Zwer ransomware – malicious program designed for money extortion
Zwer ransomware is a type of malware that restricts access to personal user files until ransom is paid to cyberiminals

Zwer ransomware is a type of malware that restricts access to personal user files until ransom is paid to cyberiminals
Zwer ransomware is a data locking malware that was developed by sophisticated hackers and is a variant of a malware family known as Djvu. The virus almost exclusively spreads via software cracks and is one of the most popular malware of such type, which targets regular consumers. The main purpose of the infection is to encrypt all music, video, document, picture, and other personal files by appending .zwer extension and preventing access to them.
After the data locking process is complete, Zwer ransomware drops a ransom note called _readme.txt – this file serves as a direct message from the attackers. Inside the note, criminals claim that victims need to pay $490 in Bitcoin in order to recover a unique RSA[1] key to unlock files. For communication purposes, the attackers provide two emails – [email protected] and [email protected].
However, paying criminals is not recommended. There is a chance that Emsisoft’s decryptor might be able to help you restore .zwer encrypted files, although it is only possible if ransomware used an offline ID to lock the data.
| Name | Zwer ransomware |
| Type | File locking virus, crypto-malware |
| Malware family | STOP/Djvu |
| Related files | b71d.tmp.exe |
| Detection |
One of the malicious executables that initiate the infection is detected as follows on Virus Total:
|
| Infection means | Most of Djvu variants are spread via software cracks or pirated program installers downloaded from third-party sources (torrents) |
| File extension | All non-system and non-executable files are appended with .zwer extension. Example of encrypted file: picture.jpg.zwer |
| Ransom note | _readme.txt is delivered into each folders with encrypted files |
| Features | Encrypts all files on the system; modifies Windows hosts file to prevent users’ access to security-focused websites; injects data-stealing module into web browsers; |
| Malware removal | The best way to eliminate the infection is by scanning the computer with powerful security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. Note: you will not be able to open .zwer files after you delete the infection from your computer, as a unique key is required for that |
| System fix | In case your Windows machine begins to crash or display errors after you get rid of the infection, scan it with PC repair software Reimage Reimage Cleaner Intego – it might eliminate virus damage and prevent the reinstallation of the operating system |
| Data recovery | The only secure and 100% effective method to restore .zwer files is by using backups. However, some users might be able to restore files by using Emsisoft’s decryption tool. Additionally, in rare cases, third-party recovery software might be able to help – check for download links and usage instructions below |
Djvu/STOP malware family that the Zwer file virus belongs to is one of the most extensive ones, and so far, over 230 versions were released. Despite this, .kkll, .nlah, .pezi, .covm, and other variants do not differ much, although the attackers tend to use different contact emails for communication purposes most of the time.
Nonetheless, the ransom note _readme.txt is almost identical, and delivers the following information:
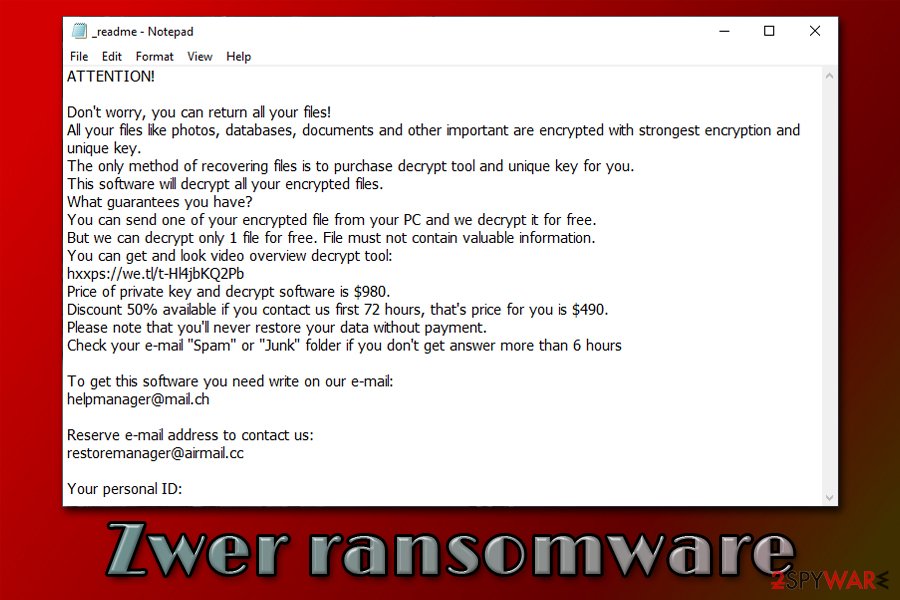
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-Hl4jbKQ2Pb
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hoursTo get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]Your personal ID:
Initially, the attackers are asking for $980 for the Zwer ransomware decryptor, although they promise a 50% discount ($490) if the contact is made within 72 hours of the infection. Besides, they also offer to decipher one of the files that do not include sensitive information. These are all tricks that are meant to create a fake sense of trust within the attackers and make users pay for the Zwer virus file recovery tool. Despite this, there is no guarantee that the attackers will send the unique key, as they might simply scam you by taking the money. The decryption tool might also fail to work in the first place.
While many malware of such type eliminate itself after the data locking process is complete, you should still remove Zwer ransomware with a reputable anti-malware software and only then attempt to recover your files. For malware termination, employ powerful security applications, and then scan the computer with Reimage Reimage Cleaner Intego PC repair application to avoid the Windows reinstallation.
Zwer ransomware is a data locking virus that uses software cracks as a main distribution measure

