M0rphine ransomware – a dangerous file encrypting malware that will attempt to extort money from you
M0rphine ransomware is a file locking virus that stems from SatanCryptor family

M0rphine ransomware is a file locking virus that stems from SatanCryptor family
M0rphine ransomware is a cryptovirus that was first spotted by security researcher dnwls0719 in May 2020. Just like other members of Satan ransomware, it uses the AES[1] encryption algorithm to lock pictures, videos, music, documents, databases, and other data held on the target computer. The modified files are not corrupted, but rather locked – they require a unique set of keys to be functional again. Unfortunately, only M0rphine virus authors have access to the decryption tool, but they are not willing to provide it for free, of course.
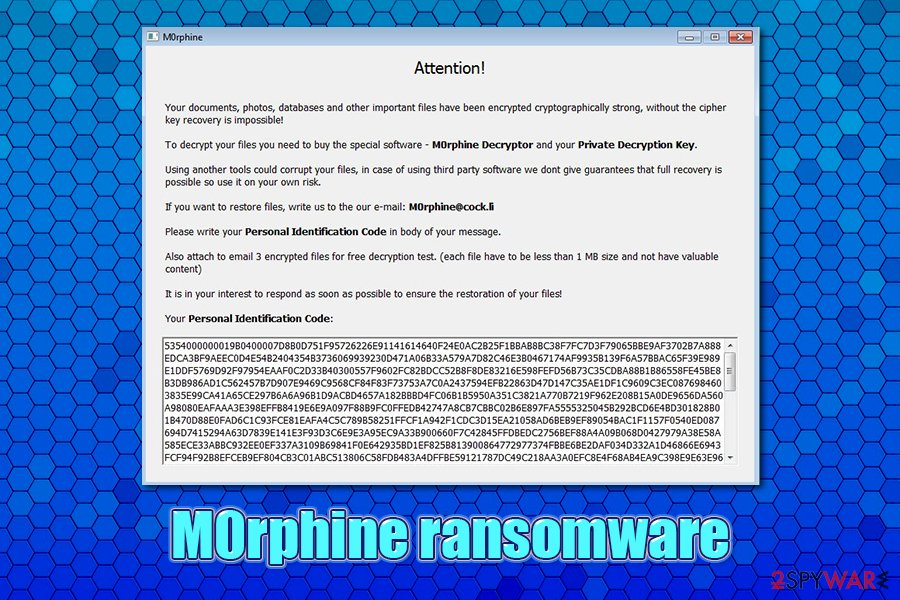
Cybercriminals ensure that users are aware of the M0rphine ransomware infection, as they make malware drop a ransom note # M0rphine Help #.hta, which can be opened as a pop-up window. Another sign of ransomware infection is the markings that are appended on the encrypted files – each of them receives a .M0rphine file extension, although the full name modification includes contact email [[email protected]] and a lengthy ID number. Suchlike modified files may seem unrecognizable and clunky and have their icons missing.
| Name | M0rphine ransomware |
| Type | File locking virus, crypto-malware |
| Family | This malware is a variant of Satan ransomware, otherwise known as SatanCryptor |
| Encryption algorithms | All non-system and non-executable files are locked with the help of AES cipher |
| File extension |
Every file is appended with .M0rphine extension, although there are also other entries affixed to the file name. An example of an encrypted file:
|
| Ransom note | # M0rphine Help #.hta is a file placed on victims’ desktop |
| Contact | Users are asked to write an email to [email protected] to negotiate the price for the M0rphine Decryptor |
| Distribution | Malicious actors can use a variety of methods |
| File recovery | Without backups, there is no secure way of recovering files safely. However, there is a possibility that security experts will find bugs within malware and manage to break its code, which will allow them to create a free decryptor. This does not happen all the time, however; you can try using third-party tools in the meantime instead – we provide the download links and instructions in the recovery section below |
| Malware removal | To eliminate the infection safely, make sure you are using comprehensive anti-malware programs. In case the malware is tampering with the process, utilize Safe Mode with Networking for the job – we explain how below |
| System fix | We recommend using Reimage Reimage Cleaner Intego after ransomware is removed to avoid Windows system reinstallation |
SatanCryptor was first released back in 2017 as a ransomware-as-a-service (RaaS),[2] which meant that its developers are not participating in the distribution process. Instead, they offer to borrow the malicious code to everybody willing on underground hacking forums (which means that distributors don’t have to be sophisticated hackers), in exchange for some profits gained from ransom payments. This technique is very common, and many ransomware strains, including the M0rphine virus, are using it.
There are several methods that the attackers can use to deliver M0rphine ransomware to your computer. Since the family that this malware belongs to is operated as a service, multiple criminal groups can employ different methods for its distribution, for example:
- Spam email attachments or embedded links
- Software vulnerabilities and exploit kits[3]
- Pirated software installers and software cracks
- Fake Flash Player (or other) updates or repacked programs
- Weakly protected Remote Desktop connections, etc.
M0rphine ransomware belongs to the new version of the initial malware, which showed up in early 2020. It uses AES to encrypt data (instead of AES + RSA) like its predecessors and modifies files in the following way: [file name].[orgonal extension].[ID-XXXXXXXXXXXXX].[[email protected]].M0rphine. Suchlike files can no longer be opened, as they require a special key that is held hostage by cybercriminals.
However, file encryption is just one of the few tasks that the M0rphine file virus performs, as it also modifies the Windows system significantly, e.g., changes the registry database entries, deletes Shadow Volume Copies, creates new processes, drops many malicious files, etc. Note that these modifications might not go away with M0rphine ransomware removal – you should employ special repair tools like Reimage Reimage Cleaner Intego for the job.
Once the infection of M0rphine virus is settled, it drops the following ransom note:
Attention!
Your documents, photos, databases and important files have been encrypted cryptographically strong, without the cipher key recovery is impossible!
To decrypt your files you need to buy the special software – M0rphine Decryptor and your Private Decryption Key.
Using another tools could corrupt your files, in case of using third party software we dont give guarantees that full recovery is possible so use it on your own risk.
If you want to restore files, write us to the our e-mail: [email protected]
Please write your Personal Identification Code in body of your message.
Also attach to email 3 encrypted files for free decryption test. (each file have to be less than 1 MB size and not have valuable content)
It is in your interest to respond as soon as possible to ensure the restoration your files!
Your personal Identification Code:
Naturally, many users are quite shocked when they see ransomware infection for the first time. Suddenly, none of their files can be opened, and they can also see a weird message talking about this unfamiliar topic. While it is understandable that M0rphine ransomware infection might seem like a disaster, there is no need to panic, as the situation will not change by doing so.
What you need to do right now is to figure out how to remove M0rphine ransomware safely, restore your Windows machine to normal, and only then ponder about data recovery. To eliminate the infection, you will have to scan your device with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful ant-malware. Note that none of these actions will recover M0rphine ransomware encrypted files, however.
M0rphine ransomware is a data locking malware that encrypts all data on the system and then demands ransom to be paid for decryption software

