Twok.pro – an unreliable domain that produces awkward pop-up notifications to its subscribers
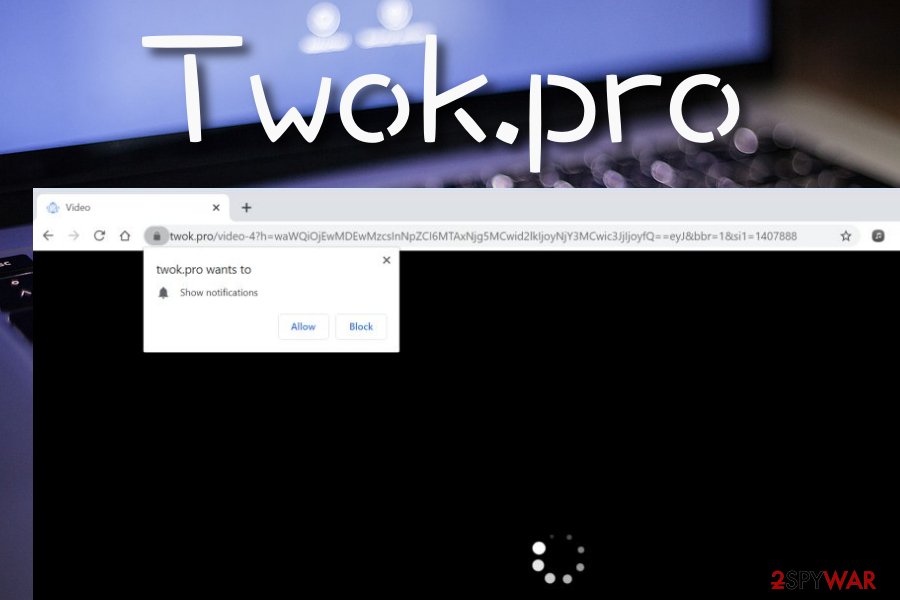
Twok.pro is categorized as adware that urges to click the “Allow” button in order to convince that you are a human or watch some type of video
Twok.pro is included in the list of adware programs due to the intrusive advertising it promotes. As long as adware collects most of its income from the pay-per-click module,[1] this app is no different. If you give permission for its notifications to appear on your computer screen while you are browsing, be almost sure that there are a lot of irrelevant offers awaiting you. Twok.pro can try to convince you to approve its subscription by encouraging you to click on the “Allow” button in order to prove that you are not a robot and continue with the website again or to watch some type of hidden video.
However, the only button you should click here is the “Block” one, otherwise, things might start getting messy. Twok.pro virus is a name attached to this adware not for any reason. The PUP sneaks into the system by using deceptive tactics, infects web browser apps, and starts producing a heavy load of ads, redirecting the user to other sources, etc.
| Name | Twok.pro |
|---|---|
| Type | Potentially unwanted program |
| Sub-type | Adware |
| Distribution | This suspicious application mostly enters computer systems through a deceptive marketing technique known as software bundling. You can receive this unwanted product while downloading various PDF managers and similar components from third-party websites such as softonic.com, cnet.com, and download.com |
| Signs | The adware program can initiate changes on web browser settings such as the homepage and new tab URL zone. Also, you are likely to be provided with a big variety of intrusive advertisements and start experiencing redirects to questionable sources |
| Income source | The main way of earning income for this adware is the pay-per-click. Every click on the provided ads brings money to the program’s developers. Also, some income might come from the non-personal information that the spreaders share with other parties |
| Elimination | If you are having trouble with this app lately, we suggest removing it with trustworthy antimalware before your web browsers start failing due to the high frequency of the ads provided. As an alternative, you can also complete manual cleaning steps that are placed at the end of this article |
| Fix tip | If you have discovered any type of corruption in your computer, you can try repairing those areas with the help of automatical repair software such as Reimage Reimage Cleaner |
Twok.pro pop-up ads are the main trouble that will likely be troubling you while dealing with this PUP (potentially unwanted program). The notifications can start appearing at any time after the adware settles on your computer. Most of the time you will see various offers of rogue security products, coupons, upcoming sales, fake prize claims, etc.