Zwer ransomware is a data locking virus that uses software cracks as a main distribution measure
Zwer ransomware could install data-stealing module on your machine
Once the malicious file such as b71d.tmp.exe is executed on a Windows machine, it will perform a series or system changes in order to perform a successful file encryption process. For that, the malware creates subfolders inside %AppData%, %User% or %Temp% folder, and then populates malicious files all over the operating system.
After that, Zwer ransomware performs the following changes:
- Deletes Shadow Volume Copies to prevent a quick file recovery
- Opens and modifies Windows registry[2] keys in order to launch with each system boot;
- Creases new and terminates some vital processes;
- Modifies Windows hosts file to prevent users from accessing security-related websites and seeking help with decryption;
- Injects a data stealing module into the web browsers (this feature is especially dangerous, as sensitive information such as credit card details could be stolen by the attackers if Zwer ransomware removal is not performed on time).
As soon as the compromised machine is ready, Zwer ransomware initiates file encryption process and targets the most commonly used types, such as PDF, MS Office, text, archive, and other files. During this development, malware is programmed to deliver users fake Windows update pop-up, as it misleads victims to believe that it is real.
However, as soon as the encryption is finished, users then notice that none of the personal files can be opened anymore, and the ransom note is present on the system, explaining that they have to pay for data recovery.
You can’t open .zwer files: here’s what you should do next
Most people who get infected with file locking malware have never previously had to deal with it. Therefore, it might be a terrifying experience for many, as the invaluable photos, important work, or school documents are no longer available. Users are generally confused about what to do next, as they cannot open .zwer encrypted files.
The correct course of action would be making a full backup of all the encrypted files (if you had backups, you could skip this step) – simply make a copy and place it on the USB stick or another external storage.
Once that is complete, you should then scan the computer with anti-malware software and eliminate the infection. This is were most users believe that anti-malware tools could help then to recover .zwer files, although it could not be far from the truth. Security software is designed to clean the system from malware, and it cannot decrypt data that was locked by ransomware.
To decrypt .zwer files, users can refer to several methods that we provide the instructions for below. Possibly the best chances besides data backups are the Emsisoft’s decryption tool. However, several rules should be met for the recovery process to be successful:
- .zwer files should be encrypted with an offline ID, which means that malware should have failed to contact its remote server. To check if that is the case for you, go to the C: drive on your computer and locate SystemID.txt or PersonalID.txt. Open the file – you should find the list of all the encrypted data IDs. If one of these entries ends with “t1,” an offline ID was used for your files, and it might be recovered with the Emsisoft decryption tool.
- If ransomware has failed to remove Shadow Volume Copies, you can recover files by using Windows Previous Versions feature or System Restore.
- Third-party recovery applications might be able to restore working versions of your files (however, this is not decryption!), as long as you did not use your computer a lot after the infection.
There are very few options that would be successful when trying to open .zwer files

There are very few options that would be successful when trying to open .zwer files
Here’s how ransomware managed to lock your files, and how to prevent it from happening in the future
As mentioned above, Djvu variants are mainly spread via software cracks. These files are used to bypass the licensing process of various applications and are essentially illegal. However, since cracks, keygens, loaders, and similar tools are widely popular, many do not even suspect that some of these could be malicious. Therefore it is highly advisable staying away from files that are download via torrent or similar insecure sites.
Another reason to stop downloading software cracks is that there is simply no way to check whether the file is actually malicious. Cracks, keygens, and similar tools are designed in a way that would break the code of another application. Therefore, even the most advanced security programs are going to flag the item as malicious, regardless if it is infected with malware or not.
Security experts from dieviren.de[3] also advise following these precautionary measures in order to avoid ransomware infections via the third-party websites that host illegal software downloads:
- Employ powerful anti-malware software with real-time detection feature and keep it updated at all times;
- Install ad-blocking browser extension to prevent the execution of background code within malicious ads;
- Pay attention to the file names that you download. For example, malicious actors often obfuscate file names by using double extensions, such as “file.mp4.exe”;
- Before downloading anything, check out user comments;
- Beware of copycat websites that mimic such sites like The Pirate Bay – these are riddled with malware;
- Set Java and Adobe Flash to run on click;
- Make sure all the latest updates are installed on your computer.
Finally, to negate most of the harmful ransomware infection effects, backup your files on a portable storage device or a remote cloud service.
Zwer ransomware removal explained
It is important to understand what type of changes the malware makes to the infected machine in order to remove Zwer ransomware in the correct way. First of all, you should go to the following location and delete the “hosts” file located there:
C:\Windows\System32\drivers\etc\
After that, you should make a full backup of the encrypted files – use something convenient like a USB stick, or upload all the data to a remote server (Google Drive, OneDrive, Dropbox). This will ensure that it will not get corrupted as soon as you perform Zwer ransomware removal. Note that encrypted files are not malicious, as they do not hold any malicious code inside of it.
Next, you should download and install a reputable anti-malware tool and perform a full system scan. In case there issues with the process, access Safe Mode with Networking, as we explain below. Finally, you can attempt the file .zwer file recovery process – we list all the solutions you can try below.
This entry was posted on 2020-06-09 at 03:10 and is filed under Ransomware, Viruses.

