Rezm ransomware – a malicious version of the Djvu ransomware family that can result in the installation of AZORult Trojan virus
Rezm virus – ransomware that provides the _readme.txt ransom message which holds ransom demands from $490 to $980

Rezm virus – ransomware that provides the _readme.txt ransom message which holds ransom demands from $490 to $980
Rezm ransomware is considered to be a file-locking malware form that employs the AES-256 cipher to release unique code on targeted files. These types of parasites are programmed to plant themselves on Windows computer systems that are running on various versions such as Windows 7, Windows 8, Windows 10, etc. Once the cyber threat infiltrates the targeted machine, it loads the encryption on every piece of data that is discovered. When Rezm ransomware encrypts all of the files, they get the .rezm appendix added to their names. From then on, the victims cannot properly access their documents and folders anymore unless they get the decryption tool that would be able to unlock the blocked components.
Rezm ransomware is currently an undecryptable form of malware as it has been released after August 2019 when the Emsisoft decryption tool works for STOP/Djvu ransomware variants that have emerged before this date.[1] Regarding this fact, criminals load the _readme.txt ransom note on the computer screen of the infected device and urge for a quite big price in exchange for the useful decryption key. Rezm ransomware developers ask for $490 as a starter amount if the demands are met within 3 days. However, if the victim is late to pay, he has to transfer a doubled price that is $980.
Criminals who spread Rezm ransomware will likely insist on payment in Bitcoin or another type of cryptocurrency when you contact them via [email protected], [email protected] email addresses or @datarestore Telegram account. However, the demanded amount is quite a big price to pay for a regular user and can even be one’s full monthly salary. If this is also the case for you, you should think of other data recovery options. Nevertheless, Rezm ransomware developers are very likely to scam their victims, so paying the demanded ransom price is never recommendable.
| Name | Rezm ransomware |
|---|---|
| Type | Ransomware virus/malware |
| Family | Djvu/STOP ransomware |
| Founder | Michael Gillespie |
| Encryption | This cyber threat looks for encryptable data once it arrives at the computer system. When the malware finds all of the files, folders, and documents, it launches the AES-256 encryption cipher and uses it for coding up the files. Afterward, the filenames receive the .rezm appendix as a sign of the encryption process performed |
| Ransom note | When all of the files and folders are locked with a unique cipher, the malware loads the _readme.txt ransom note on the computer screen where it asks for a particular ransom sum in exchange for the decryption software |
| Demanded sum | Criminals urge for a payment of $490 that needs to be transferred in Bitcoin cryptocurrency within three days. If the victim is late with the ransom, the sum doubles to $980 |
| Crooks’ contacts | Rezm ransomware virus provides the [email protected], [email protected] email addresses, and @datarestore Telegram account as a way to contact the criminals if the user wants to receive the decryption software |
| Distribution | Most of the time, Djvu ransomware variants are spread by using software cracks such as key generators that can be downloaded from pirating websites. Sometimes, this type of malware can also be passed through email messages that include malicious attachments, malvertising, etc. |
| Danger level | Rezm virus holds the danger level of high as it is capable of infiltrating various types of Windows computer systems and locking up all of the files that are found there. Nevertheless, the user can get infected with the AZORult Trojan horse that is commonly distributed by STOP ransomware variants |
| Elimination | If you have been infected with this ransomware, you need to get rid of it as soon as possible, otherwise, your files will remain encrypted and your computer system will still be vulnerable to various infections. For this task, employ only reliable antimalware software that is capable of detecting such parasites and dealing with them |
| Fix software | If the ransomware virus has corrupted some areas on your computer or has allowed other malware to do that, you can try repairing the affected places with the help of software such as Reimage Reimage Cleaner |
.rezm files virus is ransomware that has emerged at the very start of March and has been first reported on the Twitter social platform by a cybersecurity researcher named Michael Gillespie.[2] It is known that this virus is the 211th version from the Djvu ransomware family. As you can see, this malware category has been releasing identical variants very rapidly.
