Revon ransomware – a file locking malware that demands ransom payment in Bitcoin
Revon ransomware is a data locking virus that uses AES encryption algorithm to reach its goals

Revon ransomware is a data locking virus that uses AES encryption algorithm to reach its goals
Revon ransomware is a file locking malware that was first spotted in early April 2020. As a member of the Phobos family, the virus does not differ much from its predecessors – its main goal is to extort money from unsuspecting victims. Once inside the system, it performs several changes to ensure smooth operation and then uses AES to encrypt personal files like pictures, videos, music, documents, databases, and other data. During this process, ransomware marks each of the files with .revon extension, restricting access to users.
To make sure that users find out about what happened, hackers behind the Revon virus also deliver a ransom note info.hta, as well as info.txt. In it, threat actors explain that all personal data is locked and that users need to write them via [email protected] or [email protected] emails to negotiate Bitcoin payment in order to acquire Revon ransomware decryptor. While this malware is currently not decryptable, users should not rush communicating with hackers, as there might be alternative ways to retrieve the locked files.
| Name | Revon ransomware |
| Type | File locking virus, cryptomalware |
| Family | Phobos ransomware |
| Related | Fast.exeXX.exe |
| Encryption method | Revon ransomware uses AES encryption algorithm to lock all non-system files on a Windows machine |
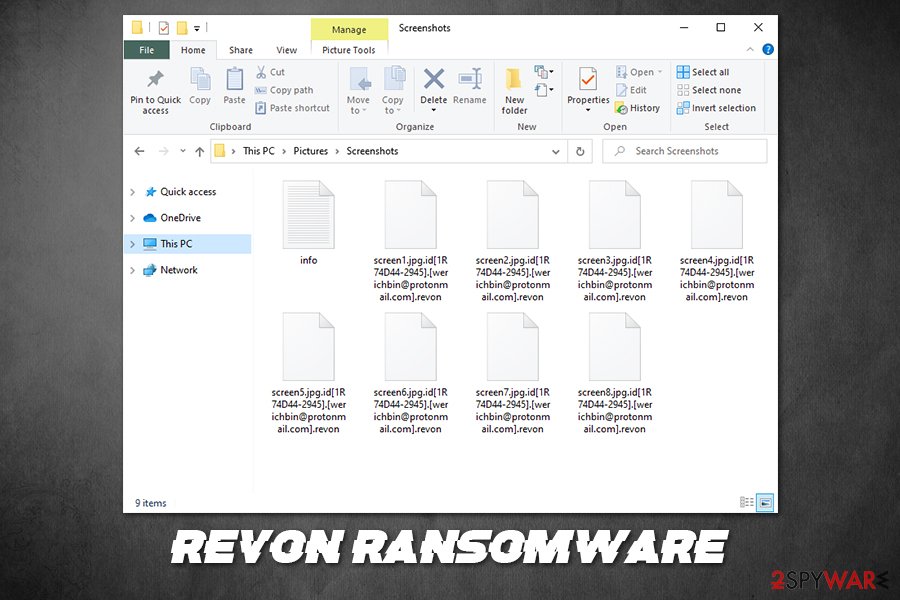
| File extension | All personal files are modified in the following pattern: [file name].[original extension].id[random ID].[email].revon. An example of an encrypted file: picture.jpg.id[1R74D44-2945].[[email protected]].revon |
| Ransom note | Upon successful file encryption, the virus drops info.hta and info.txt on victims’ machines |
| Contact | Malicious actors ask to email them via [email protected] or [email protected] |
| File decryption |
Recovering data without backups is relatively difficult. The remaining options include:
|
| Malware removal | To eliminate the virus, you should scan your system with a reputable security application, such as SpyHunter 5Combo Cleaner or Malwarebytes |
| System fix | In some cases, malware might seriously damage Windows system files, so it will not perform optimally (start crashing, lagging, etc.). If you encounter suchlike problems after you eliminate the malware, you should repair your OS with the help of Reimage Reimage Cleaner Intego |
Phobos is one of the most extensive data locking malware families around and closely resembles the Dharma family, using the same pattern for delivering users ransom notes and also incorporates many operation features, such as encryption algorithm.
Revon ransomware, just as its previous versions Razor, Dewar, and Dever, are primarily targeting public entities and businesses, although regular users could be targets as well. Since targets are mainly companies, the virus is mostly proliferated after the attackers scan the internet for vulnerable Remote Desktop connections and brute-force themselves in. Nonetheless, in case of the Revon virus would target regular users, it could spread in one of the following ways:
- Spam email attachments;
- Web injects;
- Exploits and vulnerabilities;[1]
- Software cracks;
- Malicious ads;
- Fake updates, etc.
In some cases, malware might be installed with Process Hacker 2 – an open-source application used for system monitoring purposes. As a result, Revon could also steal personal information from other apps and web browsers, including login data – users may suffer considerable financial losses. This is why Revon ransomware removal is so crucial at the early stage of the infection.
Before encrypting data, Revon virus performs a variety of changes to Windows machines. For example, it deletes Shadow Volume Copies with the help of “vssadmin delete shadows / all / quiet” command to complicate the data recovery for the victims, establishes Windows registry keys for persistence, gains access to external drives (such as USB flash or external hard drives), as well as networked resources such as NAS.
Once the preparations are complete, the Revon virus begins the encryption process with the help of a symmetric encryption algorithm AES.[2] This means that the same secret key is used to lock up the data and is later sent to a remote Command & Control server controlled by the attackers.
Revon ransomware is crypto-malware that belongs to Phobos virus family

