Toec ransomware is the cryptovirus that locks user’s files forever due to an advanced encryption algorithm applied
 Toec ransomware is the malware that employs a sophisticated encryption algorithm and makes files useless to have a reason for a ransom demand. This is the 179th version of the notorious Djvu ransomware that keeps releasing variant after variant. Unfortunately, the previously-known as decryptable, now the family includes more advanced coding techniques, and it may take years to develop the decryption tool which recovers those affected files. There are some free tools released already, but virus developers keep stating that those programs can only help with files encrypted using offline keys or for versions discovered before August 2019. One of the more recent and powerful tools that works for 148 versions can be found here.
Toec ransomware is the malware that employs a sophisticated encryption algorithm and makes files useless to have a reason for a ransom demand. This is the 179th version of the notorious Djvu ransomware that keeps releasing variant after variant. Unfortunately, the previously-known as decryptable, now the family includes more advanced coding techniques, and it may take years to develop the decryption tool which recovers those affected files. There are some free tools released already, but virus developers keep stating that those programs can only help with files encrypted using offline keys or for versions discovered before August 2019. One of the more recent and powerful tools that works for 148 versions can be found here.
It is possible that files affected by Toec ransomware virus and marked with the .toec appendix cannot be recovered, but you can still try to use third-party software capable of restoring encrypted files. If these files are backed up on external devices, cloud services, you should be fine. Of course, you need to clean the machine thoroughly before you add anything new to the device to prevent further damage. For that, anti-malware programs work the best but follow the article to learn more tips.
| Name | Toec ransomware |
|---|---|
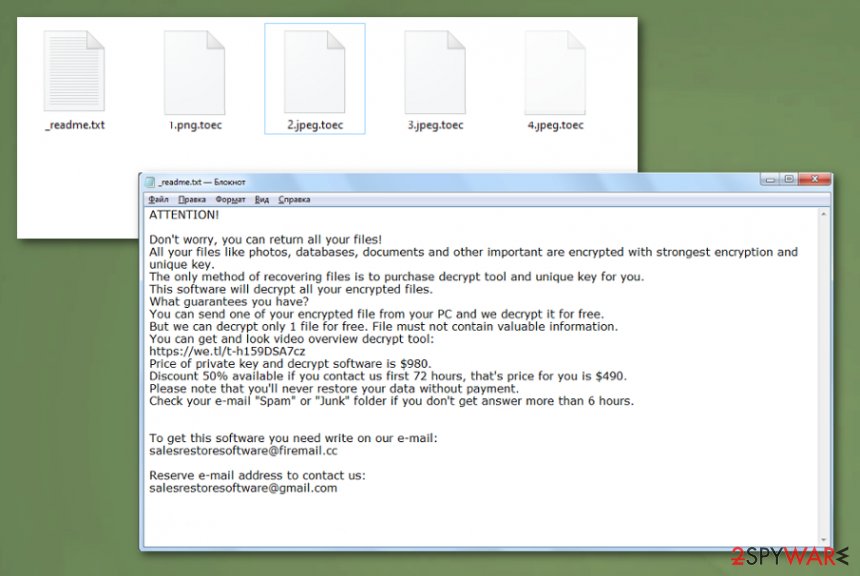
| File marker | .toec marker comes after the original file name and extension that determines the type of data. This appendix indicates affected files besides the blank file logo |
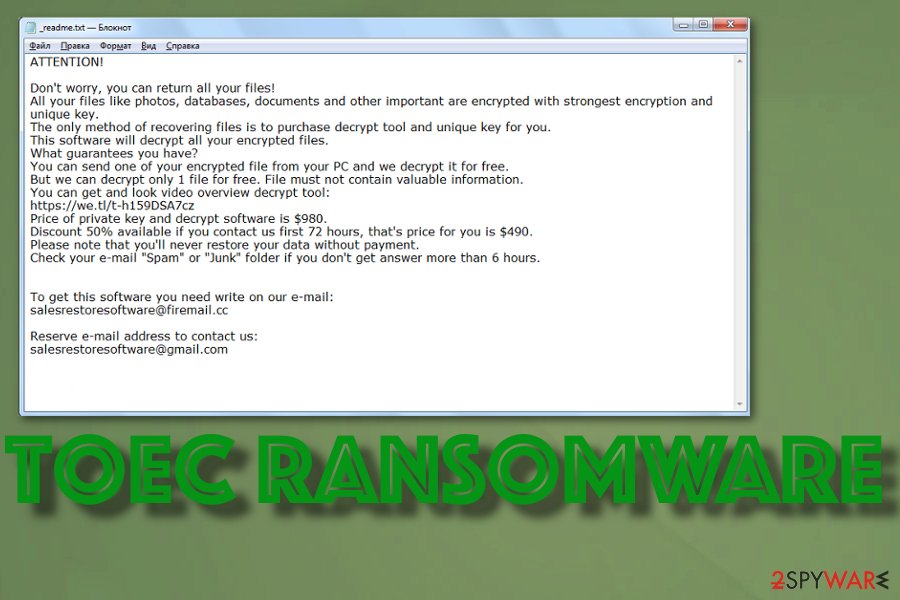
| Ransom note | _readme.txt – a text file that gets placed in various folders and contains information about the encryption, payment details, ransom amount and time window |
| Family | Djvu/STOP virus |
| Contact emails | [email protected], [email protected] |
| Distribution | These viruses involving extortion and damage to files, system functions, spread around via infected files that drop the malicious script directly on the system. In most cases, the victim downloads cracked or pirated software, and executable or different type of data get installed. Also, malicious macro infections[1] come from spam email campaigns delivering infected documents with content enabling suggestions. The encryption starts immediately after one of these scrips get launched |
| Elimination | The best tool for Toec ransomware removal is an anti-malware program because it can locate all core files and associated programs which need to get terminated completely |
| System repair tips | Use reputable anti-spyware to fix the system. Since the threat interferes with various system files, you might need to fix virus damage by using Reimage. Note that it cannot decrypt encrypted files! |
Although Toec ransomware deletes the main virus file after successful encryption, there are many files planted around the system. Also, programs get installed to affect some system functions, disable applications. Windows registry, other directories, and Shadow Volume Copies may get deleted or compromised, so it becomes more difficult to remove the threat and recover the data. It affects:
- files in windows registry;
- security functions;
- programs or system features having an anti-malware function;
- programs or features having file recovery functions.
