njRat is a multi-functional Remote Access Trojan that can log keystrokes and disable anti-malware software on the host machine

njRat, also known as Bladabindi, is a Microsoft .NET framework-based Remote Access Trojan and a sophisticated backdoor that possesses a variety of capabilities which allow the attacker to take over the computer remotely. Because of its large scale, authors of the Trojan used a variety of distribution methods to deliver njRat, including malspam campaigns, fake updates, drive-by downloads, etc.
The malware, which was first spotted back in 2013, is of Arabic origin (developed by لهكر جوكر 1337) and mainly targets Middle Eastern users, although surges of the infection were also seen in other countries, such as India. njRat Trojan was used by various cybercriminal gangs to launch cyberespionage campaigns, control botnets, and deploy targeted distributed denial of service (DDoS) attacks.
Anyone can get infected with the njRat malware, so you should be vigilant, as the infection can lead to money loss, data corruption, installation of other malware, and further compromise. Make sure you perform regular computer scans so you would be able to remove njRat Trojan immediately upon detection.
| Name | njRat |
| Also known as | Bladabindi, Njw0rm |
| Type | Remote Access Trojan (RAT) |
| Targets | Mainly Middle East |
| Functionality | Can allow the attacker upload additional malware, harvest variety of information, take screenshots, log keystrokes, steal browser data, etc. |
| Distribution | Spam emails, fake updates, drive-by downloads, software cracks, VoIP applications, etc. |
| May be distributed with | Lime ransomware |
| Symptoms | Trojans usually show no symptoms, but some users might notice crashing applications, errors (0x000000F4), increased amount of advertisements, suspicious processes running in the background, modifications of Windows registry, etc. |
| Termination | Use reputable anti-malware software and scan your machine fully in Safe Mode with Networking to remove njRat |
| System repair | You can clear malware damage by checking the machine using Reimage Reimage Cleaner Intego or a system repair tool hat indicates corrupted files or affected system functions |
It is natural that malware like njRat, which runs for over six years now, is continuously being improved and new versions added. Despite the wide array of variations, this Trojan is something really nasty that most of the users should avoid in the first place – the infection can put their online safety at risk and cause extensive harm to the host machine.
njRat is equipped with an array of capabilities that are needed for the RAT to perform the required activities on the infected machines. The Trojan can perform the following:[1]
- Steal a variety of sensitive information, including Chrome/Firefox/Opera/Internet Explorer stored passwords,
- Record video using the PC camera and take screenshots;
- Log keystrokes that are typed by the infected user;
- Restart the computer;
- Upload other malware;
- Update itself;
- Download and run files;
- Modify or create new keys in Windows registry;
- Prevent detection by using .NET obfuscators, etc.
njRat is continually communicating with a Command and Control server that is only accessible to the hackers. By establishing the connection, the RAT is capable of sending the collected data directly from %TEMP%\[variable name].exe.tmp file to the remote server.
As evident, the threat consists of a variety of features that can serve for malicious actors in many ways. Unfortunately, njRat removal might be hindered by its obfuscation techniques, as malware is known to crash the computer with the error code 0x000000F4 as soon as attempts to terminate it are made.
To avoid such a scenario, the infected users should access Safe Mode – load Windows in secure mode, which temporarily disables the functionality of njRat malware. Then, scan your machine with a powerful security application to terminate the infection and revert all the damage done to the system files with software like Reimage Reimage Cleaner Intego.

njRat is sophisticated malware strain employed by various cybercrime gangs to gain unauthorized access to millions of computers worldwide

