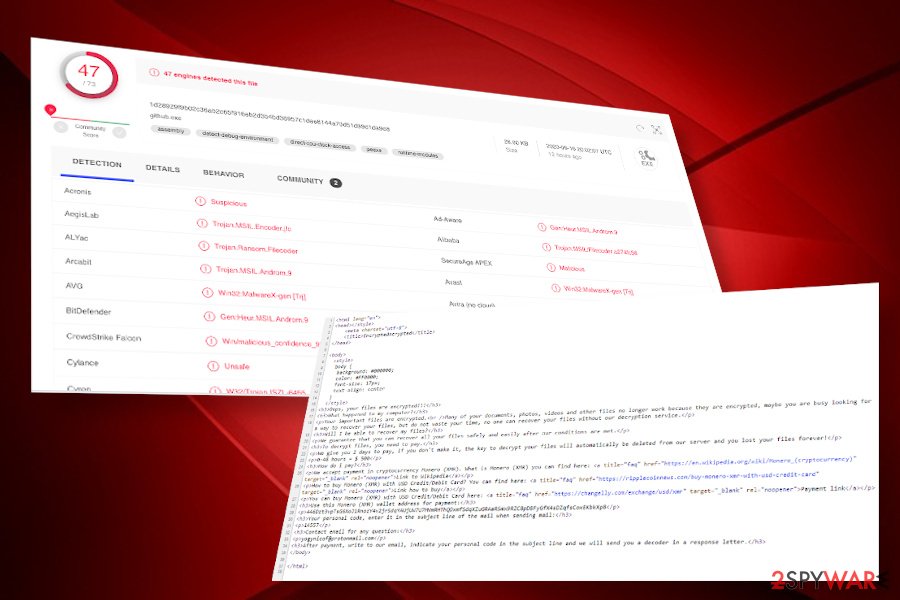
Yogynicof ransomware is a cryptovirus that generates 20 HTML notes on the host machine

Yogynicof ransomware is a virus that encrypts 122 extensions on the machine using AES + RSA encryption algorithm. Upon that, most of the files stored on the targeted Windows machine get locked and replaced with consecutive numbers 1,2,3,4,5,6, etc. To ensure that the user understands that the system is taken hostage, the virus generates 20 HTML files from Read-me! 0.html to Read-me! 20.html on the desktop. Each of the ransom note redirects to the Yogynicof ransom page on the Internet Explorer web browser where victims get the basic information on the attack and ransom payment conditions.
The crooks behind the Yogynicof ransomware offer people to purchase the decryptor for $500. However, this price is applied to those who respond within 48 hours. It’s yet unknown whether the virus permanently restricts people’s access to their personal files if the payment is not transferred with the dedicated period or the ransom size is increased. According to criminals, victims have to make the payment in Monero (XMR)[1] cryptocurrency via the 446Dzt3vpTsG6XoJ1RnozY4v2jrSdqYAUjUW7U7MVmRHThQDxmfSdqXZuGRAaRSmx9RZC8pD8FyGfX4sDZqfsCoxEKbkXp8 Monero Wallet and the write an email to [email protected] indicating unique ID number.
| Name | Yogynicof |
| Type of malware | Ransomware |
| Geneology | The virus is not bound to any known ransomware family |
| Distribution | As typical ransomware, it is being distributed via spam email attachments in particular. However, PC’s can get infected via unprotected RDPs, cracks, keygens, infected software updates, etc. |
| Ransom note | 20 HTML files (Read-me! 0.html to Read-me! 20.html) |
| File extension | It does not use a file extension. Instead, the ransomware renames all files with the consecutive numbers |
| Ransom | Criminals demand to pay $500 within 48 hours in Monero (XMR) cryptocurrency |
| Symptoms | The main symptom – locked personal files, all automatically renamed by numbers, many Read-me! files in HTML format dropped on desktop and other locations. In addition, the machine’s performance can diminish, it may randomly restart or crash |
| Decryption | The ransomware is currently under investigation by cybersecurity experts. Therefore, even though there’s not functional decryptor yet, it’s advisable to copy the Yogynicof encrypted files to external or cloud storage and wait for the decryption tool to be released |
| Removal | Automatic system scan with a professional AV security suite is required |
| Fixing the damage | This virus aims at deleting the content stored on the \Registry\Machine\Software\Microsoft\Windows NT\CurrentVersion\ location. This way, it may damage the system and cause various issues. Thus, upon elimination of the ransomware, it’s advisable to scan the system with Reimage Reimage Cleaner Intego repair tool |
Yogynicof ransomware virus encrypts to files on the infected machine using a combination of AES and RSA encryption algorithm. It is capable of encrypting 122 types of extensions, including MS Office documents, OpenOffice, PDF files, text files, databases, images, photos, archives, and other important files. The extensions mainly targeted by this virus are the following:
.3fr, .7z, .7zip, .acc, .accdb, .ai, .arw, .asp, .aspx, .avi, .backup, .bay, .cdr, .cer, .cpp, .cr2, .crt .crw, .csproj, .css, .csv, .db3, .dbf, .dcr, .der, .dng, .doc, .docm, .docx, .dotx, .dwg, .dxf, .dxg,. eps, .erf, .flv, .gif, .img, .indd, .ink, .jpe, .jpeg, .jpg, .js, .json, .kdc, .litesql, .log, .lua, .mdb, .mdf, .mef, .mov, .mp3, .mp4, .mpeg, .mrw, .msi, .nef, .nrw, .odb, .odc, .odm, .odp, .ods, .odt, .orf .p12, .p7b, .p7c, .pdd, .pdf, .pef, .pem, .pfx, .php, .plist, .png, .ppt, .pptm, .pptx, .ps1, .psd, pst, .ptx, .py, .pyc, .r3d, .raf, .rar, .raw, .rtf, .rw2, .rwl, .sln, .sql, .sqlite, .sqlite3, .sr2, .srf, .srw, .tif, .tiff, .tmp, .txt, .vbs, .vlf, .wav, .wb2, .wmi, .wmv, .wpd, .wps, .x3f, .xlk, .xlm, .xls , .xlsb, .xlsm, .xlsx, .xml, .zip
The Yogynicof virus encrypted files, unlike with most other ransomware viruses, do not get a unique file extension. Instead, they are completely renamed using a simple numbering scheme starting with 1 and increase the sequence depending on the number of detected files.