Toec ransomware attack begins with the drop of a malicious payload that gets launched and immediately delivers ransomware on the system. To mask the encryption process and other background activities virus shows fake Windows update pop-up and tries to trick the person that the system is running slowly because if this.
Then files get encrypted without your noticing, and the ransom note in _readme.txt file appears in various folders, on the desktop. Once the message appears, you can be sure that Toec files virus is running on full speed in the background. Although the ransom amount of $980 and the 50% discount seems reasonable, paying is not getting you anywhere.
Toec ransomware is the notorious file-locking virus that claims to offer decryption key for a hefty payment of $980 in Bitcoin. Toec ransomware belongs to a known family of DJVU virus that hasn’t changed much, so there is no reason to trust criminals. This malware alters Windows hosts file to disable users from entering security sites and cybersecurity forums. This is how malware tries to prevent victims from accessing anti-malware tools and forums that offer help.
This damage alongside other Toec ransomware-related files needs to be removed completely. Deleting those can be difficult or even damaging when you lack knowledge, so we offer to get an anti-spyware, such as SpyHunter 5Combo Cleaner for this task. Additionally, fix Windows system and corrupted files with the software like Reimage that might fix the damage caused by the virus.
The initial Toec ransomware removal might require disabling the virus, as many experts note.[2] By disabling the malicious processes running in the background, you will get a chance to launch the security software. Tips for this task are provided at the end of this article.
Additionally, get a professional anti-malware program to remove Toec ransomware fully. Detection names[3] and results, in general, depends on the particular virus database that specific tool you use relies on. This is why you shouldn’t expect the particular name of the virus to pop-up on the list of issues and malicious detections and remove all the intruders and threats found on the system.
It is less than believable that Toec ransomware affected files will get decrypted in the future, but you can store virus-related data on the external device before you delete the threat and then check the following sites for decryption tool updates:
Toec ransomware is the threat that affects more parts of the system, but encryption is the most noticeable since it makes your common files useless.
Avoid hacked, pirated files and installations of suspicious programs
The bulk of user complaints about such infections, especially the particular ransomware family includes the key phrases like “I downloaded cracked version” or ” pirated some software.” These tendencies are the biggest mistakes any internet user can make because there are plenty of malware types that get delivered via those torrent services or licensed programs downloaded from a free page.
Infected file loads alongside the program during the installation and gets launched immediately after, so you don’t get the cracked video game or an application. Ransomware lands on the pc instead and immediately start the file locking process. Also, such infected files may appear as financial information attachments on the legitimate-looking email send from crooks.
You need to either clean the email box more often and pay more attention to such details, restrain from torrent services and pirated program networks or keep the system safe with a proper security program that can block any dangerous material.
Make the system Toec ransomware virus-free again with robust anti-malware scan
Any user that surfs the internet should take into consideration the possibility of additional infections and other threats besides Toec ransomware virus. It is known that the family of these file-locking threats also delivers trojans, info-stealing malware. When you recover the files and don’t remove all files of the virus, your identity and privacy remain at risk.
