Pykw is a cryptovirus that adds the .pykw file extensions to encrypted files and urges victims to pay a ransom in Bitcoins

Pykw is the name of a malicious application that corrupts people’s personal files stored on the PC once it gets installed. It has an in-built AES[1] or another encryption algorithm, which uses a sophisticated mathematic cipher to restrict users’ access to their data, which cannot be unlocked without a decryption key.
The goal of the Pykw ransomware is to prevent users from accessing the most essential files and then demand them to pay the ransom for the functional decryptor. Such viruses are known as crypto-extortionists, ransomware, file-encoders, and similar names. At the moment, this particular virus is circulating on the Internet via obfuscated files attacked to pirated software or spam email attachments. Thus, experts urge people to restrain from downloading cracks, such as Adobe Acrobat or Photoshop. Besides, do not open emails that have .ZIP, .EXE, .PDF attachments named something like “Order confirmation”.
Genealogically, Pykw ransomware virus belongs to the huge STOP/Djvu ransomware family. Some of the noteworthy members of this gang are Zipe, Tabe, Zwer, Nlah, Kkll, and the rest of 230 variants in total. The current version marks corrupted files with the .pykw file extension and drop a _readme.txt file as an information “leaflet,” which demands victims to pay the ransom $480/790 in Bitcoins and then contact ransomware managers via [email protected] or [email protected] emails.
| Name | Pykw |
| Family | STOP/Djvu |
| Classification | Ransomware |
| Ransom note | _readme.txt |
| Contacts | [email protected] or [email protected] |
| Symptoms | Slow PC, inaccessible personal files, all locked files marked wit .pykw extension, ransom note present on the system |
| Distribution | The ransomware can be disseminated in many ways: spam email attachments, unprotected RDPs, pirated software, cracks, keygens, exploits, etc. |
| Decryptable? | No. Unlike Djvu versions launched before August 2019, the current variants are based on online keys that cannot be cracked without paying the ransom |
| Possible decryption methods | Although there’s no official decryptor, victims are not recommended to pay the ransom for criminals. Instead, try to recover .pykw files using alternative methods, including backups, third-party data recovery tools, Volume Shadow Copies. Besides, you can give a try for a free Djvu decryptor that is used for unlocking older Djvu variants. There’s a possibility that it will decrypt at least a part of compromised files |
| Removal | Ransomware should be eliminated with a powerful anti-virus program. NOTE: the virus can block anti-virus tools, so restart the machine into Safe Mode with Networking |
| The system’s performance may significantly decrease upon ransomware installation. Therefore, we recommend using Reimage Reimage Cleaner Intego program to optimize the system | |
Djvu ransomware family is regularly augmented. The new variants emerge every week, so the emergence of the Pykw virus has been expected. This version does not deviate much from its ancestors:
- It is distributed via malicious spam email attachments and software cracks in particular;
- Upon infiltration, it stops many Windows system processes from running, including anti-virus;
- It launched an AES or another cipher that scans the machine for compatible file styles (over 200 extensions) and locks all of them using .pykw extension;
- Victims get the _readme.txt note, which contains instructions on how to pay the ransom (only Bitcoins are accepted);
- Those who pay the ransom within 72 hours can use a discount, i.e. the ransom size is double dropped to $480 instead of $790;
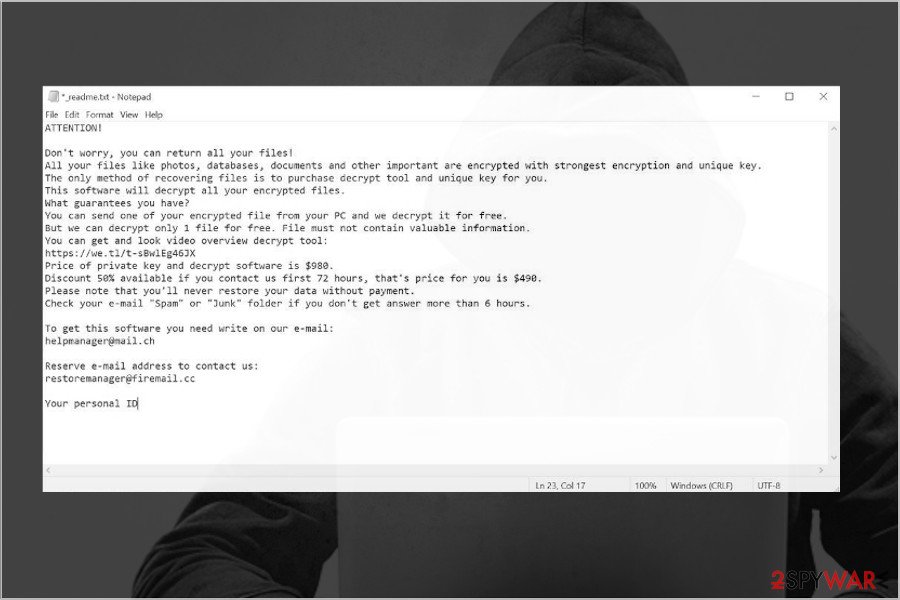
A full Pykw ransom note contains the following information:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-sBwlEg46JX
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]Your personal ID
The Pykw decryptor is not a cheap piece of software. Criminals evaluate it for $780 and, most probably, there are many people who agree to pay this amount in exchange for unlocking important Microsoft Office documents, file archives, photos, and other data, especially when no backups are available.