njRat is sophisticated malware strain employed by various cybercrime gangs to gain unauthorized access to millions of computers worldwide
njRat authors conducted multiple campaigns over the years
njRat Trojan is capable of performing a variety of malicious tasks on victims’ machines, and that makes it a desirable target for many cybercrime gangs. Over the years, various malicious actor groups employed multiple distribution techniques to deliver the Trojan to as many victims as possible. Below are a few examples of multiple occasions when njRat caught the attention of multiple media outlets worldwide.
Microsoft shuts down over 20 domains to battle njRat malware
In July 2014, njRat hit Indian users, infecting them via contaminated USB drives or was delivered by other malware already residing in the computer.[2] The malware was able to acquire a safe network domain ID to bypass the host machine’s firewall and enter it uninterrupted. This variant of njRat was concentrating on harvesting users’ keystrokes and using computer camera, later sending the data to the remote server for the attacker to exploit.
During that time, Microsoft initiated actions to stop the infections in India and other parts of the world. The industry giant asked Nevada court to acquire the permission to shut down over 20 domains that were related to njRat distribution and belonged to Dynamic DNS services provider no-ip.com. In the attempt, Microsoft shut down four million websites
njRat malware was delivered via spam email during 2015
In early 2015, njRat was spotted making rounds via phishing emails that came from the file hosting service site eDisk.eu.[3] The hackers copied the legitimate email just perfectly, using the correct markings and logos, claiming that a file was shared by the user “The Driver” – the message states:
File link
Good day,
this email brings you eDisk – online digital file storage.User The Driver (A Professional Gamer) Sends you link for files stored on eDisk:
NFSW_Car_Charger.exe – [download link redacted]
best regards,
eDisk team
Once the executable is downloaded, the payload of njRat is distributed, and the host computer is infected.
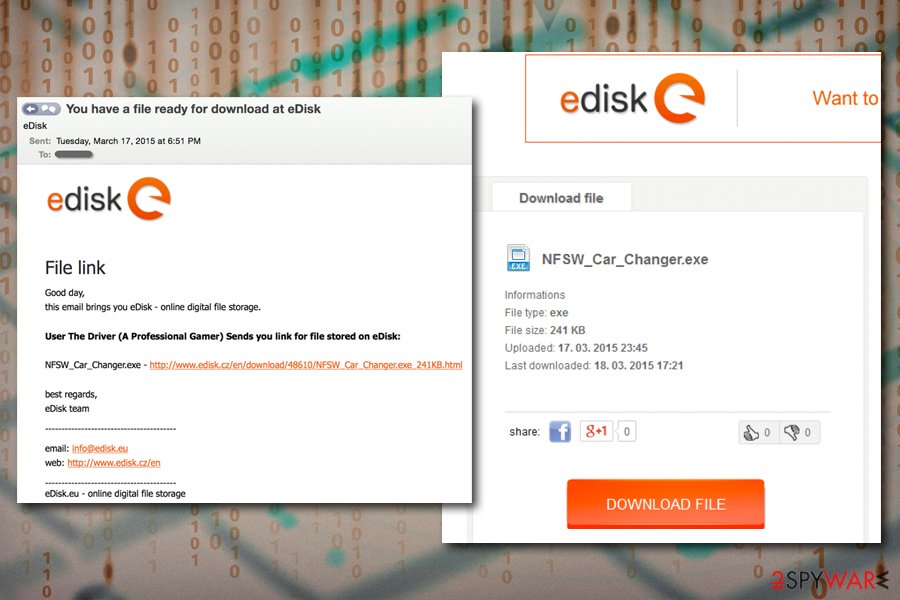
At some point njRat was actively being distributed with the help of malicious executable link embedded in a spam email

At some point njRat was actively being distributed with the help of malicious executable link embedded in a spam email
VoIP application Discord used to deliver njRat to gamers
Discord malware has been spreading as soon as the platform gained popularity among the gaming community. In 2016, the VoIP application was used to deliver various Remote Access Trojans to platform’s users, one of which was the infamous njRat.
Some malware authors create their own Discord servers where they embed the never-expiring links into the chat. Other attackers simply join servers they were invited to and post the links or attachments there. The malicious files usually had seemingly innocent names, such as “FreeMemes.exe,” which was part of an elaborate social engineering technique to make users click on the malware-laden links.
Among the other sensitive data that njRat can harvest, it was also employed to steal login details from platforms like Steam, or online games. In response to Symantec’s findings,[4] Discord immediately removed the malicious links and employed a scanner that would prevent such malicious links from being uploaded to the platform servers.
Discord is one of the most popular chatting applications on the market, and njRat was spotted being delivered via the platform with the help of phishing links and malicious attachments

