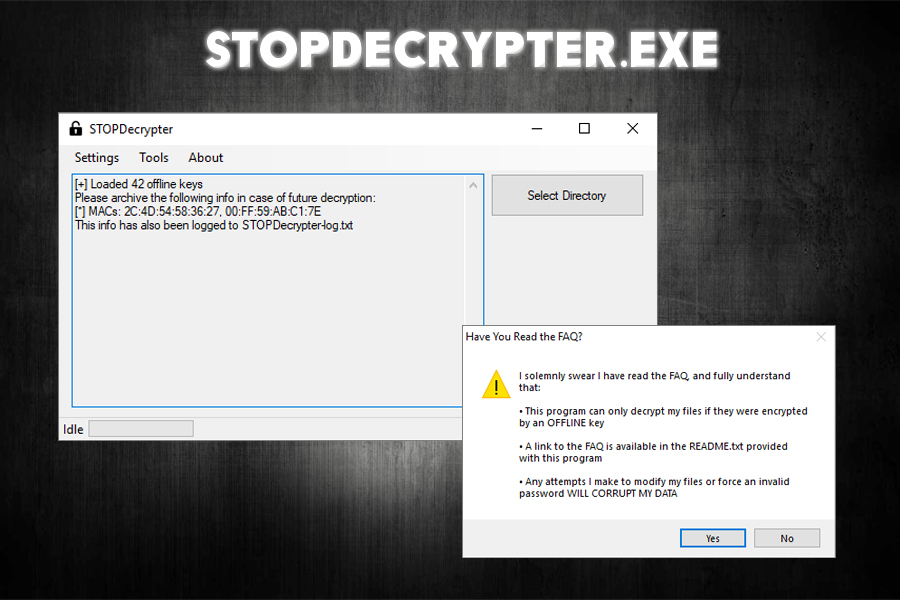
STOPDecrypter.exe – a decryption tool created to recover files locked by STOP ransomware
STOPDecrypter.exe is a legitimate executable presented by Michael Gillespie – a renowned security expert and ransomware hunter. Being actively involved in STOP ransomware analysis, the researcher designed a tool helping the victims of crypto-malware to retrieve encrypted files. Beware: it does not work for all variants! Recently, hackers have started using different encryption methods making the decrypter completely useless. This version of the tool is no longer capable of decrypting files affected by the Djvu or Stop virus variants because criminals started to use proper encryption and online keys instead of offline keys that were easily decryptable before. At the moment of writing, the latest version of STOPDecrypter.exe is STOPDecrypter v2.1.0.9. You can download it from here.
As a result of the encryption and coding changes made by the criminals, STOPDecrypter is no longer supported and has been discontinued. Fortunately, it has been replaced with the Emsisoft Decryptor for STOP Djvu Ransomware developed by Emsisoft and the same malware expert who developed STOPDecrypter – Michael Gillespie. This particular tool works for threat variants released until August 25th, 2019. It is possible that the tool is getting updates after any changes in encryption, so we will keep you updated.
| Name | STOPDecrypter.exe |
| Type | Executable |
| Belongs to | STOPDecrypter free decryption tool |
| An optional tool for Djvu decryption | STOP decrypter is no longer working, so you should try the Emsisoft tool for most Djvu ransomware versions that you can get it from here |
| Purpose | To help the victims of STOP ransomware to retrieve locked files for free |
| Developer | Michael Gillespie |
| Download link for STOP Decrypter | Direct link |
| Virus Total detection | 13/70[1] – while the detection is most likely a false positive, use the tool at your own risk |
STOP Decrypter was introduced because of STOP ransomware which is one of the most prolific ransomware families around. Its sub-family DJVU has also been active recently. Since its release in December 2018, the hackers behind these two viruses have released dozens of versions, each of which appends different file extensions.
STOPDecrypter.exe can be used to negate the harmful effects of ransomware and retrieve all pictures, music, video, documents, and other files for free. Nevertheless, while some older variants can be deciphered with the tool, it is not that simple when it comes to the newest versions as the encryption process can be performed only with offline malware versions.
STOPDecrypter.exe had been updated constantly till hackers changed the way they encrypt victim’s data. Starting with Coharos ransomware, Gero ransomware and Hese ransomware, the tool won’t work. However, infections such as Heroset, Stone, Lanset, and others (OFFLINE) will be decrypted.
Djvu ransomware has more than 180 variants released already. Unfortunately, the tool that STOPDecrypter.exe belongs to is no longer working for them. Also, other decryption tools are only capable to recover first 148 due to changes in the encryption process. The list of possibly decryptable versions:
.bora, .reco, .kuub, noos, .nesa, .karl, .kvag, .moka, .shadow, .djvu, .djvur, .djvuu, .udjvu, .uudjvu, .djvuq, .djvus, .djvur, .djvut, .pdff, .tro, .tfude, .tfudet, .tfudeq, .godes, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promorad, .promock, .promok, .promorad2, .kroput, .kroput1, .pulsar1, .kropun1, .charck, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .vorasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .berost, .forasom, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .rezuc, .stone, .skymap, .mogera, .redmat, .lanset, .davda, .poret, .pidom, .pidon, .heroset, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .darus, .tocue, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .cetori, .stare, .carote, .gero, .hese, .seto, .peka, .puma, .pumax, .pumas, .DATAWAIT, .INFOWAIT.
Ransomware is possibly one of the worst and most destructive malware families in existence, as the locked data does not get restored, even after infection removal. That is when victims realize that they must pay cybercriminals a hefty sum (STOP ransomware usually demands $980 or $490 ransom payment in Bitcoins) or lose their files forever.
While it might be hard to choose what to do, paying hackers is not recommended as they might misuse your trust and never send the decryption key back after receiving the payment. In such a case, users are risking losing not only personal files but also the money.
Fortunately, security experts are constantly working on ways how to crack the code of ransomware. STOPDecrypter.exe is one of them. On the other hand, some ransomware victims might never be able to retrieve their data, as decryption tools are not available for all ransomware. Most of the existing tools can be found on No more Ransom project page online.
STOPDecrypter.exe usage instructions
Before you do anything, you need to ensure that you remove the ransomware virus from your computer, as the infection of the malicious software and encryption of files are two separate things. To do that, you should employ reputable security software, although be aware that not all variants of STOP ransomware are recognized by various AV vendors, so a scan with multiple different tools might be needed.
STOPDecrypter.exe is a relatively simple tool to use. However, before putting it to work, it is highly recommended to read a README.txt document, where many questions are answered, and the instructions are given. Once done, you can click on the STOPDecrypter shortcut, click “Yes” and then open the application to view a simple UI.
The next steps highly depend on which STOP ransomware version you are infected with. For some versions, you will simply need to upload ransom note, personal ID and MAC address and proceed with the decryption process, which other cases require direct contact security experts that created STOPDecrypter.exe – you can reach out Michael Gillespie on Twitter.[2]
Steps to take if STOPDecrypter.exe does not work
STOPDecrypter.exe should work perfectly fine with versions that use uppercase file extensions, such as .KEYPASS, .PAUSA, .DATASTOP, .INFOWAIT, and others. Additionally, the Puma family of the virus uses XOR[3] encryption, which is quite easy to decode, so all variants of this branch should be decryptable without problems.
Nevertheless, STOPDecrypter.exe might not work for victims if the encryption process was performed when the infected machine contacted the remote server. Fortunately, for other victims, the outcome can be positive as long as the virus did not reach the remote server and performed the encryption offline.
If you belong to the former group of people, and STOPDecrypter.exe did not work for you, you should try data recovery software. You can find all the alternative solutions in articles such as Meds ransomware removal instructions.