Revon ransomware is crypto-malware that belongs to Phobos virus family
Due to this, blackmail is possible, as users need to retrieve it in order to decode all files. Nonetheless, there were confirmed cases of victims not receiving a decryption tool after a Bitcoin payment, hence users are not recommended contacting threat actors with the hopes for the Revon ransomware decryption tool.
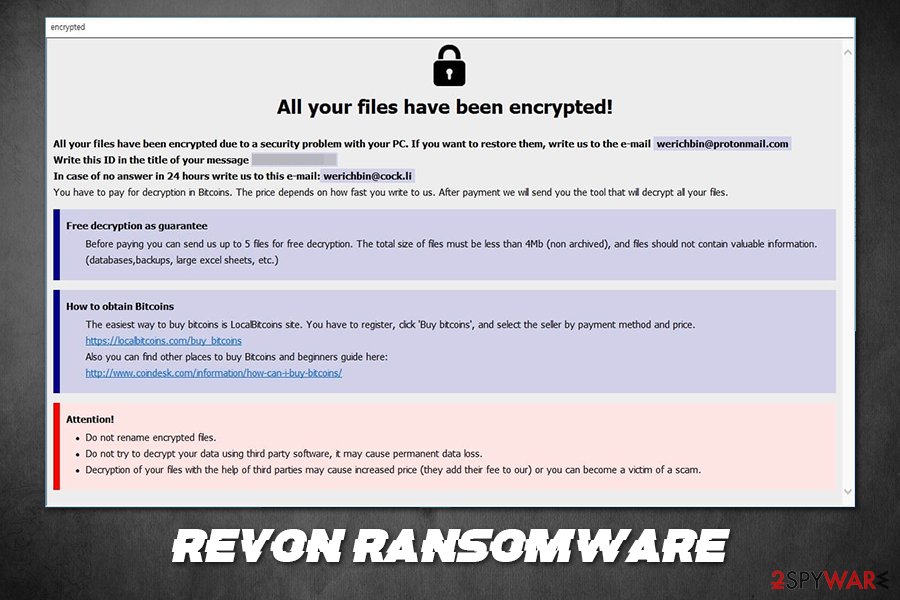
After locking up the data, users can access an Info.hta and Info.txt file which explains users about data recovery process:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID in the title of your message 1R74D44-2945
In case of no answer in 24 hours write us to this e-mail:[email protected]
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 4Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
hxxps://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Since no decryption software is currently available, we highly recommend you back up all the encrypted files before you remove Revon ransomware; otherwise, the data might get permanently damaged. For malware elimination, you should employ one of the anti-virus engines that can deal with the infection. Note that infiltration can also be prevented with the help of AV tools that detect the main executable file Fast.exeXX.exe as follows:
- Trojan/Win32.RL_Generic.R325921;
- Gen:NN.ZexaF.34106.duW@aSFkxzo;
- Ransom.Phobos;
- Win32:Malware-gen;
- W32/Phobos.8B03!tr.ransom;
- A Variant Of Win32/Filecoder.Phobos.C;
- HEUR:Trojan.Win32.Generic, etc.
In case you do have backups, you should not bother with copying the encrypted files and simply eliminate the malware as soon as possible. In case your machine is still not working correctly after you get rid of Revon ransomware, you should fix the damage done with the help of such tools as Reimage Reimage Cleaner Intego.
Prevent ransomware intrusions and ensure you backup your data regularly
Since Phobos ransomware can access all the networked drives, the consequences of the infection can be devastating. Thus, the best way to negate the consequences of a ransomware infection is to have up-to-date backups that are stored on a remote server. This should not be connected to the main network, as the attackers can then easily access backups and encrypt them as well.
Unfortunately, many cybercriminal gangs behind the most popular ransomware families like Maze or DoppelPaymer now started extorting sensitive company information and publishing it online in case the ransom demands are not fulfilled.[3] This way, malware can cause not only loss of important data but also result in sensitive details compromise. There have been no reports of Phobos developers doing this, although it is most likely a matter of time.
Once Revon ransomware encrypts data, it is impossible to to open files, unless a special key is obtained

Once Revon ransomware encrypts data, it is impossible to to open files, unless a special key is obtained
So, how do you protect the important data from ransomware infection? The answer is relatively straight forward – you must put resources into cybersecurity, such as regular staff training and adequate security solutions. Since Revon mainly spreads with the help of weak RDP connections, here are some tips on how to protect it better:
- Never use a default TCP/UDP port 3389;
- Limit RDP access to those that need it only;
- Enable Network Level Authentication (NLA) via System Properties;
- Employ a VPN;
- Use strong passwords.
Eliminate Revon ransomware correctly
As previously mentioned, if you do not have working backups of your files, you should remove Revon ransomware immediately. First, you should employ an external storage device and place all the locked data there. Once done, you need to initiate a network-wide scan to find and eliminate all the malicious files that were placed by the Revon virus.
In case Revon ransomware removal is hindered due to its functionality, you can access Safe Mode with networking and performing a scan from there. Once you are sure that all the malware is gone, you can start with data recovery – simply connect your backups and copy it over. If no backups are available, you can try other methods listed below. Note that paying cybercriminals is also an option, but is not recommended due to a risk of cybercriminals not providing the decryption tool after payment. In such a case, you would not only lose your files but also money, so take that into consideration.
This entry was posted on 2020-04-09 at 05:28 and is filed under Ransomware, Viruses.

