Redl ransomware – file-locking malware that can add random executables to %AppData% or %LocalAppData% folder
Redl ransomware is a ransom-demanding virus that scans Windows computer systems for encryptable data. This malware adds a random executable to %AppData% or %LocalAppData% directories that finds all files and allows the ransomware to lock them with the .redl appendix. Afterward, the malware displays the _readme.txt ransom note that is added to each folder holding encrypted data and also placed on the desktop. Here, Redl ransomware developers urge for contact via [email protected] or [email protected] email addresses and demand a ransom that can go up to approximately $1K in Bitcoin. This malware is one of the latest versions of Djvu ransomware and is currently undecryptable.
| Name | Redl ransomware |
|---|---|
| Category | Ransomware virus/malware |
| Family | Djvu ransomware/STOP ransomware |
| location | The malicious infection can plant rogue files and processes in the Windows Registry and Task Manager sections. Also, the ransomware virus brings an executable to the %AppData% or %LocalAppData% directory that allows the malware to scan the computer for encryptable data |
| Malware | This ransomware virus can easily bring additional malware to the system. These types of viruses are known for spreading AZORult Trojan virus to Windows computers |
| Extension | When files and documents are locked by employing a unique encryption cipher, all the data ends up with the .redl appendix added to the filenames |
| Ransom note | When all the data is encrypted and marked, the ransomware virus starts providing ransom demands via the _readme.txt message that is placed on the desktop and included in each folder that holds encrypted data |
| Demands | The criminals urge for $490 as the starter price and threaten to double the demands up to $980 if the criminals to not transfer the money within 72 hours |
| Additional features | Redl virus might be capable of multiple tasks. The malware can damage the hosts file to prevent users from visiting security-related websites, include specific modules to ensure its startup process, evade antimalware detection, delete Shadow Volume Copies via Powershell commands, etc. |
| Distribution | The most popular ransomware distribution techniques include delivering phishing email messages with infectious attachments or hyperlinks, installing the malware into cracked software and putting it up on p2p networks, injecting the malicious payload into third-party adverts, and hacking vulnerable RDP |
| Removal | To eliminate the ransomware virus, you should use only automatical software. Note that manual elimination might not be an option as you can accidentally miss some crucial steps or leave some malware-laden content lurking on your computer system |
| Fix | If you have found out that the ransomware virus or additional malware has damaged your computer system and some of its objects, you can try repairing them with a tool such as Reimage Reimage Cleaner |
Redl ransomware is a dangerous file-locking parasite that can compromise multiple locations on the Windows computer system, including the Task Manager and Windows Registry. The ransomware can add specific commands such as running within every startup process, searching for encryptable data once in a while, evading antimalware detection.
Redl virus can also try to harden the decryption process for its victims by eliminating or permanently destroying the Shadow Volume Copies via PowerShell commands. Nevertheless, the cybercriminals try to scare and stress the users by claiming that the only method of recovering encrypted data is by paying them money:
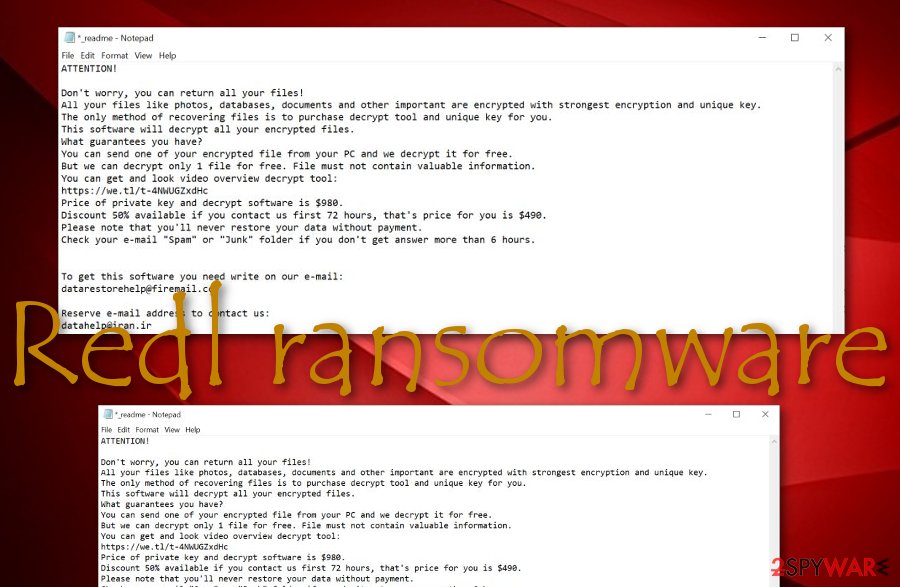
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-4NWUGZxdHc
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]
Redl ransomware urges for $490 as a starter price and threatens to double the ransom amount if the payment demands are not met within 72 hours. Continuously, the hackers urge for Bitcoin cryptocurrency as these types of currency transfers allow the crooks to stay anonymous and untrackable during the entire process and after.
