GNS ransomware – malicious program designed to prevent access to personal files
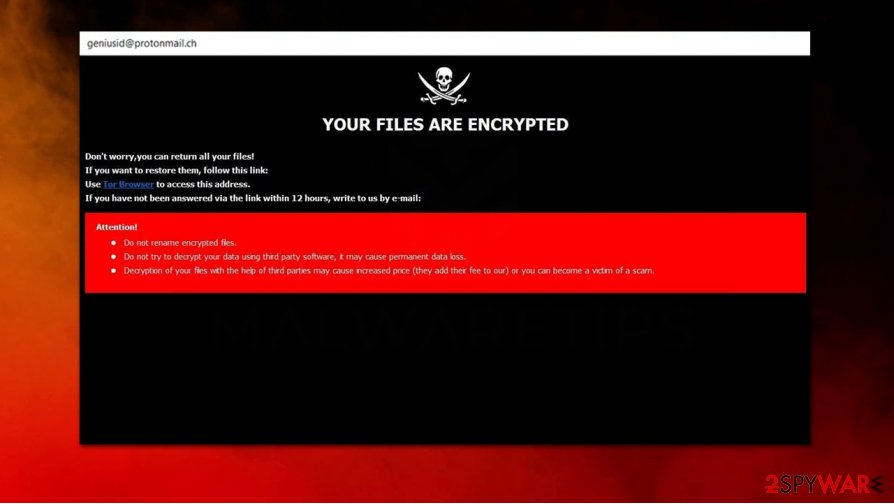 GNS ransomware is a data locking malware that belongs to Dharma virus family
GNS ransomware is a data locking malware that belongs to Dharma virus family
GNS ransomware is a threat that has been spotted spreading around the world in early July 2020[1] and was attributed to the Dharma ransomware family, which has been around for several years now. The malware spreads via several channels, including malicious spam emails, repacked installers, and weakly protected RDP connections.
As soon as the payload is executed, GNS ransomware begins the data locking process with the help of RSA + AES ciphers,[2], which also modifies file names. For example, a file “picture.jpg” is turned into “picture.jpg.id-random string.[[email protected]].GNS,” and can no longer be accessed by the victims.
Malware also drops a ransom note FILES ENCRYPTED.txt, as well as shows a popup window. These documents serve as a message from GNS files virus authors and explain that users have to pay a ransom in Bitcoin in order to regain access to their data.
| Name | GNS ransomware |
| Type | File locking virus, crypto-malware |
| Malware family | Dharma, also known as Crysis |
| Distribution | Malicious actors can use several different techniques, although the malicious payload is mainly delivered via spam email attachments, insecure Remote Desktop connections, or software cracks |
| File extension | .GNS, although a full extension looks as follows: .id-ID.[[email protected]].GNS |
| Ransom note | FILES ENCRYPTED.txt and a popup window titled [email protected] |
| Contact | [email protected] and [email protected] |
| File decryption | There are no known tools that could recover your files encrypted with the latest versions of Dharma. However, you might want to try using built-in Windows restoration points or third-party recovery software |
| Malware elimination | You should remove the malicious payload with the help of powerful anti-malware tool – we suggest using SpyHunter 5Combo Cleaner or Malwarebytes |
| System fix | Ransomware might damage some Windows system files and configuration settings in a way that would prevent the OS from operating the way it used to. In case you experience crashes, BSODs, errors, and other stability issues, scan your machine with Reimage Reimage Cleaner Intego |
While GNS ransomware can use several different distribution methods, it mostly penetrates machines with the help of social engineering. Believable messages are crafted by malware authors and then delivered to thousands of users. Clipped to such emails are the attachments which hold the payload of ransomware. Hackers behind the strain often use double extensions in order to confuse users and make them believe that they are not opening an executable (.exe) file.
Once such a file is executed, Windows operating system is heavily modified, and several built-in backup systems deleted. This is done to prevent users from recovering from the virus without paying the ransom. In some cases, even GNS ransomware removal might not help when it comes to system performance after the infection is terminated. In such a case, we suggest using PC repair software Reimage Reimage Cleaner Intego, which could help to regain computer stability after malware intrusion.
GNS files virus begins the file encryption process immediately – it looks for pictures, music, videos, databases, MS Office documents, and other types of most commonly-used file types. The process of encryption is swift – and for a reason. In many cases, the data encryption process might begin to slow down the computer, which could make users suspicious and interrupt the process. Thus, ransomware typically encrypts only a few kilobytes of each file.