According to the Emsisoft blog,[3] Djvu/STOP ransomware was the most commonly reported ransomware string between April 1 and September 30, 2019, that rank 56%. This type of malware has been produced since the end of 2018 and has been actively distributed by cracked software such as key generators that can be found on torrenting networks.
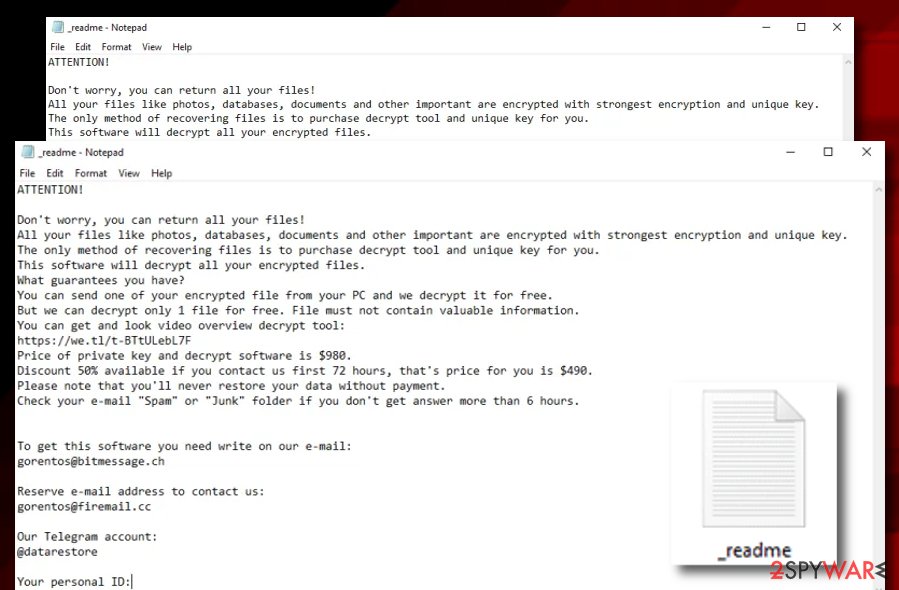
Rezm ransomware targets English-speaking users as its ransom note is written in the English language and is identical to every ransom message that is released by Djvu ransomware variants. Criminals in the message claim that files have been locked with the strongest encryption cipher and the only way to return them is by purchasing the key from them:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-7YSRbcuaMa
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]Your personal ID:
Rezm ransomware wants to make sure that the victims fall for believing that “you’ll never restore your data without payment”. Even if there truly are low chances that you will recover your files without the original decryption tool, you should still stay away from transferring the demanded ransom price due to the below-mentioned risks:
- You make the payment but the criminals just run off with your money.
- Hackers provide you with a fake data recovery tool.
- Crooks raise the ransom demands after you make the first payment.
Rezm ransomware developers will, of course, demand some type of cryptocurrency, e.g. Bitcoin, when you contact them via the provided email address or Telegram account. Digital currencies allow both parties to stay completely anonymous which is very beneficial for the criminals as they can remain untrackable by not revealing their identities.
Rezm ransomware is dangerous malware that comes from the Djvu/STOP ransomware family and is the 211th variant released

Rezm ransomware is dangerous malware that comes from the Djvu/STOP ransomware family and is the 211th variant released
Even though Rezm ransomware uses a unique Advanced Encryption Standard[4] cipher to lock up all files and stores both encryption and decryption keys on remote servers, you still might have a chance to recover at least a piece of your data by employing third-party software. We have added some tools to the end of this article.
However, it is important to choose a piece of software that has the best chances of helping you to recover .rezm files as Rezm ransomware might be able to delete Shadow Volume Copies of encrypted data by running specific PowerShell commands. This way you might not be able to restore your data with certain types of software.
Furthermore, Rezm ransomware is capable of modifying Windows hosts files to prevent you from accessing security-related websites and forums and receiving valuable information on the removal process of the malware. Note that you have to delete these files when you are completing the virus elimination, otherwise, access will remain blocked.
Also, Rezm ransomware will try to remain persistent by adding various entries into the Windows Registry that help the malware to boot up every time the Windows computer is turned on. Nevertheless, some ransomware viruses have the ability to disable certain types of antimalware software in order to avoid getting detected.