Besides, it seems that developers of the Yogynicof virus are afraid of victims not to notice the presence of the ransomware. For this purpose, they programmed the virus to generate 20 identical HTML files dubbed as Read-me! 1 .html, Read-me! 2 .html, Read-me! 3 .html, and so on. These so-called ransom notes automatically open the web browser and display a pre-default page that guides the victims through the ransomware maze. The victim is expected to pay Monero cryptocurrency for $500 and transmit the money to criminals via 446Dzt3vpTsG6XoJ1RnozY4v2jrSdqYAUjUW7U7MVmRHThQDxmfSdqXZuGRAaRSmx9RZC8pD8FyGfX4sDZqfsCoxEKbkXp8 Monero wallet. After that, they are supposed to inform criminals about the transfer via email ([email protected]), though the message necessarily has to contain a personal ID number that is given on the HTML file.
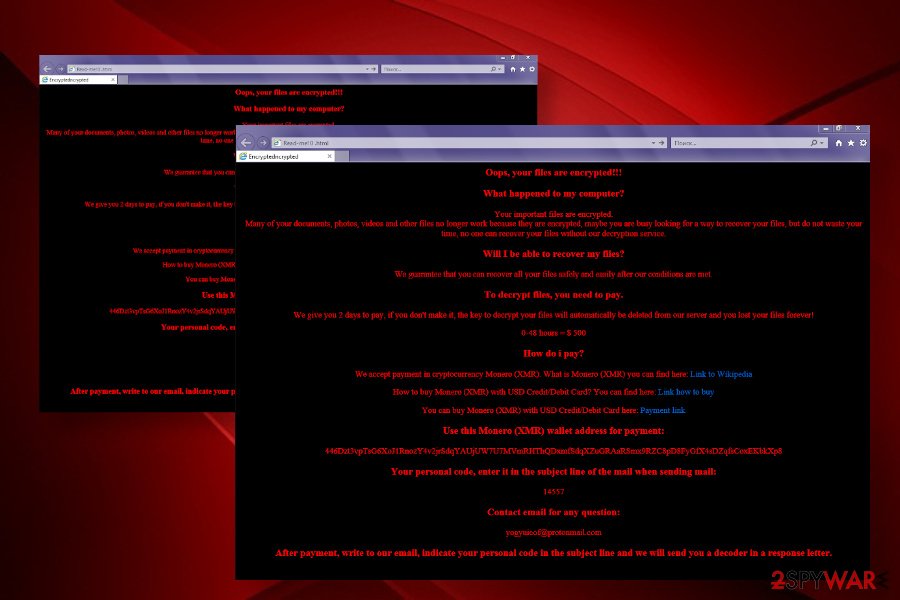
A full text of the Yogynicof ransom note:
Oops, your files are encrypted !!!
What happened to my computer?
Your important files are encrypted.
Many of your documents, photos, videos and other files no longer work because they are encrypted, maybe you are busy looking for a way to recover your files, but do not waste your time, no one can recover your files without our decryption service.
Will I be able to recover my files?
We guarantee that you can recover all your files safely and easily after our conditions are met.
To decrypt files, you need to pay.
We give you 2 days to pay, if you don’t make it, the key to decrypt your files will automatically be deleted from our server and you lost your files forever!
0-48 hours = $ 500
How do i pay?
We accept payment in cryptocurrency Monero (XMR). What is Monero (XMR) you can find here: Link to Wikipedia
How to buy Monero (XMR) with USD Credit / Debit Card? You CAN the find found here: Link how to the buy
You CAN the buy Monero (XMR) with USD at Credit / Debit Card found here: Payment link
the Use the this Monero (XMR) wallet address for payment:
446Dzt3vpTsG6XoJ1RnozY4v2jrSdqYAUjUW7U7MVmRHThQDxmfSdqXZuGRAaRSmx9RZC8pD8FyGfX4sDZqfsCoxEKbkXp8
Your personal below code, Press enter to IT in the are subject line of the mail when sending mail:
14557
Contact email for any question:
[email protected]
After payment, write to our email, indicate your personal code in the subject line and we will send you a decoder in a response letter.