M0rphine ransomware is a data locking malware that encrypts all data on the system and then demands ransom to be paid for decryption software
Ways to avoid ransomware infections
Ransomware-as-a-service operators hire multiple different groups to assist the delivery to users. For this reason, there might be several different methods the attackers use to spread the virus. However, one of the most known tactics that are used by many different actors is spam emails, otherwise known as malspam.
Initially, the phishing emails are created by the attackers and then sent out to thousands of users using botnets or other tools. While some scam emails might look fake and have multiple grammar mistakes (which hints to deception), some emails are compiled exceptionally well, and it is sometimes difficult to differentiate between a legitimate message and a fake one.
In many cases, cybercriminals employ familiar logos, hyperlinks, buttons, and other attributes to make the email believable. Also, they usually use an email address that resembles a legitimate one, so victims would not notice it. For that reason, you should always analyze the sending address, and ensure it is legitimate before performing any other actions.
The payload is usually carried out within the attachment, which can be in different file types. For example, macro-laced MS Office documents are often employed in order to trigger the infection routine. Thus, be very careful when opening email attachments, they typically serve as the main attack vector. If you are in doubt, employ tools like Virus Total or anti-malware software to scan the document.
Also, it is important to protect your machine with a reputable anti-malware, backup all your files on a regular data, and practice safe browsing habits.
M0rphine ransomware elimination
As previously mentioned, M0rphine ransomware removal will not return your files into their working state. Nevertheless, the process is mandatory, as malware will keep corrupting the incoming files until it is terminated from the PC. For that, we highly advise using a reputable anti-malware tool and then perform a full system scan. If the M0rphine virus is tampering with your security software, you should access Safe Mode with Networking and perform a scan from there.
M0rphine ransomware infection can be prevented by using a reputable security program

M0rphine ransomware infection can be prevented by using a reputable security program
Once you remove M0rphine ransomware, you can begin to think about data recovery methods. Unfortunately, there is no known secure and 100% working method to recover the encrypted files if no backups were retained. While paying cybercriminals might seem like an option, keep in mind that they might simply keep the money and never message you back – you will end up losing your data and the payment, receiving nothing in return.
Thus, we recommend following alternative methods for data decryption – you can use third-party recovery programs or built-in Windows features. While chances are low, it is possible that you will be able to recover at least some of your files.
This entry was posted on 2020-05-11 at 04:47 and is filed under Ransomware, Viruses.