Additionally, Rezm ransomware might camouflage as a legitimate process and start operating in the Windows Task Manager. Such malware can disguise as some type of well-known software, service, or application. While ones are known to camouflage as a web browser task, other viruses can pretend to be a flash player or another type of process.

Another dangerous capability of Rezm ransomware is to install malicious pieces of software on the vulnerable computer system. STOP ransomware viruses are known to distribute AZORult Trojan horse. If this type of malware lands on a particular device, it can start recording personal information, swindling money, damaging software, etc.
If you want to avoid all of these possible consequences, you need to remove Rezm ransomware from your Windows computer ASAP. The best way to get rid of these types of cyber threats is by installing reliable antimalware software. If the malware has applied any damage to your PC, try repairing the corrupted areas with the help of Reimage Reimage Cleaner .
However, if you are having trouble with Rezm ransomware removal or to detect this particular malware, this might be because the parasite is blocking your antivirus program. To diminish such type of activity, you should boot your computer in Safe Mode with Networking or activate the System Restore feature as described at the end of this article.
When Rezm ransomware is gone, you should try the alternative data recovery methods that have been provided by our security experts. If you find none of them helpful, there also is an option to purchase the RescuePack from DrWeb[5] that includes decryption software and two years of full computer protection for only $150.
Djvu ransomware variants are mostly distributed through software cracks
Ransomware infections are very commonly spread through cracked products such as key generators that are downloaded from torrenting websites such as The Pirate Bay. You should prevent yourself from visiting these types of pages and use only original sources for receiving software to decrease the risk of catching a ransomware virus.
Furthermore, ransomware developers can think of different types of methods to distribute infections. Below we provide a list of other commonly used places for the delivery of file-encrypting malware:
- Email spam and their malicious attachments. Crooks often attach malicious executables, word documents or other files to suspicious email messages that pretend to come from reliable companies. Do not open any unknown attachments without scanning them with antimalware products.
- Malvertising. Malicious advertisements are also a popular source of delivering malicious strings. Avoid clicking on every advert that you encounter while browsing the web. Even better, install an adblocker to prevent intrusive advertising in the upcoming future.
- Fake software updates. Crooks also disguise ransomware as false JavaScript or Adobe Flash Player updates. This is a very easy way to trick users so you should always be aware when provided with offers to upgrade your products. Download the updates from their official sources only.
Additionally, we want to outline the importance of reliable antivirus software. You should not be afraid to invest in trustworthy automatical security that will serve you in the future. These types of tools can prevent you from visiting deceptive websites, downloading malicious pieces of software, proceeding with infected links, advertisements, and so on.
Terminating Rezm ransomware and recovering files
If you have been infected with this cyber threat, you have to get rid of it as soon as possible. According to cybersecurity experts from LosVirus.es,[6] the more time you spend on waiting, the worse the infection can get and you might not even notice how other malware forms start operating on your computer system so it is the best to speed up Rezm ransomware removal.
You should employ only reliable software that is capable of detecting .rezm files virus. If your tools are having trouble with that, this might be because the malware is blocking your antivirus software. Try diminishing such malicious changes with the help of Safe Mode with Networking that is listed as a computer boot option at the end of this article.
When you successfully remove Rezm ransomware from your Windows machine, you should scan your device for possible damage with tools such as SpyHunter 5Combo Cleaner and Malwarebytes. If these programs show any signs of corruption on your system, you can try repairing the altered areas with the help of Reimage Reimage Cleaner .
After that, you can continue with the file recovery of those components that were touched by Rezm ransomware. At the end of this article, we have provided some data restoring software that might help you to recover at least some of your files. Also, you can try purchasing the RescuePack from DrWeb that includes decryption software.
Remove Rezm using Safe Mode with Networking
To diminish malicious changes and activities on your Windows computer that have been initiated by the ransomware virus, you should boot the device to Safe Mode with Networking as shown in the following instructions.