However, files encrypted by Yogynicof ransomware is just a peak of an iceberg. This dangerous virus is programmed to initiate aggressive alterations of the Windows OS. One of the most malicious processes run by this malware is github.exe[2]. Upon infiltration, it automatically opens files on C:\WINDOWS\system32\ and injecting malicious scripts onto them. Based on the analysis, the virus targets these files:
- winime32.dll
- ws2_32.dll
- ws2help.dll
- psapi.dll
- mscoree.dll
- imm32.dll
- lpk.dll
- usp10.dll
- mscoreei.dll
- mscorwks.dll
On top of that, it can delete the content from Windows registries, especially located in \Registry\Machine\Software\Microsoft\Windows NT\CurrentVersion\ directory. Therefore, if your files have been encrypted, we would strongly recommend you to think about an immediate Yogynicof removal instead of ransom payment.

Yogynicof virus generates 20 HTML files on the infected PCs and uses a renaming strategy of the encrypted files

Yogynicof virus generates 20 HTML files on the infected PCs and uses a renaming strategy of the encrypted files
Paying the ransom is pointless because there’s a high risk of being deceived. No one can guarantee that criminals will provide you with a functional decryption tool, thus leaving you with empty pockets and restricted from the usage of personal files.
Luckily, it’s not difficult to remove Yogynicof ransomware from the machine. You should learn how to restart the system into Safe Mode and then launch the antivirus program. However, make sure to use an updated AV version and set it to perform a thorough system scan.
NOTE: before Yogynicof ransomware removal it is advisable to make copies of the encrypted files to prevent permanent file loss. Use external hard drive, USB stick, or cloud storage. This particular ransomware is under investigation right now as it’s a novel virus with exceptional traits. It’s very likely that cybercriminals will detect some flaws in the encryption model allowing them to create a functional free decryption tool.
Ransomware-type viruses can be spread via malicious files within spam emails
File-encrypting ransomware virus is typically disguised by highly obfuscated files. These files can be injected into spam email attachments, fake software updates, cracks, keygens, and whatnot. Often such files are recognized by AV tools; however, it must be fully updated. Nevertheless, there are thousands of malicious executables that manage to bypass security software without being noticed. Therefore, it’s very important for people to be careful when downloading anything on their machines, clicking on ads, links, or any online content.
Nevertheless, the biggest risk to get a ransomware virus is to download pirated software, cracks, and keygens. Millions of people download pirated software for unlocking additional features of paid software without evaluating the risks. At the moment, Reddit[3] and other forums keep reporting about infected Adobe Acrobat crack spread on P2P networks. The latter appears to be infected with a Djvu ransomware virus, namely Zwer, Nlah, Usam, Tabe, and others.
Apart from software cracks, malicious cyber infections are actively distributed via spam email attachments. Therefore, if you receive an “Order Confirmation” email that contains a PDF, Word, Exel, or another format, but you haven’t ordered anything, you’d better not open it as it may be infected with ransomware payload.

Yogynicof ransomware virus can be detected by 47 AV engines out of 73
Get rid of the Yogynicof ransomware virus and recover the damage
Yogynicof ransomware virus focuses on locking up people’s files and then collecting the money from helpless victims. However, the damage it causes is much bigger. The file-encrypting virus unleashes tens of malicious files on the system, which aggressively alters various Windows settings, registry entries, processes, etc., which eventually can make the system crash, generate BSODs, and errors.
Therefore, if you have noticed 1,2,3,4,5,6,7, etc. tiles on your PC, all you have to do is to remove Yogynicof virus from the system without a delay. For this purpose, employ a fully-updated anti-virus application, such as SpyHunter 5Combo Cleaner or Malwarebytes. These tools can be infringed by the virus, so if you are not allowed to launch any security tool, restart the machine in Safe Mode.
Upon a full Yogynicof removal from Windows, we recommend running a system scan with Reimage Reimage Cleaner Intego repair tool. This application can help to prevent the system from crashing and encountering errors due to the changes triggered by ransomware. Finally, you can try to recover files encrypted by this ransomware. The below-given guide will help you to apply decryption steps.
The government has many issues in regards to tracking users’ data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Computer users can suffer various losses due to cyber infections or their own faulty doings. Software issues created by malware or direct data loss due to encryption can lead to problems with your device or permanent damage. When you have proper up-to-date backups, you can easily recover after such an incident and get back to work.
It is crucial to create updates to your backups after any changes on the device, so you can get back to the point you were working on when malware changes anything or issues with the device causes data or performance corruption. Rely on such behavior and make file backup your daily or weekly habit.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware occurs out of nowhere. Use Data Recovery Pro for the system restoring purpose.
This entry was posted on 2020-06-17 at 05:27 and is filed under Ransomware, Viruses.