We recommend declining any offers to pay the ransom price as there is a big risk of getting scammed by Redl ransomware developers. These people might wait until they receive the payment and run off with your money by leaving you with no decryption tool or solution at all.
Continuously, Redl ransomware might try to harden the removal process and data recovery process by damaging the Windows hosts file.[1] This way the malicious actors prevent the victims from accessing any types of security-related websites/forums and receiving valuable information.
Redl ransomware is a file-encrypting virus that comes from the Djvu and STOP ransomware families
Nevertheless, Redl ransomware is also a member of the STOP ransomware family. This signifies something dangerous too. All STOP category members are known for their capability to distribute additional malware, especially, AZORult trojan. If this threat appears on your system, you might experience identity theft, monetary losses, and permanent PC damage.
Users’ reports about Redl ransomware attacks have already reached the cybersphere.[2] However, this is only one simple version of Djvu ransomware when there are hundreds more of them lurking for potential victims. This ransomware string has been releasing multiple versions very fastly and seems to succeed in its attempts.
If you are ever infected with this particular malware string, you should remove Redl ransomware ASAP. For this process, employ only reliable antimalware software as manual elimination is not a great possibility in this case. You might miss some crucial steps or accidentally leave some malicious content on your Windows computer.
When Redl ransomware removal is completed, it is time to search for damaged objects that might have been touched by the ransomware virus or additional malicious software. If your automatical software locates any compromised products on your Windows computer system, you can try repairing them with a tool such as Reimage Reimage Cleaner .
Redl malware – a ransomware infection that urges for a ransom price approximately up to $1K in BTC cryptocurrency
The distribution tactics of ransomware viruses
Cybersecurity specialists from NoVirus.uk[3] claim that ransomware infections can travel via multiple sources. However, there are always techniques that are promoted by malicious actors the most. Criminals usually distribute their file-encrypting malware via these types of sources:
- Email spam. The crooks pretend to be from reliable shipping companies such as FedEx and send an order confirmation letter that includes an infected hyperlink or malicious attachment.
- Software cracks. There are many pirating sources such as The Pirate Bay that offer users to download cracked software. However, these types of programs might easily be provided as malware to you.
- Vulnerable RDP. If RDP includes weak password protection or does not have any at all, this increases the possibility of remote attacks and computer infections.
- Malvertising. While you are browsing on the Internet sphere, a lot of advertisements might try to approach you and if you do not employ AdBlock, you will definitely receive the annoying ads. However, some of them might target random users and try to infect them with malware once they are clicked.
Avoiding ransomware attacks is possible
The most important thing to know while trying to avoid ransomware attacks is that you are the one responsible for your computer’s safety and for what is in it. Keeping copies of important files on USB drives or remote servers will slightly decrease the possibility of getting your data encrypted.
Continuously, you should be careful while opening email messages. Always identify the sender, check the content and look for possible grammar mistakes. Additionally, do not open any clipped attachments without scanning them with reliable antimalware software.
In addition, download all of your software only from reliable sources and the official developers to protect yourself from receiving cracked software. Also, secure your RDP with a strong password that includes random symbols and numbers.
Do not forget to act carefully while browsing the Internet sphere too. Avoid clicking on random hyperlinks and advertisements that you are provided with, get an adblocking tool to prevent rogue pop-ups. Last but not least, install reliable security software that will guard you 24/7.
Data recovery solutions for .redl files
Redl ransomware is a dangerous cyber threat because it can lock all types of files and documents, including audio, video, image, word, excel, powerpoint, etc. When this happens, the user is unable to properly access the locked data until the encrypted components are reversed back to their previous states.
However, paying the demanded ransom for Redl ransomware developers might be a big mistake. These people might seek to scam you and run off with your money. Regarding this risk, we recommend declining any suggestions to pay money and trying alternative data restoring methods instead.
Even though the Djvu ransomware decryptor works only for versions that have been released before August this year, you can consider trying DrWeb’s Rescue Pack for $150.[4] This software package includes 2 years of antimalware protection and data recovery software which some users have found to be beneficial.
There are also some other ways to recover .redl files. Go to the end of this article and you will find three other methods that might help you to bring your documents and important data back to their primary positions and allow you to access these components properly again.
Redl ransomware virus removal steps
Redl ransomware removal is an important and time-requiring process. Our recommendation would be to use only automatical techniques while dealing with this type of cyber threat. These malware forms are advanced parasites that can plant malicious content all over your computer system.