As soon as the encryption process is finished and the .GNS extension applied, malware does not hide its presence on the system anymore and displays the following information via the pop-up window:
YOUR FILES ARE ENCRYPTED
Don’t worry,you can return all your files!
If you want to restore them, follow this link:email [email protected] YOUR ID –
If you have not been answered via the link within 12 hours, write to us by e-mail:[email protected]
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
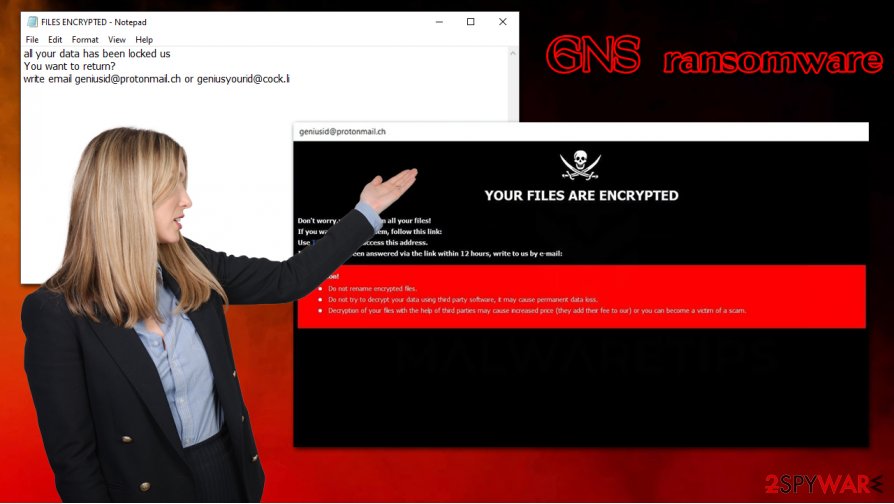

GNS ransomware is a type of computer virus that locks all files on the system and then demands ransom to be paid for their redemption tool
Another file, FILES ENCRYPTED.txt, which can be opened via the Notepad, includes a much shorter description of a ransomware attack:
all your data has been locked us
You want to return?
write email [email protected] or [email protected]
Most security researchers[3] advise not paying the ransom, as it might result in not only data but also money loss. Instead, we suggest you remove GNS ransomware from your system with the help of powerful anti-malware software and then use alternative methods for data recovery – we provide some solutions below.
Should you pay the ransom? GNS files recovery methods
We advise you to take the words of cybercriminals behind the GNS virus with a grain of salt: they claim that other methods of data recovery will result in a complete data loss. This is not true, however, since some alternative methods might actually be successful in GNS virus files recovery.
In case malware failed to delete Shadow Volume Copies and System Restore features, you would most likely be able to retrieve all data without any issues. However, all the modern and working crypto-malware strains are programmed to delete the automatic backups (although this process might fail due to bugs or other reasons).
Another solution is using third-party recovery tools – this option also has a very small success rate, as most of such tools rely on retrieving working copies of files from the hard disk. Note that neither data recovery software, nor anti-malware can remove .GNS file extension (i.e., decrypt current files), as it is not designed for such a purpose.
Finally, paying criminals is your last resort. Before you consider this option, please take points into consideration:
- Crooks might send you a non-working decryptor
- Hackers might not send you anything and completely ignore you
- Payments only fuel the will of cybercriminals to create more malware
- You might be a target of future attacks, as threat actors would know you are willing to pay.
As you can see, the task of recovering GNS files is not that easy. We suggest you keep backups ready in case such unfortunate circumstances happen to you in the future. To protect your machine, use reputable anti-malware, update your operating system and the installed software on a regular basis, and never download software cracks.

GNS ransomware intrusion can be prevented by most of anti-malware solutions
Delete GNS ransomware from your computer and only then attempt file recovery
Many ransomware victims find themselves in a state of disbelief and even shock after they find out that they cannot open their photos, school papers, or a work project. However, panicking doe nothing in such a situation, and handling it correctly is the only way to go forward. If you never had to deal with GNS ransomware removal, it might seem like a very complicated task, however.
Nonetheless, considering you had no backups available, you should copy all the encrypted files before you remove GNS ransomware from your computer. Encrypted data does not store any malicious code within it, so having them on another medium is safe. Likewise, security researchers might develop a working GNS ransomware decryptor in the future.
To delete the GNS file virus from your machine, perform a full system with anti-malware software, although do not get surprised that your files till cannot be opened. As explained earlier, malware termination will not grant you access to locked files. Instead, follow the instructions for alternative data recovery methods below.