Be careful with the last ones as they are very tricky and aim to scam people. If Twok.pro provides you with some type of survey in order to win a prize, do not fill any personally-identifiable information as you cannot know where such type of information will get misused in the future. Also, do not provide any contact details such as your mobile phone number or email address as you might start receiving more scams or get spammed with advertising content.
Twok.pro – an ad-supported application that mostly travels bundled with other free programs
Also, try not to get lured in any offers that are promoted by Twok.pro as you can accidentally get attached to high-costing services and agree to pay an inadequate price for a useless thing. Furthermore, do not get attracted to suggestions to purchase system optimization software as these types of products are also a part of a scheme that involves swindling money from the users and bringing no true value to them.
You should also know about another feature that belongs to Twok.pro. This function is called redirecting and aims to take users to affiliate websites where you can find more bogus deals. Nevertheless, you can get forcibly taken to a malware-laden domain and your computer can catch a serious infection there.
Be aware that even though Twok.pro is not considered to be malware itself, that does not mean that it cannot be an intermediary for distributing malicious parasites. Some hackers use potentially unwanted programs to bring other stuff to the system and by meaning “stuff”, it can start anywhere from a browser hijacker and end up with ransomware infection.
Another symptom of Twok.pro is browser modifications in the homepage and new tab URL areas. Keep in mind that these changes cannot be reversed unless the adware program is completely gone from your computer system and web browsers. Also, you might find your browsers filled with unknown extensions, plug-ins, and add-ons that belong to the adware.[2] HTTP cookies can also appear as an additional component.
By using these tracking objects, Twok.pro can aim to record details about your browsing habits and online sessions. This type of information usually refers to commonly visited websites, hyperlinks accessed, advertisements clicked, saved bookmarks, your IP, and is used for benefiting from targeted advertising campaigns when the developers create related ads or for sharing the collected data with other parties for monetary income.
Twok.pro removal is the first step that awaits you while dealing with this adware. The process requires cleaning both your operating system and web browsers such as Google Chrome, Mozilla Firefox, Internet Explorer, Microsoft Edge, and Safari. You can use reliable antimalware software to get rid of the program or manual instructions that are added to the end of this page. When you remove Twok.pro, you can continue with fixing any system corruption by trying Reimage Reimage Cleaner .
Bundling is the main technique used for adware delivery
Getting infected with adware is not that unusual as it might seem for a person who caught this type of infection and has no clue where did it come from. According to IT technology specialists from ZonderVirus.nl,[3] potentially unwanted programs are very easy to let in computer systems while skipping downloading/installing steps.
We recommend always paying attention to the downloading instructions and opt-outing of all suspicious components. Besides, make sure that you have set the custom or advanced mode as the default one instead of risking to receive adware and other PUPs by using the recommended or quick settings.
Continuously, third-party sources[4] such as cnet.com, download.com, and softonic.com are also found filled with bogus products that can bring potentially unwanted programs to the system. Our point is that you should download and install all of your wanted software from official and reputable developers/pages only.
Some other adware hiding places include rogue flash player downloads, infectious hyperlinks, and advertisements that you might meet on the Internet. Avoid visiting unknown locations on the web and always make sure that your antivirus protection is working properly as it should report all threats that are spotted ahead.
Automatical and manual removal instructions for Twok.pro
Twok.pro removal requires paying a lot of attention if you consider completing the process on your own. Below are some instructing steps that should help you to clean operating systems such as Windows, macOS and also wipe out web browsers, including Google Chrome, Mozilla Firefox, Internet Explorer, Microsoft Edge, and Safari as these apps can also be filled with adware-related components or have gotten their settings modified unknowingly.
If you do not like the idea of eliminating the adware on your own, do not worry. You can always remove Twok.pro by leaning on automatical software that will complete the entire process for you. This option might be better not only for less-skilled users but also for those who have been running into a lack of time.
You may remove virus damage with a help of Reimage Reimage Cleaner . SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.