Discord is one of the most popular chatting applications on the market, and njRat was spotted being delivered via the platform with the help of phishing links and malicious attachments
ISIS website hijacked to make visitors download njRat
In March 2017, the so-called Islamic State’s propaganda website Amaq was hacked by the njRAT distributors.[5] Hackers injected a script into the site that shows a fake Adobe Flash update prompt for anyone who visits. Flash is outdated software full of flaws,[6] and has been abused by various malicious actors for years to spread the malware.
The malicious file that would be downloaded by visitors was named “FlashPlayer_x86.exe” not to arouse any suspicions. Soon after the execution, users’ machines would be infected with the notorious info-stealer njRAT. During the time, it is estimated that around 600 people clicked on the malicious in one day alone, so the scope of infections might be potentially enormous.
Experts say that the attack was not necessarily planned against ISIS, but was rather a generic attempt to infect users with malware for personal gain. After the incident, Amaq moved to a different domain to prevent further contamination of the site.
njRat Lime edition
In 2018, security researchers from Zscaler discovered a new variant of njRat that was capable of stealing cryptocurrency wallet funds.[7] As usual, the RAT was employed to steal sensitive information from users, establish the dynamic DNS to connect to its Command and Control server, and use various obfuscation techniques to avoid detection.
Besides the info-stealing component, njRat now came with a file locking capability, as it employed Lime ransomware to use AES cipher for data encryption. Soon after the infiltration, users are asked to pay 0.10 Bitcoin into a provided wallet for file recovery. However, paying criminals is never advised, mainly because a free decryption tool is available that would allow victims to recover data for free.

In 2018, malicious actors delivered Lime ransomware along the main payload of njRat

In 2018, malicious actors delivered Lime ransomware along the main payload of njRat
Prevent malicious Remote Access tools from entering your machine
Remote Access Trojans are among one of the most dangerous malware infections around. These tools allow the attackers to take over the machine remotely, upload other malware, steal the most sensitive data, including the device into a wide botnet that can be used for malspam, DDoS attacks, etc.
In other words, RAT allows malicious actors to take over your machine, and you might not even know about it, as there are rarely any symptoms that accompany the infection. Therefore, it is vital to protect yourself from such an enormous threat and never allow it into your computer in the first place. Security experts[8] advise following these guidelines when it comes to cybersecurity:
- Install comprehensive security software and enable the firewall;
- Patch your operating system with security updates without postponing;
- Enable automatic updates for all the installed software;
- Do not download software cracks or pirated versions of paid programs;
- Never open email attachments that ask you to enable macro function;
- Use strong passwords and never reuse them;
- Protect Remote Desktop connection adequately – do not use a default port;
- Enable ad-block;
- use two-factor authentication where possible;
- Backup your personal files regularly.

Spam email attachments remain one of the most prominent malware distribution methods, including the njRat RAT

Spam email attachments remain one of the most prominent malware distribution methods, including the njRat RAT
Remove njRat from your computer to avoid identity theft, money loss, and other unforeseen consequences
To remove njRat virus from your machine, you need to know it is in your machine in the first place. Unfortunately, Trojans are very deceptive and use multiple obfuscation techniques – they can even avoid or disable security software. If you apply regular computer scans, you should be safe and not affected by malware.
Nevertheless, if you have no anti-malware software installed and exercise unsafe online behavior – you are at significant risk. You should download reputable security software and fully scan your device. Be aware that some AV engines might not be able to perform njRat removal, as new variants emerge regularly. Thus, you might need to perform system scans several times, using different tools like SpyHunter 5Combo Cleaner or Malwarebytes.
Also, since AV tools can terminate the malware, but files damaged in some system folders remain affected run Reimage Reimage Cleaner Intego for repair purposes. To prevent njRat RAT from tampering with security software or additional programs, you should access Safe Mode with Networking as explained below.
This entry was posted on 2020-05-04 at 08:46 and is filed under Trojans, Viruses.