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
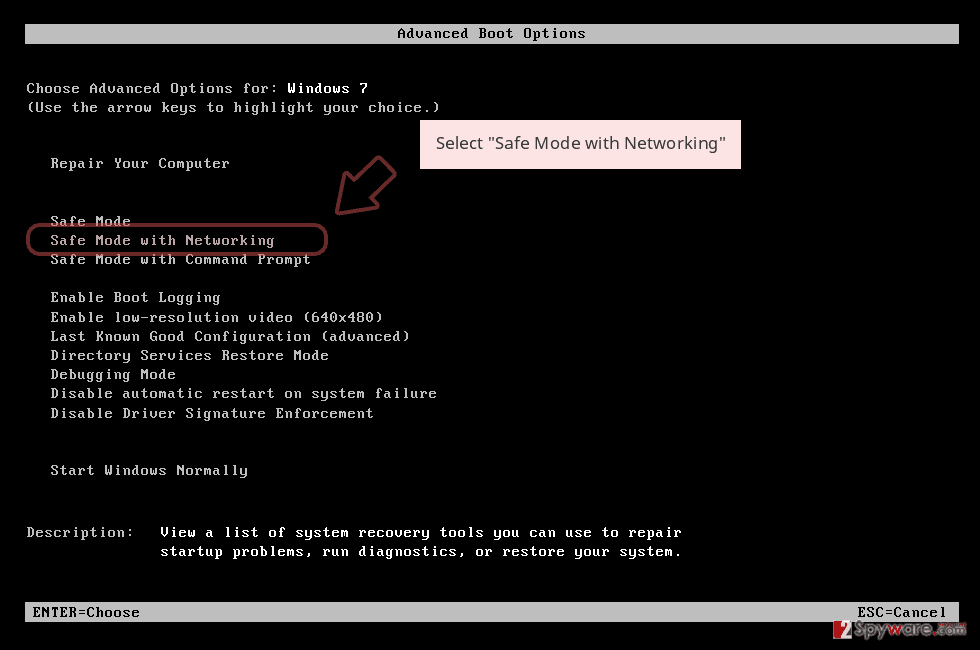
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
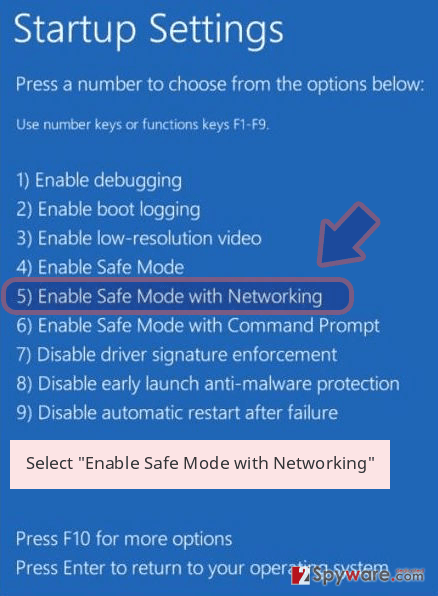
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Rezm removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove Rezm using System Restore
To deactivate the ransomware virus and disable all the questionable changes that it has performed, you should opt for System Restore. If you do not know how to select this feature, we have provided some instructions below.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Rezm from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
.rezm files can be hard to recover without a proper decryption tool. However, it is not worth paying the demanded ransom price and risking to get scammed when there are other options that you can try.
If your files are encrypted by Rezm, you can use several methods to restore them:
Employ Data Recovery Pro and try to restore some files.
If the ransomware virus has locked your files, documents, and folders, you might have a chance of restoring at least some of the components. Also, this software can work for deleted and damaged files too.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Rezm ransomware;
- Restore them.
Use Windows Previous Versions feature for data restore.
If you have been looking for software that might help you to recover some of your data, this tool might do the trick. However, you need to make sure that you have enabled the System Restore feature before the ransomware attack.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try Shadow Explorer for file recovery.
You should give this software a try if you have been looking for a tool that might help you with data recovery. However, be aware that this current method might not work if the ransomware virus has eliminated the Shadow Volume Copies of your encrypted files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, cybersecurity researchers are still working on the official decryption tool for .rezm files.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Rezm and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-03-02 at 04:31 and is filed under Ransomware, Viruses.

