Nypd ransomware gains access to host machines in order to lock personal files and increase income from selling file decryption keys

Nypd ransomware is a cyber infection that is currently actively distributed via infected download links of VST plugin, as well as spam email attachments[1]. It’s a member of the STOP/Djvu ransomware family, which is one of the biggest file-encrypting ransomware gangs on the marketing bringing together more than 200 variants.
If the Nypd virus payload is launched, it manifests itself by locking all personal files on the machine, including personal photos, Microsoft Office documents, videos, and others. It leaves non-system files untouched, though some of the core Windows components, including registry entries and boot up files. It uses the AES encryption model and appends the .nypd file extension to the personal users’ data.
Criminals behind this malware clarify the situation by presenting their victims with the _readme.txt ransom note, which can be found on the desktop, as well as other non-system Windows folders. Crooks demand their victims to pay the $490/$980 ransom payment within 72 hours, but first, they have to email them via [email protected] or [email protected].
| Name | Nypd |
| Type | Ransomware or file-encrypting malware |
| Geneology | It’s a variant of the STOP/Djvu ransomware family |
| Distribution | According to users, this virus is actively distributed via infected software download links (e.g. VST plugin) on peer-to-peer networks and spam email attachments. However, it may also be pushed via unprotected RDPs, so admins should ensure a strong password protected service |
| File extension | The ransomware appends the .nypd extension to encrypted files |
| Ransom note | _readme.txt |
| Contact email address | [email protected] or [email protected] |
| Ransom | Djvu classic – $490 if the victim pays the ransom within 72 hours. Later, the price for the decryptor gets doubled – $980 |
| File decryption | Djvu versions launched after August 2019 can only be decrypted if an offline key is used. In this case, victims can rely on Emisoft’s STOP decryptor. |
| Virus removal options | There’s only one away to remove Nypd ransomware virus – restart Windows in Safe Mode and run a full scan with a robust antivirus program |
| Windows repair is needed upon ransomware attacks. For recovery of Windows registries, startup processes, and other system components, try using Reimage Reimage Cleaner Intego repair tool. | |
The Nypd ransomware is a clone of other Djvu variants launched recently (Zipe, Nlah, Zwer, Pezi, etc.). Upon infiltration, it restricts user’s access to most of the personal files stored on the machine using the .nypd file virus marker. Up until August 2019, criminals behind Djvu ransomware have been using offline IDs for encoding people’s data, so cybersecurity experts managed to crack the code down and represented the victims with a free decryption software known as STOPDecrypter.
However, since September last year, the Djvu ransomware has been improved and all the new strains generate online IDs that cannot be decrypted without paying the redemption. If you received an ID number, which has the t1 compound at the end of the key, it means that the virus is using offline keys[2] and you can use free decryption software upon complete Nypd ransomware removal.
If, however, the virus locked your files with .nypd file virus using an online key, there are not many options to recover your files. You can either pay the criminals or remove the ransomware and try alternative data recovery options, such as data backups or third-party software.
The new .nypd ransomware manifests its presence on the machine right upon infiltration. Victims can hardly feel the symptoms of PC’s hack during the first infection phase because the virus functions in the background to take control of the system.
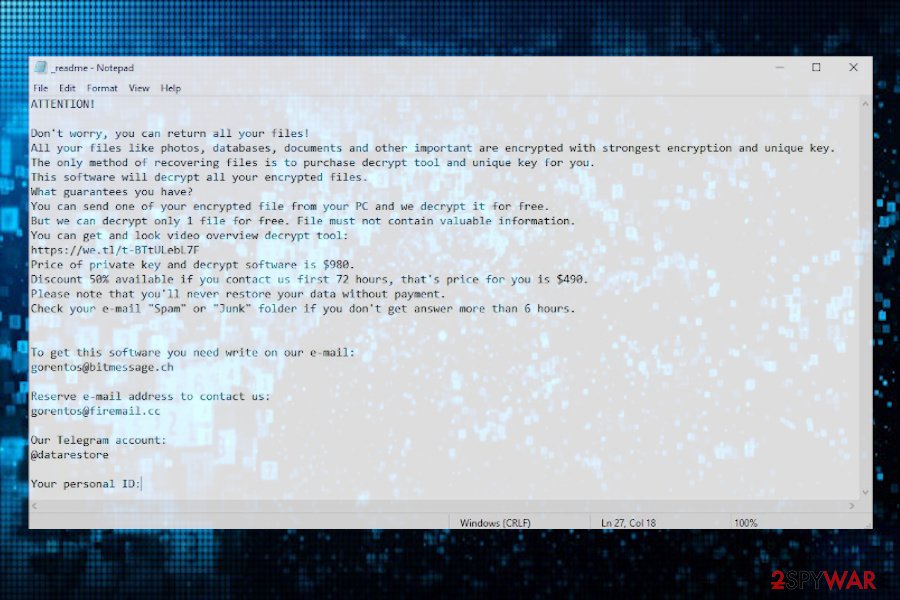
During the second phase, the system may be automatically rebooted. Upon that, all personal files are loaded with the novel .nupd file virus extension, which prevents the data from being opened or otherwise used. The whole information about an attack can be found in the _readme.txt file, which contains the following information:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-dIIHZji8hl
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]
According to LosVirus.es[3], people should not pay the ransom for Djvu managers. These guys are not worth any financial support. The best option in this unpleasant situation is to remove Nypd ransomware virus using SpyHunter 5Combo Cleaner, Malwarebytes, or similar antivirus program and then apply data recovery tools, for instance, Data Recovery Pro.
Check whether .nypd virus files can be recovered