Using reliable software should help you to remove Redl ransomware from your Windows machine and get rid of all the additional content that has been brought together with the threat. Continuously, you should check your system for possible damage by performing a full scan with software such as SpyHunter 5Combo Cleaner or Malwarebytes.
If Redl virus or some additional malware has compromised your system in some way, you can try repairing the damage by employing Reimage Reimage Cleaner . Afterward, you can continue with data recovery techniques. Below we have provided some methods that might help you to restore access to your files.
Remove Redl using Safe Mode with Networking
To diminish malicious processes on your Windows computer, boot your machine in Safe Mode with Networking. To complete such a task, use the below-provided instructing steps.
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
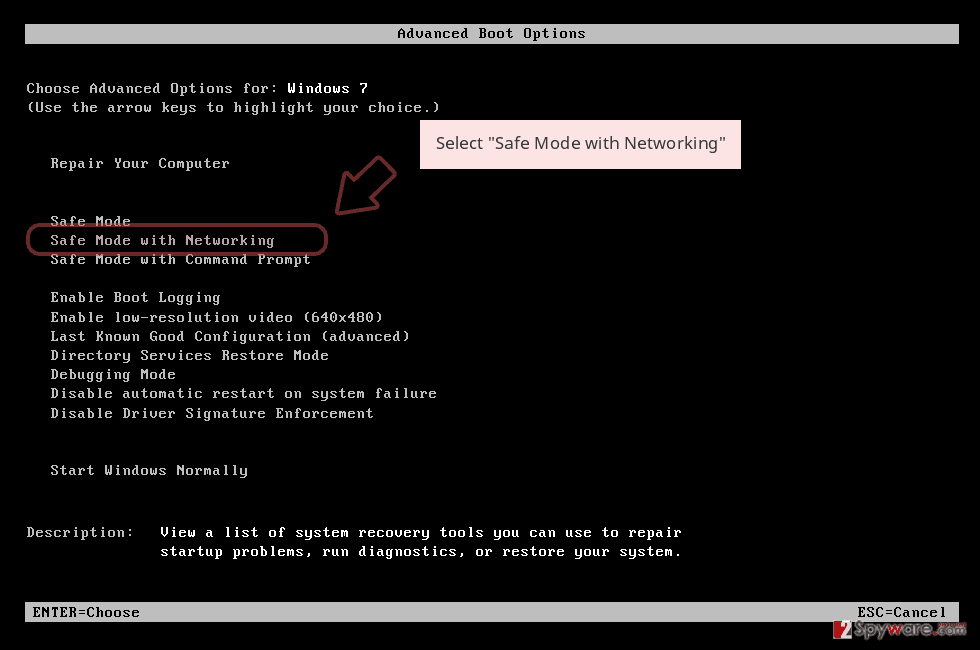
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
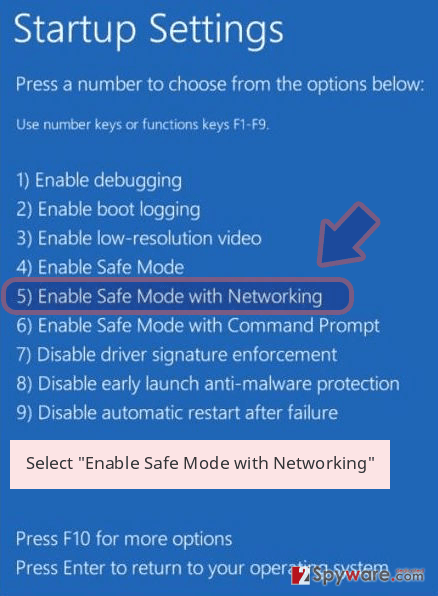
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Redl removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove Redl using System Restore
To disable malicious activities on your PC or laptop, you should activate the System Restore feature. Learn how to do this by completing the following instructions.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Redl from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If you have found files with the .redl appendix, this is an accurate sign that Redl ransomware has managed to touch your data. Rather than paying the demanded ransom and risking to get scammed, try applying some of the following data recovery methods.
If your files are encrypted by Redl, you can use several methods to restore them:
Use Data Recovery Pro and try restoring some of your files.
Employ this software if you are struggling to open any type of file such as audio, video, image, excel, database, powerpoint, word document, etc.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Redl ransomware;
- Restore them.
Try using the Windows Previous Versions feature for data recovery tasks.
This method might appear helpful if you complete all the steps as required. Additionally, ensure that you have booted your Windows computer via System Restore in the past.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer might help you to recover some components.
Try this tool if you have been dealing with encrypted data lately. However, note that this method might not work properly if the ransomware virus has damaged or permanently deleted the Shadow Volume Copies of your encrypted files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, there is no official decryptor available for .redl files.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Redl and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2019-12-23 at 03:05 and is filed under Ransomware, Viruses.

