Within just a month of its existence, Zeppelin ransomware was improved and built-up by criminals behind it
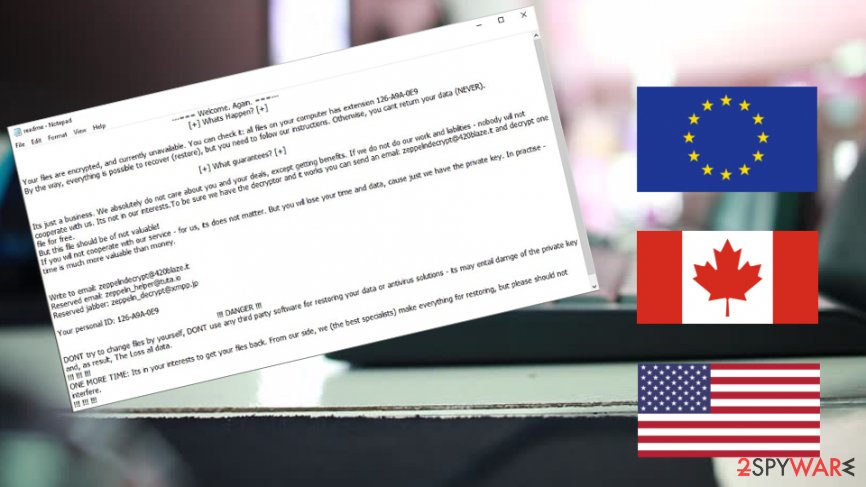
Zeppelin ransomware,[1] a newly developed threat, has been spotted attacking major healthcare and technology organizations worldwide. Victims have been found across Europe, Canada, and the USA. According to Cylance researchers, this malware is known to be Delphi-based RaaS, also recognized as Vega/Vegalocker ransomware.
The first Vegalocker ransomware infections were found at the beginning of 2019 and targeted Russian speakers. Despite being only a bit over a month old, Zeppelin ransomware was altered so much and improved upon Vegalocker, researchers believe that there must be a different criminal group distributing it altogether.
Malware analysis showed that it is designed to stop its execution if it enters a computer system that is located in Russia or other countries that belonged to the USSR block in the past:[2]
In a stark opposition to the Vega campaign, all Zeppelin binaries (as well as some newer Buran samples) are designed to quit if running on machines that are based in Russia and some other ex-USSR countries.
Zeppelin ransomware – a multi-modular ransomware
Cylance claims that the first traces of Zeppelin ransomware were discovered on November 6, 2019, and its primary targets were healthcare and technology companies from all over the globe.[3]
Another interesting trait that was spotted in Zeppelin ransomware was that it had multiple similarities with Sodinokibi ransomware when it comes to its distribution tactics, which include MSSPs (Managed Security Service Providers) in supply-chain attempts,[4] malvertising, as well as targeted waterhole attempts.
Zeppelin ransomware can be deployed via the .exe or a .dll file or utilize a PowerShell loader, although regardless of the method, malware always creates a folder “zeppelin,” where the infection sequence starts from.[5] Afterward, it can launch the following functions:
- Inject specific commands that allow it to boot itself every time the machine is turned on.
- Permanently destroy or delete backups of encrypted data, including Shadow Volume Copies.
- Bypass UAC prompt by launching itself with advanced privileges.
- Track the current location and IP address of the victim.
- Disable processes on the system.
- Unlock data that is found blocked while performing encryption tasks.
- To write a self-elimination command and include it in the notepad.exe process.
- Avoid anti-malware detection by executing specific keys.
The ransom note’s length depends on what type of organization has been targeted
Zeppelin ransomware employs the same encryption cipher as Vegalocker – AES-256 in CBC mode. However, each of the files is then encrypted repeatedly with a custom-built RSA cipher, as claimed by Cylance researchers.
The specialists have also discovered another very interesting fact about Zeppelin ransomware – it locks only the primary 0x1000 bytes (4KB), but not the 0x10000 (65KB). Researchers claim that this function might be a bug included in the malware’s module or intentional action for making the encryption faster.
Zeppelin ransomware can generate various ransom notes, depending on the target it infects. Some messages left by malware authors are brief, while others disclose more details about how to proceed. It is also unknown what is the size of the ransom, although because Zeppelin is targeting corporations, it is highly likely to be a few thousand US dollars at least.
Currently, there is no decryption tool available for the Zeppelin-locked files, making a recovery much more complicated if no backups were prepared prior to the infection. Researchers claim that corporations should be ready for the intrusion of ransom attacks:
The ongoing refinement of ransomware attacks serves as a stark reminder that effective cyber security should be proactive, predictive, adaptive, and semi-autonomous. BlackBerry Cylance researchers aim to keep organizations one step ahead of cyberattacks by sharing threat analysis like this with the public.