Pykw ransomware payload can be launched by accident and lead to permanent file loss for people who do not have backups

Pykw ransomware payload can be launched by accident and lead to permanent file loss for people who do not have backups
Nevertheless, it is not advisable to pay the ransom. Experts from the NoVirus.uk[2] team recommends people make a copy of the locked files using a USB stick, hard drive, or cloud storage and then remove Pykw ransomware from the system. It’s important to stress the fact that Djvu ransomware family members are programmed to download AZORult trojan as a secondary payload. The latter may install spying software and start recording keystrokes, take screenshots, and perform other activities to get access to the victim’s bank accounts.
In general, the sooner you perform Pykw removal, the chance of getting a banking trojan and experience further losses will decrease. Please note that paying the redemption for criminals is not a guarantee that a fully functional decryptor will reach you. We recommend you to make copies for the .pykw files and send them to the trustworthy ransomware researchers who are working on the Djvu decryption tool and wait for them to find a way to unlock your personal files.
Until that, we recommend trying alternative Pykw file recovery methods that have been submitted by our security experts. These methods can help you to retrieve separate files. However, do not initiate any file recovery steps before ransomware removal. Once you have backups[3] for the encrypted files, restart Windows into Safe Mode and run a full scan with a professional anti-virus program. The run a scan with Reimage Reimage Cleaner Intego optimization tool to restore your machine’s performance and then start the data recovery process.
Ransomware authors disguise malicious files in popular places, such as P2P networks or shady download sites
Cybersecurity experts stress the fact that the Internet is not a safe place where every content could be trusted. Statistically, dangerous viruses, such as ransomware, trojans, spyware, etc. are typically distributed by means of spam email. Crooks append malicious payload to word documents, zip files, pdf files, etc. and represent them as original content. Usually, these attachments command people to enable Macros to read the content. That’s a catch because Macros enabling means the launch of ransomware payload.
Pykw ransomware virus can be distributed via malicious spam email attachments

Pykw ransomware virus can be distributed via malicious spam email attachments
In addition to spam, file-encrypting viruses are often hidden under hyperlinks and adverts positioned on unprotected networks, such as P2P, online gaming, streaming, gambling, pornographic sites, etc. Thus, clicking on any content presented on suchlike websites poses a risk of getting your files locked.
Another popular ransomware distribution way is pirated files, such as software cracks, game cheats, keygens, license keys, and similar. According to experts and victims’ reports on Reddit[4], Djvu ransomware family members are most frequently distributed this way. Thus, restrain from any illegal online content to protect yourself from cybercrime.
Do not postpone Pykw ransomware removal
Every ransomware victim wonders whether to pay the ransom or not. Although most probably criminals have a fully functional Pykw decryptor, no one can guarantee that upon paying the ransom you will get the key. There’s a huge risk that you will be left with empty pockets and permanently locked files.
Therefore, we recommend you to remove Pykw ransomware virus instead and rely on alternative data recovery options. Do not try to eliminate ransomware manually because it’s not possible. This type of virus enters the machine in packages that consist of tens of malicious processes. Some of them are responsible for stopping Windows processes, the others for rooting into Windows registries, and the others for performing malicious tasks. All these processes can be stopped by rebooting the machine into Safe Mode with Networking and running a scan with SpyHunter 5Combo Cleaner, Malwarebytes, and similar anti-virus tools.
Pykw ransomware virus runs malicious files that suck up CPU and slows the machine down

Pykw ransomware virus runs malicious files that suck up CPU and slows the machine down
After a complete Pykw ransomware removal, the Windows system needs a recovery. Corrupted system files, deleted Windows registries, and altered startup processes can lead to errors, BSODs, and slowdowns. Thus, it’s advisable to optimize the system using Reimage Reimage Cleaner Intego optimization utility.