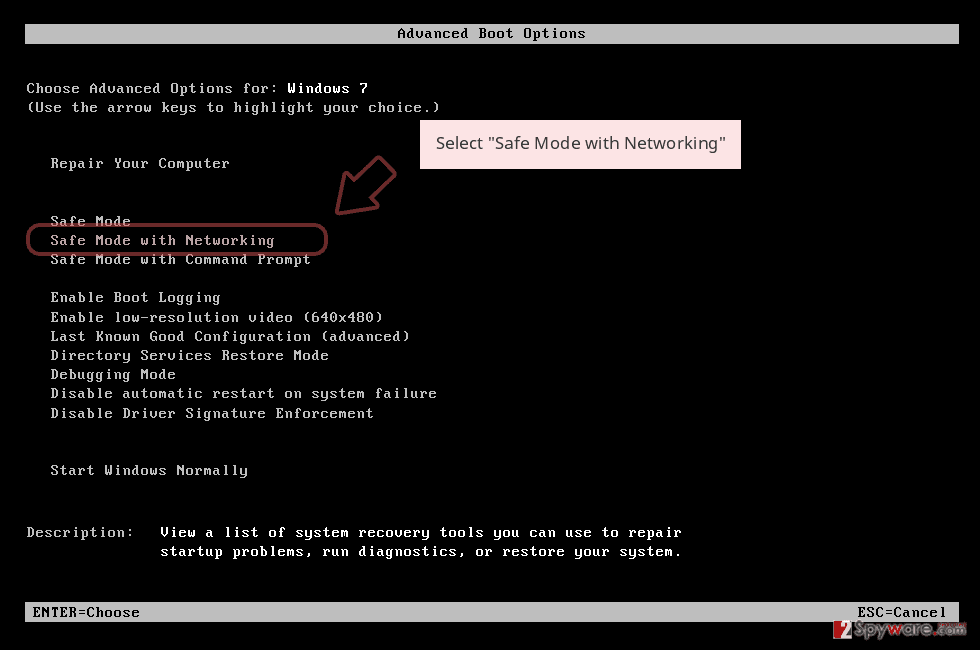
Remove GNS using Safe Mode with Networking
In case you cannot delete the malware in a normal mode, you can access Safe Mode with Networking:
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
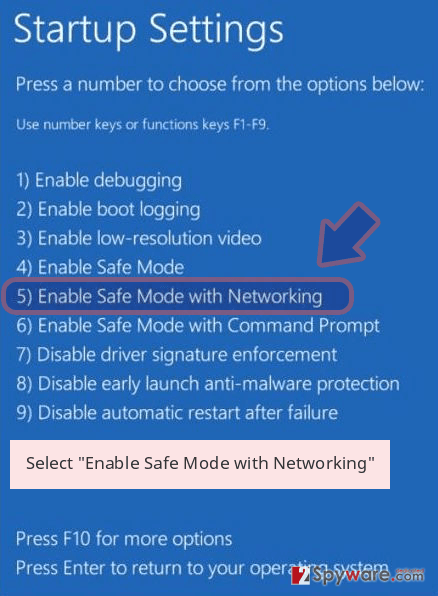
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner Intego or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete GNS removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove GNS using System Restore
System Restore could also help you undo the changes made by ransomware in some cases:
Bonus: Recover your data
Guide which is presented above is supposed to help you remove GNS from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by GNS, you can use several methods to restore them:
Data Recovery Pro might work for you
If you did not use your computer much after the infection, you could try using Data Recovery Pro to recover at least some of your files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by GNS ransomware;
- Restore them.
Windows Previous Versions feature could help you retrieve files one-by-one
This method will only work if automated Windows backups were not erased by the GNS file virus.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
In some cases, ShadowExplorer could save your files
If malware failed to delete Shadow Volume Copies, ShadowExplorer is a great tool to recover your files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from GNS and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner or Malwarebytes
The government has many issues in regards to tracking users’ data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Computer users can suffer various losses due to cyber infections or their own faulty doings. Software issues created by malware or direct data loss due to encryption can lead to problems with your device or permanent damage. When you have proper up-to-date backups, you can easily recover after such an incident and get back to work.
It is crucial to create updates to your backups after any changes on the device, so you can get back to the point you were working on when malware changes anything or issues with the device causes data or performance corruption. Rely on such behavior and make file backup your daily or weekly habit.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware occurs out of nowhere. Use Data Recovery Pro for the system restoring purpose.
This entry was posted on 2020-07-30 at 09:17 and is filed under Ransomware, Viruses.