Get the anti-malware tool and run a full system scan. When proper results come back with all the threats and dangerous applications, you can fully remove Toec ransomware from your system. You may need to reboot into a Safe Mode first to achieve the best results, but we have prepared a guide for that below.
In addition to Toec ransomware removal, we recommend employing SpyHunter 5Combo Cleaner, Malwarebytes. Then, for system file repair and optimization purposes, use Reimage. You may need to fix some serious virus damage and corrupted files left on the machine before you use the device normally again.
Remove Toec using Safe Mode with Networking
Remove Toec ransomware by rebooting the machine in Safe Mode with Networking
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
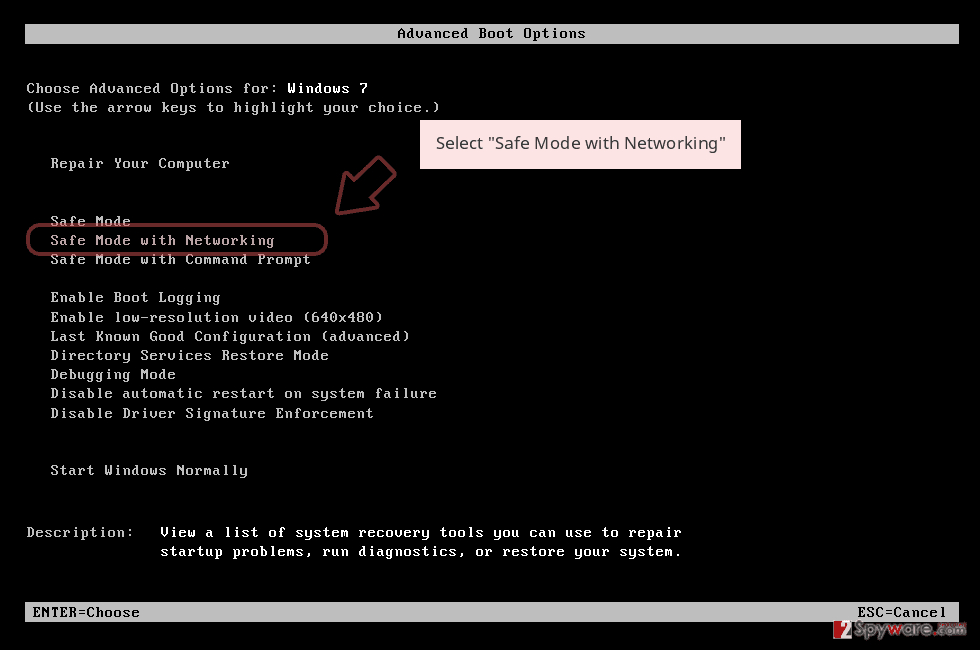
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
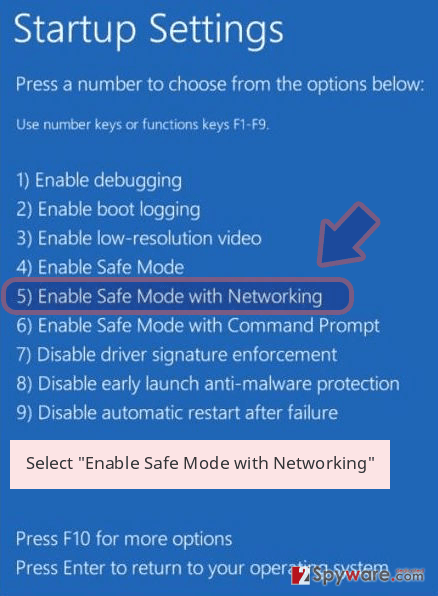
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Toec removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove Toec using System Restore
System Restore should also be a helpful feature for the elimination of Toec ransomware since it can recover the machine in a previous state before the malicious infection
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Toec from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by Toec, you can use several methods to restore them:
Use Data Recovery Pro when your file backups are not up-to-date
You should recover Toec ransomware affect files with reputable thrid-party software like Data Recovery Pro or your own files backed up on separate device
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Toec ransomware;
- Restore them.
Windows Previous Versions is the particular function of the machine that can recover your data
When System Restore gets enabled, you can rely on Windows Previous Versions and restore encrypted files one by one
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer as an alternate data recovery method for Toec ransomware encrypted files
When Toec ransomware virus is not affecting those Shadow Volume Copies, you can use them to restore files with ShadowExplorer
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption of the particular Toec ransomware virus affected files is not possible
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Toec and other ransomwares, use a reputable anti-spyware, such as Reimage, SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2019-11-05 at 04:12 and is filed under Ransomware, Viruses.