Nypd ransomware restricts people from accessing their personal files

Nypd ransomware restricts people from accessing their personal files
In this case, NYPD is not an abbreviation of the New York Police Department, so don’t get confused. If you see your files locked by .nypd extension, it’s obvious that your machine is hacked by a ransomware virus. As we have pointed out above, this file-encoder is the latest variant of Djvu ransomware, so there are very few chances that you will be able to get your files back without paying for the criminals unless you have data backups.
The most recent versions of this data locker are known for using online IDs, thus leaving the victims helpless. However, since this latest variant hasn’t yet been anatomized, you can check whether your ID is online or offline by yourself. For this purpose, navigate to the C: drive and look for the SystemID.txt or PersonalID.txt entry. Open the file and check whether any of the entries listed ends up with the t1. In case you found at least one entry ending with the t1 suffix, then try to download Emsisoft’s decryption tool to recover .nypd files.
In case it turns out that the Nypd ransomware virus is using online IDs and no free decryptor is capable of breaking it down, then try taking advantage of alternative data recovery means:
- If you have data backups, then there’s nothing to worry about. Remove Nypd virus from the system and recover the files using the backups.
- In addition, you can try to export locked files using Shadow Volume Copies or Windows Previous Versions feature.
- Upon ransomware removal, take advantage of third-party data recovery tools, such as Data Recovery Pro. Although they may not be capable of retrieving the whole package of .nypd files, you may get back at least a part of important documents.
Fake Nypd decryption software can encrypt already encrypted files
At the beginning of June 2020, cybersecurity experts started sharing the warnings about a fake Djvu decryptor. Criminals are taking advantage of the Djvu victims who are looking for a solution to get their files back without paying the ransom to criminals.
Crooks started spreading a malicious piece of software on various channels, including some underground forums and some third-party download websites claiming that the decryption tool has been found capable to unlock .nypd virus files and other Djvu versions that are using online IDs.
IMPORTANT: do not fall for downloading free Nypd decryptor from shady sources because you can end up with another ransomware on your machine. It has been found that the fake decryption tool carries Zorab ransomware payload, which once launched double encrypts encrypted files. Consequently, Djvu file virus is replaced by .zorab extension appendixes and the victims get a new ransom note called –DECRYPT–ZORAB.txt.ZRB.
Although it’s not yet clear whether it’s possible to recover double encrypted files, experts presume that it may be much difficult to ever the changes.

Nypd ransomware is the latest variant of Djvu family

Nypd ransomware is the latest variant of Djvu family
Do not rely on shady download sites that promote pirated software
The members of this infamous ransomware group are extremely prevalent for several years already. The reason for that – sophisticated distribution techniques applied. In most of the cases, hackers inject virus payloads into the links for downloading pirated or untrustworthy third-party software (e.g. cracked Virtual Studio Technology plugins).
Alternatively, people can get infected with a file-encrypting virus on P2P and torrenting sites. Hackers can easily participate in file-sharing websites as registered users, who may offer software cracks for Adobe Acrobat, Photoshop, and others. Although bypassing license restrictions may be fun for users for as long as their personal files are not locked.
Another perfect medium for hackers to exploit is spam email messages. Since people cannot handle their curiosity, criminals keep inventing appealing spam campaigns, such as Covid-19 protection measures or Black Lives Matter anonymous voting. Thus, every time your inbox gets a new email message from an unknown sender and you are seduced to open the attachment, check for grammar mistakes, google the sender and think twice before opening it. If the email requires enabling Macros, it’s an immediate sign that you may be on the verge of launching ransomware.
Get rid of Nypd ransomware and proceed with file recovery options
Nypd virus might not only cause permanent file loss but also trigger serious Windows system malfunctions. Even more, it may download a malicious trojan virus on the system as a secondary payload, thus exposing you to a high risk of identity theft and money losses.
There’s only one option for Nypd ransomware removal, i.e. access Safe Mode with Networking and enabling the scanner of a robust antivirus program. There are multiple malicious processes that belong to this ransomware (e.g. dfile.su[4]), which cannot be quarantined manually in any way.
Once you successfully remove Nypd virus, launch a scan with Reimage Reimage Cleaner Intego repair tool to fix the damage that the virus initiated on Windows registries and other system components. Finally, when the malicious entries are gone and the system is fully functional again, try to recover the data that have been locked.
