Html/rce.gen3 – a trojan that gets detected by antimalware every time when the user opens Internet Explorer Html/rce.gen3 is reported to be a Trojan virus[1] that is detected by antivirus software when users open web browsers such as Google Chrome, Mozilla Firefox, Microsoft Edge, and Internet Explorer. A user has […]
Trojans
Trojan:Win32/Occamy.C is the malware that can open backdoors on the infected system for other hackers or load malware Trojan:Win32/Occamy.C is the malware that can be set to steal passwords or even spy on the victim but that depends on the particular version you encountered. This trojan is designed to stealthily infiltrate […]
Occamy.C
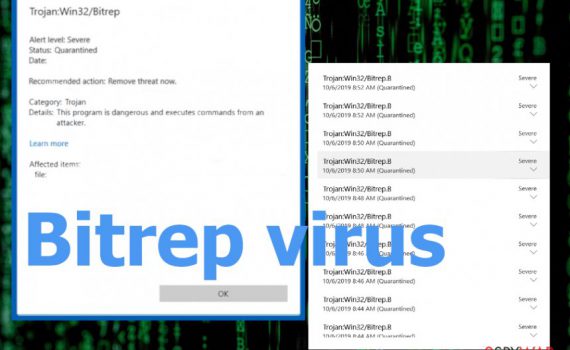
Bitrep virus is the trojan horse infection that can be set to perform tons of different malicious processes on your device Bitrep virus is the term used for a big amount of detection names that share the same name. This is the virus that stealthily infiltrates the machine and runs […]
Bitrep virus
Kronos malware is the trojan designed to steal sensitive information from victims and transfer funds from the bank accounts Kronos malware – banking trojan that had a few updates since 2014 when it first got released. This malware is the type of virus that pretends to be a simple email attachment, […]
Kronos malware

Trojan.Agent is a generic definition of particular malware that can be set to do a variety of malicious tasks on the infected machine Trojan.Agent is a type of malicious software that uses deception to access user’s Windows machines Trojan.Agent is a heuristic[1] detection name of a Trojan malware category and […]
Trojan.Agent
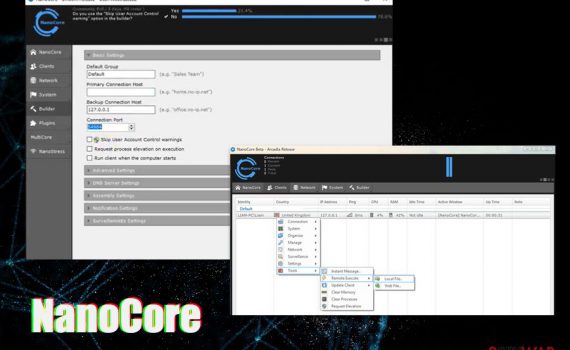
NanoCore virus is a sophisticated trojan that threat actors utilize to remotely control the infected machine NanoCore virus is a remote access trojan (RAT) that allows the attackers to take over the host machine NanoCore virus is a backdoor and a remote access trojan that is used in a variety […]
NanoCore virus
Kwampirs malware is a backdoor Trojan that targets healthcare organizations and infects computers connected to medical equipment Kwampirs malware is a backdoor that allows the threat actors to take over the machine and spread the malicious payload across network sahres Kwampirs is malware with worm-like capabilities mainly used by a […]
Kwampirs malware
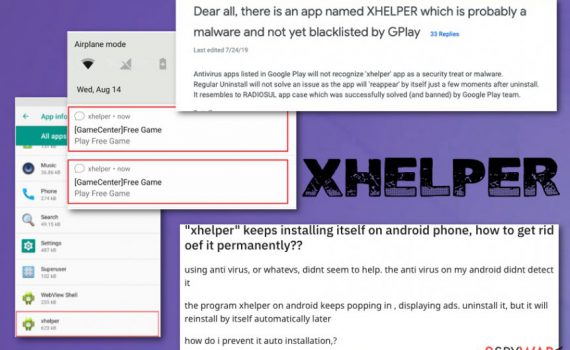
xhelper – Android malware that reinstalls itself after termination, uninstallation and even factory reset xHelper is the trojan dropper that delivers malware like banking trojans and ransomware on mobile devices. This trojan has already infected 45 000 devices in the past six months, mainly targetting U.S, Russia, and India. Malicious applications […]
xhelper

Regin malware is a Trojan developed by National Security Agency to gather intelligence information on targeted Windows machines Regin is a sophisticated APT that is capable of taking control over the host machine on all levels Regin virus is a multi-stage malware program designed to open a backdoor[1] on the […]
Regin virus

Skeleton Key is dangerous malware that targets 64-bit Windows machines that are protected with a single-factor authentication method Skeleton Key is a stealthy virus that spawns its own processes post-infection Skeleton Key is a Trojan that mainly attacks corporate networks by bypassing the Active Directory authentication systems, as it abuses […]