Remove Pykw using Safe Mode with Networking
Safe Mode disables malicious processes run by Pykw ransomware. Therefore, if you cannot run an anti-virus program while in normal Windows mode, follow these steps:
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
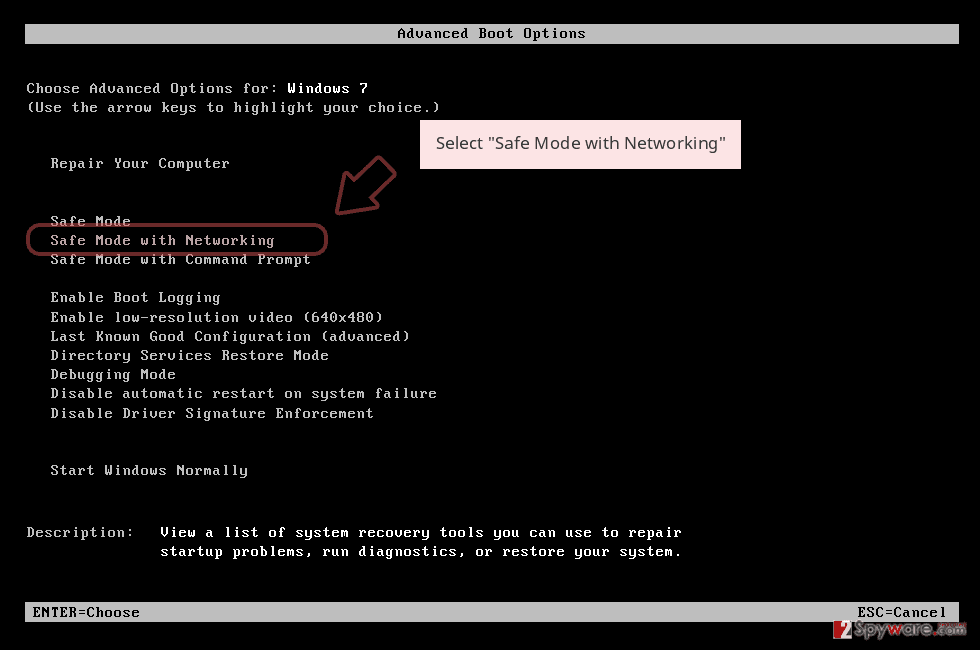
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
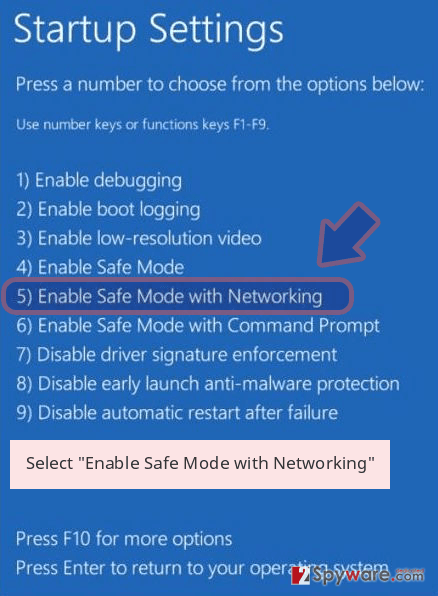
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner Intego or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Pykw removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove Pykw using System Restore
If Safe Mode did not solve the problem, you can try to remove the ransomware using the System Restore feature
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Pykw from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
The instructions provided above explain how to remove Pykw ransomware virus from the system. However, virus removal does not mean the recovery of locked files. Thus, we’ll provide a couple of methods that can help you to decrypt infected files.
If your files are encrypted by Pykw, you can use several methods to restore them:
Run a scan with Data Recovery Pro
To restore .pykw files, try running a scan with a powerful tool known as Data Recovery Pro::
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Pykw ransomware;
- Restore them.
Windows Previous Versions – an in-built Windows OS feature that might help
Windows Previous Versions is a Windows function, which can help to recover your files to the state prior to the ransomware attack. However, this function will work only if you have had the Previous Version feature enabled.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer can help
Experts claim that Djvu versions are programmed to run a command via an elevated PowerShell to delete all Shadow Volume Copies. However, each variant of this family is slightly different, so you can try to retrieve the files using Shadow Volume Copies.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryptor available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Pykw and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner or Malwarebytes
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can’t grant a full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features.
Nevertheless, there’s a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
While much of the data can be accidentally deleted due to various circumstances, malware is also one of the main culprits that can cause loss of pictures, documents, videos, and other important files. Potentially unwanted programs may clear files that keep the application from running smoothly.
More serious malware infections lead to significant data loss when your documents, system files, or images get locked. Ransomware is the one that is focused on such functions, so your device gets useless without access to needed data. Even though there is little to no possibility to recover after file-locking threats, some applications have features for such recovery in the system.
In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
This entry was posted on 2020-06-25 at 02:35 and is filed under Ransomware, Viruses.

