would also eliminate the data-stealing component.
Note that EGMWV ransomware removal could permanently damage the locked personal files, so you should prepare a backup before using recovery solutions – we provide several methods below. Of course, if you backed your data before ransomware struck your computer, you have nothing to worry about, as you can negate all the effects of the virus easily.
If you had no backups, we still do not recommend paying EGMWV ransomware authors, as you might end up losing not only your data, but also a particularly high sum of money, as they might send you a non-working decryptor, or fail to contact you completely after you pay. In other words, you cannot trust cybercriminals, although, in some cases, victims might have no choice.
This entry was posted on 2020-02-07 at 08:03 and is filed under Ransomware, Viruses.

